SAML [3] is a standard, which is widely used to deploy Single Sign-On and federation identity solutions. SAML is based on the XML technology, using XML Signatures and X.509 certificates.
Manual testing for SAML vulnerabilities is time consuming and error prone. For example, because a SAML message is only valid for a predefined period of time, the penetration tester potentially needs to be able to manipulate SAML messages within a short time. This is a factor which increases the chance of errors.
Therefore students of the University of Applied Sciences Rapperswil, Switzerland [6] developed an extension [2] for the Burp Suite [1] in collaboration with Compass Security. This extension automates most of the steps, which are necessary to test a SAML environment.
The extension, called “SAML Raider”, supports the penetration tester with the following tasks:
- “Clone” a certificate, i.e. all fields are copied but a random new key-pair is generated.
- Edit certificates and sign them with the arbitrary generated key-pair or with valid keys
- Encode and decode SAML messages
- Display SAML messages with syntax highlighting
- Edit SAML messages manually
- (Re-)sign SAML messages and assertions
- Remove signatures
- Perform XML Signature Wrapping (XSW) attacks
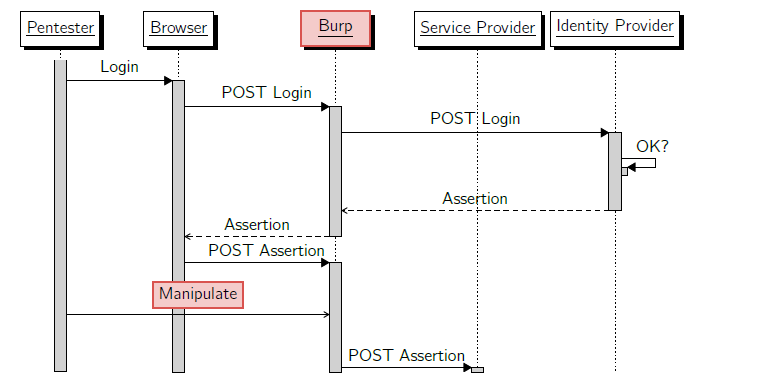
The extension intercepts the POST message with the SAML Assertion, which is received from the Identity Provider (IdP) and is sent from the browser to the Service Provider (SP). The point of manipulation is illustrated in the following flow graph with the red field “Manipulate”.
The following example case illustrates a possible attack, which could be executed with “SAML Raider”. At Hacking-Lab [7] subscribers and license holders can test this vulnerability riskless in a secured environment.
- An attacker can log in as an ordinary user to an Identity Provider and intercepts the SAML assertion before it is sent to the Service Provider.
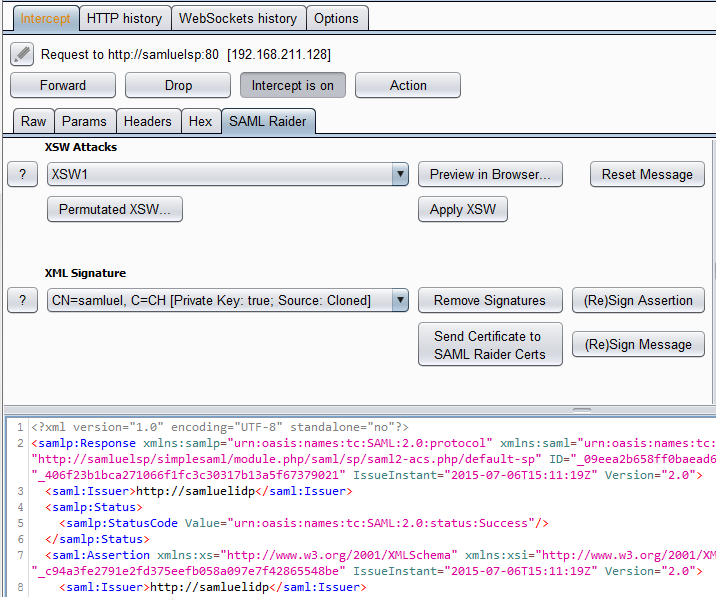
- The attacker now extracts the embedded x509 certificate and clones it.
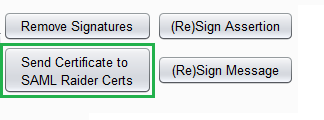
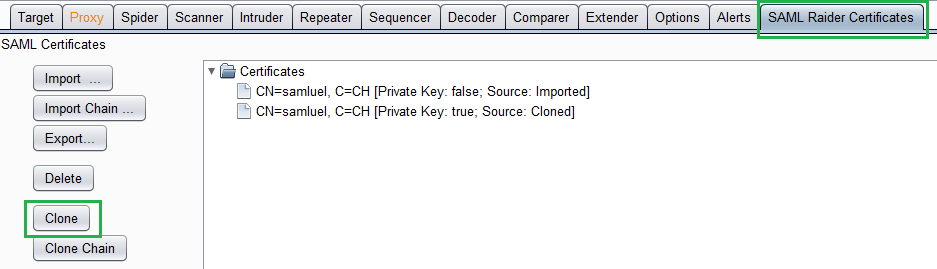
- The attacker changes the user group which is included in the SAML Assertion to administrators.
- The attacker signs the assertion with the cloned certificate and embeds the cloned certificate in the assertion.
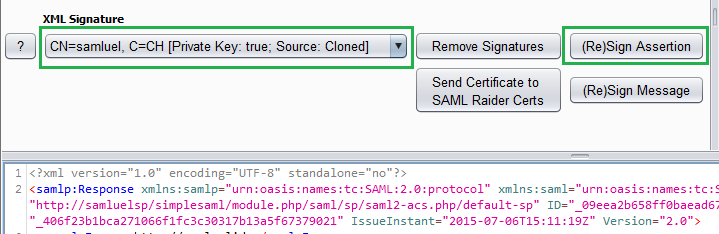
- The attacker sends the manipulated SAML message to the Service Provider.
- The Service Provider wrongly acknowledges the embedded cloned certificate as valid and validates the signature with the wrong certificate.
- The attacker is now logged in as an administrator.
SAML Raider supports the penetration tester in testing SAML Environments with Burp.
There is another Burp extension [4] of the Ruhr University Bochum, which displays Single Sign-On messages and allows to manually edit SAML messages.
At Black Hat 2015 a tool called “samlyze” is announced. Its goal is to pentest SAML service providers fast and easy [5]. We are looking forward and really hope samlyze supplements this extension with one or the other feature.
References:
[1] http://portswigger.net/
[2] https://github.com/SAMLRaider/SAMLRaider
[3] https://www.oasis-open.org/standards#samlv2.0
[4] https://github.com/RUB-NDS/BurpSSOExtension
[5] https://www.blackhat.com/us-15/arsenal.html#samlyze
[6] http://www.hsr.ch/
[7] https://www.hacking-lab.com/
Leave a Reply