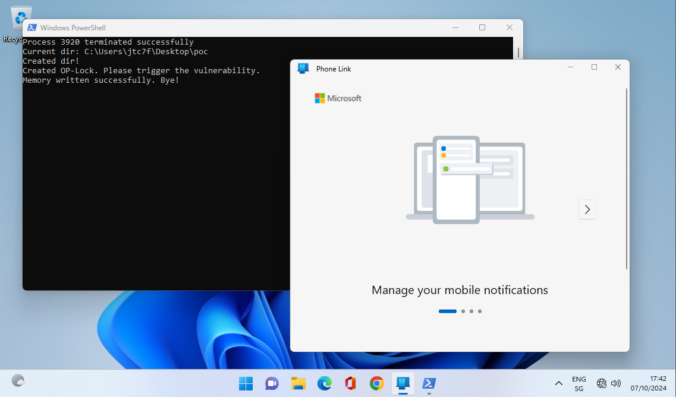
As a pentester you are sometimes thrown into projects where you have no idea where you are going to end up. This project was one of those where you were given a customer laptop and the aim was to “find something interesting”, perhaps a misconfiguration on the customer side. The problem was that the laptop […]
Compass Security Blog
Offensive Defense
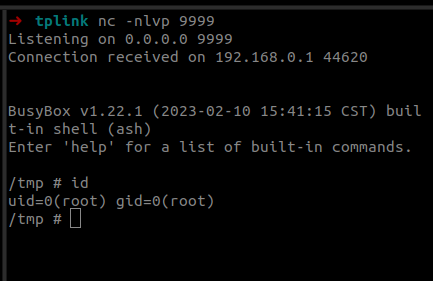
Last year we participated in the Pwn2Own 2023 Toronto competition and successfully exploited the Synology BC500 camera. The DEVCORE Internship Program team managed to exploit a bug in the TP-Link Omada Gigabit VPN Router. So I was naturally curious and wanted to figure out how difficult it would be to recreate that exploit having access only to a high-level bug description and the firmware.
TL;DR An attacker is able to register new security keys (FIDO) or other authentication methods (TOTP, Email, Phone etc.) after a successful device code phishing attack. This allows an attacker to backdoor the account (FIDO) or perform the self-service password reset for the account with the newly registered sign-in methods. Microsoft deemed this not a vulnerability.
Nowadays, web developers rely mostly on well-established frameworks to develop their platform or web sites. These frameworks take care of many vulnerabilities like XSS, SQLi, etc. and give the developers a care-free environment.
However, there is one sneaky weakness that can escape the usual checks quite easily and go undetected: SSRF.
Passwordless products promise greater security and convenience by allowing users to log in to Windows systems with only their smartphone. But what is going on behind the scenes and how could a domain’s security stance be worsened by such a solution? In this post I will explain how these products are implemented and detail the vulnerabilities and weaknesses discovered in three tested products.
ArcGIS [1] is a family of software providing geographic information system services. While testing a customer’s ArcGIS architecture we came across a SAML login flow. In this blogpost we show how we found and exploited an AES-CBC padding oracle in this flow.
During a customer project, we could bypass the biometric authentication mechanism of Ionic Identity Vault on Android, because the Android KeyStore entry does not require any authentication. This post shows how this was done and how it can be exploited.
A little bit over a year ago, I wrote an article on this blog about CVE-2020-1113 and how it enabled to execute code on a remote machine through relaying NTLM authentication over RPC triggering a scheduled task on the remote system. History repeats itself and a vulnerability of the same category has been fixed by Microsoft in June this year.
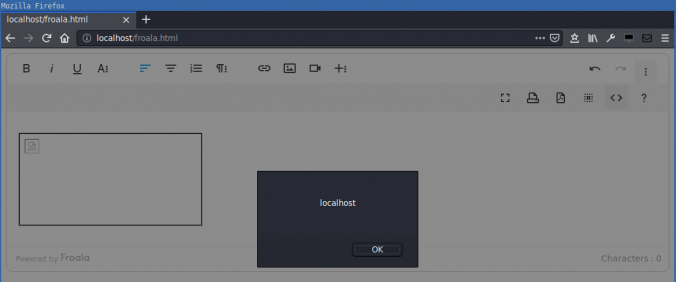
Compass found a DOM-based cross-site scripting (XSS) in the Froala WYSIWYG HTML Editor. HTML code in the editor is not correctly sanitized when inserted into the DOM. This allows an attacker that can control the editor content to execute arbitrary JavaScript in the context of the victim’s session.
SharePoint is a very popular browser-based collaboration and content management platform. Due to its high complexity, proprietary technology and confusing terminology it is often perceived as a black-box that IT and security professionals do not feel very comfortable with. These days, web security topics are well understood by many security professionals, penetration testers and vendors. But what […]
© 2025 Compass Security Blog