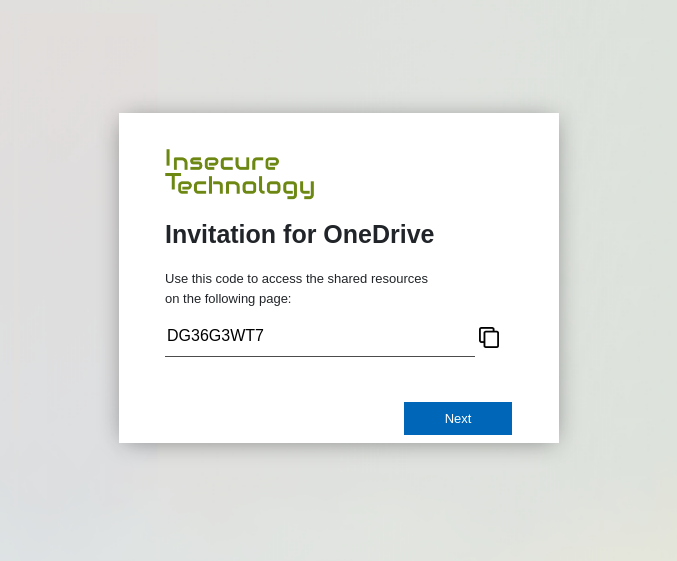
Device code phishing is nothing new. In fact it has been around for some years now. Despite the awesome capabilities of device code phishing, it is not widely used by threat actors. Therefore, it probably does not receive much attention from Microsoft. Compass Security is releasing two tools that can work hand in hand in a device code phishing exercise or even your next red team engagement.
Compass Security Blog
Offensive Defense
Introduction Last Friday and Saturday (15./16. June 2018), the 6th edition of the security conference Area41 (formerly Hashdays, https://area41.io/) organized by DEFCON Switzerland (https://www.defcon-switzerland.org/, https://twitter.com/defconCH) took place in Zürich. Every Compass security analyst can attend two conferences every year supported by Compass. So most of the analysts decided to go to the Area41 this year […]
As every year, some Compass Security Analysts travelled to Geneva and attended the Insomni’hack conference and it’s enjoyable CTF.
This year again a small delegation of Compass Security was present at Insomni’hack in Geneva. On the novelties this year, the workshops spanned over two days (Tuesday and Wednesday) and the conference followed the same direction (Thursday and Friday). There was also a new kind of CTF, labeled blue-team CTF, called Boss of the SOC. […]
The BlackAlps 2017 security conference took place this week in Yverdon-les-Bains: https://www.blackalps.ch. A small delegation of Compass Security was here to present a web application security workshop and also take part in the Y-NOT-CTF. You’ll find below a write-up of the challenges we were able to solve. Fun : Beautiful Alps This was probably the […]
Recently our analysts have been spending increasing amounts of time on IoT security. More specifically looking at the Tensilica Xtensa microcontroller architecture, and even more specifically at the Mongoose OS embedded operating system. With some public (CVE-2017-7185), and some not yet disclosed advisories (watch this space for Dobin Rutishauser’s work), we are happy to announce that […]
Last Friday a little more than a dozen Compass Security Analysts traveled to Geneva and attended the Insomnihack conference and its CTF. Conference The conference featured a variety of topics, ranging from areas such as corporate IT security, distributed systems and malware analysis, or even unusual topics such as remote exploitation of game engines. DevOOPS: Attacks […]
What is CodeMash? CodeMash is a conference for software developers and IT security professionals. It takes place every year in Sandusky, Ohio, in the U.S. The event consists of two parts: two days of training sessions (called “PreCompiler”), followed by two days of conference with sessions. It attracts about 3’000 visitors and takes place in […]
At the beginning of August, as every year, two of our security analysts attended the most renowned IT security conferences Black Hat USA and DEF CON to learn about the latest trends and research. This year’s Black Hat conference, the 19th edition, took place at the Mandalay Bay Conference Center while DEF CON 24 was located […]
For the second part of our report about Black Hat USA 2015, we decided to change topic, and switch from web application security to two hot topics nowadays: Security in Internet of Things and mobile security. We encourage you not only to read this summary but also to go online and take a closer look […]
© 2025 Compass Security Blog