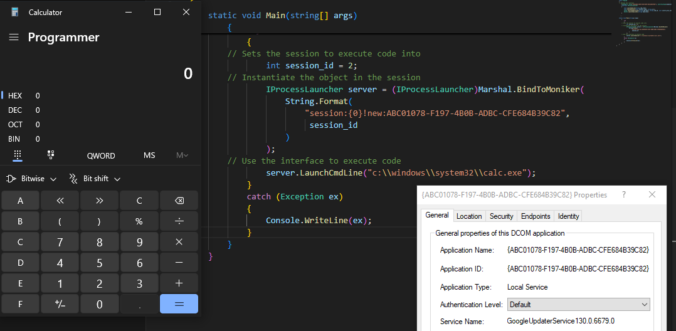
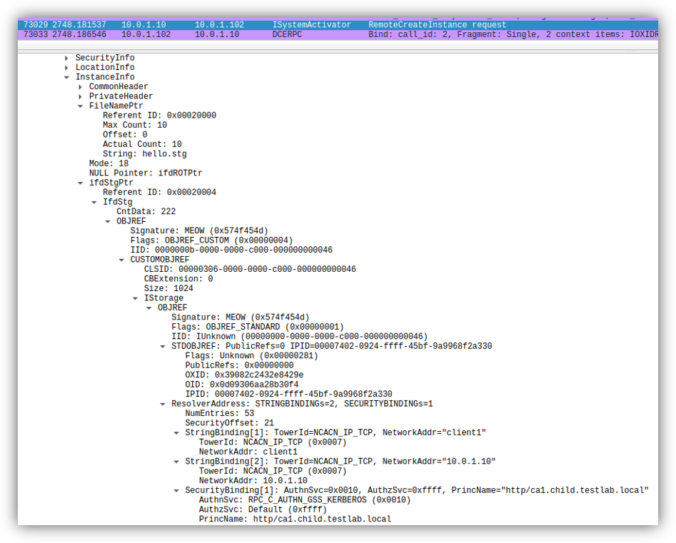
Once again, reading blogs and tweets from James Forshaw led me to wonder how things work. This time, I was working on DCOM for my last blog post and while reading about cross-session activation, I had trouble believing what I was reading.
Compass Security Blog
Offensive Defense
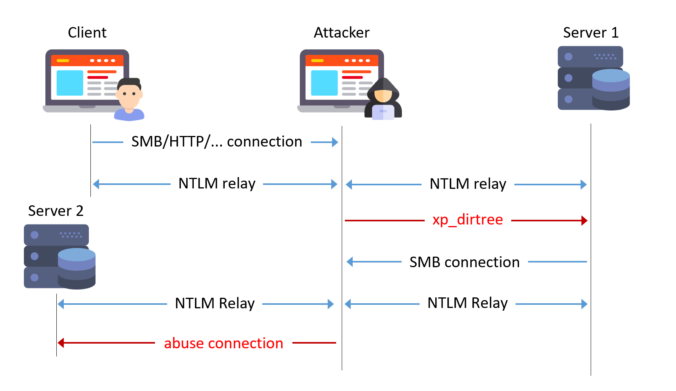
Earlier this year, several security researchers published research about using DCOM to coerce Windows systems to authenticate to other systems. This can be misused to relay the authentication to NTLM or Kerberos, to AD CS over HTTP for instance. This sounds like a hot and complex topic. Let’s take a look back how this started […]
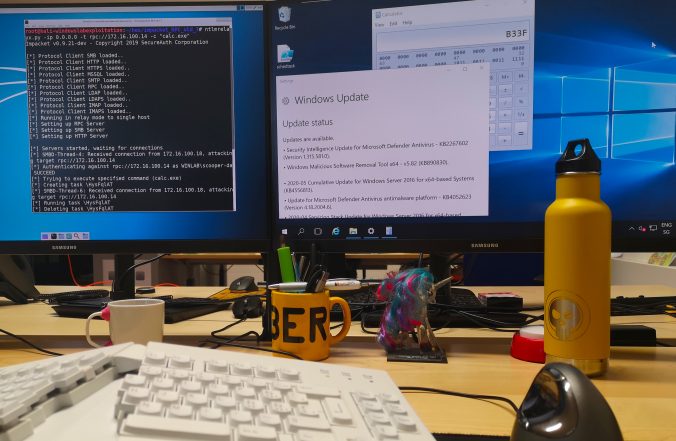
Readers of this blog probably know that I like to try NTLM relaying over all protocols possible! Relaying to Microsoft SQL (MSSQL) is known to work when using the default weak configuration.
With this blog post, we show some dangerous configurations and release a small tool to automate NTLM relaying in these cases.
Sometimes, the good old credential dumping techniques just won’t work. This is the story of how a bad actor could dump credentials on a fully-patched, monitored and hardened workstation.
Red Teaming exercises are getting popular with the growth of security operations centers. These attack simulations aim to help companies improve their defenses and train the blue team. But solid foundations are necessary to get the most of such an exercise.
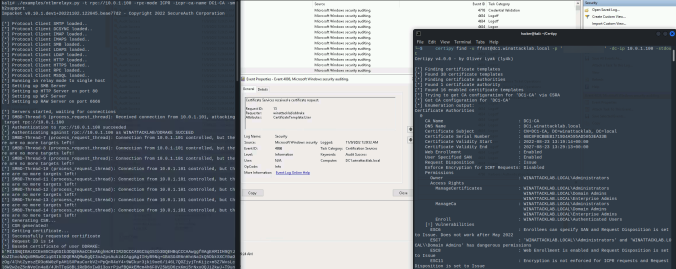
In June last year, the good folks at SpecterOps dropped awesome research on Active Directory Certificate Services (AD CS) misconfigurations. Since then, we find and report these critical vulnerabilities at our customers regularly. One of these new attack path is relaying NTLM authentication to unprotected HTTP endpoints. This allows an attacker to get a valid […]
More and more companies use Microsoft 365, well even we at Compass-Security use it internally. Moving to the cloud solves many issues that our DFIR team had to deal with in the past years. Managed infrastructure means no ProxyShell, Hafnium, etc. We’re grateful for that.
Email authentication and security is another complex topic that was often misconfigured in the past. We often could send phishing email in the name of our clients during assessments. Office 365 makes the life of scammers and phishers somehow harder. We’re also grateful for that.
However we still encounter some O365 environments where it’s possible to send spoofed emails. Why is that, you ask? We also wondered and dug into the O365 features and settings!
A little bit over a year ago, I wrote an article on this blog about CVE-2020-1113 and how it enabled to execute code on a remote machine through relaying NTLM authentication over RPC triggering a scheduled task on the remote system. History repeats itself and a vulnerability of the same category has been fixed by Microsoft in June this year.
Since a few years, we – as pentesters – (and probably bad guys as well) make use of NTLM relaying a lot for privilege escalation in Windows networks.
In this article, we propose adding support for the RPC protocol to the already great ntlmrelayx from impacket and explore the new ways of compromise that it offers.
This vulnerability was discovered by Compass Security in January 2020, disclosed to Microsoft Security Response Center and assigned CVE-2020-1113 as identifier.
As a defender, you want to find and patch attack paths in your Active Directory environment. One cannot easily spot issues by looking at the Active Directory Users and Computers console, GPOs, etc. but here comes BLOODHOUND.
© 2024 Compass Security Blog