In this blog article, we would like to share key insights from the “Defeating Microsoft’s Default BitLocker Implementation” security training by Hands-On Security and emphasize the potential risks and consequences associated with this attack technique. Our target audience includes businesses looking to safeguard sensitive data on their Windows devices, as well as individuals with an elevated requirement for protecting their data.
Compass Security Blog
Offensive Defense
When accessing a remote server, one should always assume it has been compromised or might be in the near future. It is particularly crucial for users with administrative privileges to establish a secure connection to the Remote Desktop Protocol (RDP) service in order to not fall victim to credential theft or impersonation. To achieve this, there exist several measures in Windows. In this blog post, we’ll look at some of them, their benefits and their drawbacks.
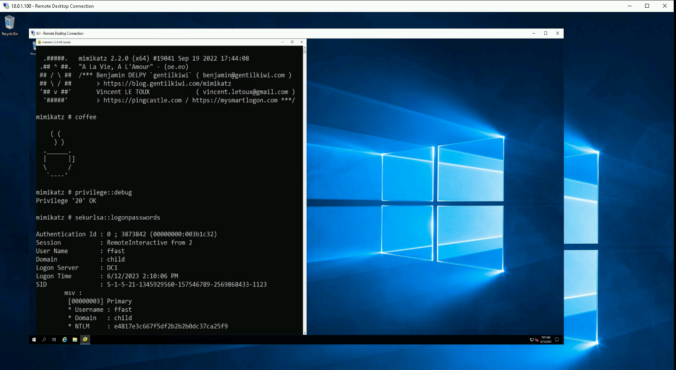
Sometimes, the good old credential dumping techniques just won’t work. This is the story of how a bad actor could dump credentials on a fully-patched, monitored and hardened workstation.
The ntds.dit file from a domain controller contains all password hashes of the domain. In a company with employees around the globe we were allowed to analyze the hashes. Here are the results, and the reason why you should implement a banned password list.
BloodHound is the way to go to for finding attack paths in an Active Directory (AD) environment. However, it is not always clear how the data is gathered without looking at the code of SharpHound, the data ingestor for BloodHound. Microsoft hardened their systems over time through updates, which makes enumeration of Active Directory (AD) […]
BloodHound is the way to go to for finding attack paths in an Active Directory (AD) environment. However, it is not always clear how the data is gathered without looking at the code of SharpHound, the data ingestor for BloodHound. Microsoft hardened their systems over time through updates, which makes enumeration of Active Directory (AD) […]
BloodHound is the way to go to for finding attack paths in an Active Directory (AD) environment. However, it is not always clear how the data is gathered without looking at the code of SharpHound, the data ingestor for BloodHound. Microsoft hardened their systems over time through updates, which makes enumeration of Active Directory (AD) […]
A little bit over a year ago, I wrote an article on this blog about CVE-2020-1113 and how it enabled to execute code on a remote machine through relaying NTLM authentication over RPC triggering a scheduled task on the remote system. History repeats itself and a vulnerability of the same category has been fixed by Microsoft in June this year.
Due to recent developments we figured it would be great to contribute a cheat sheet and create security best-practices on how to tie down a Microsoft on-prem environment. Our work mostly relies on MS recommendations. However, we put some effort to really condense it to the essence. We hope to see this applied everywhere and thus open-sourced everything in our GitHub repository.
A post on how to trick browsers to work as a gateway to internal web servers and IoT devices, the concepts behind and how to easily exploit DNS rebinding using the Singularity of Origin framework.
© 2025 Compass Security Blog