Microsoft Azure is probably the most widely used cloud platform in Switzerland, powering businesses of all sizes, from startups to multinational companies. According the the official Microsoft page over 95% of Fortune 500 companies rely on Microsoft Azure in one form or another. With this industry-wide adoption, it has become a critical component of modern-day […]
Compass Security Blog
Offensive Defense
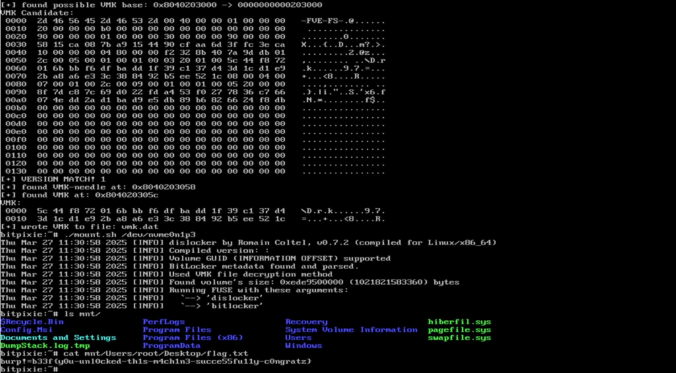
Depending on the customer’s preference, possible initial access vectors in our red teaming exercises typically include deployment of dropboxes, (device code) phishing or a stolen portable device. The latter is usually a Windows laptop protected by BitLocker for full disk encryption without pre-boot authentication i.e. without a configured PIN or an additional key file. While […]
This blog post introduces our new custom queries for BloodHound Community Edition (CE) and explains how you can use them effectively to analyze your Active Directory infrastructure. TL;DR: Check out our new BloodHound CE custom queries! Active Directory and BloodHound The majority of our customers run a Microsoft Active Directory infrastructure, either exclusively on-prem or […]
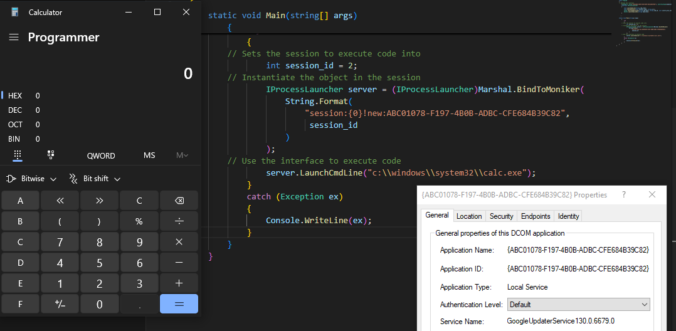
Once again, reading blogs and tweets from James Forshaw led me to wonder how things work. This time, I was working on DCOM for my last blog post and while reading about cross-session activation, I had trouble believing what I was reading.
In this blog article, we would like to share key insights from the “Defeating Microsoft’s Default BitLocker Implementation” security training by Hands-On Security and emphasize the potential risks and consequences associated with this attack technique. Our target audience includes businesses looking to safeguard sensitive data on their Windows devices, as well as individuals with an elevated requirement for protecting their data.
TL;DR An attacker is able to register new security keys (FIDO) or other authentication methods (TOTP, Email, Phone etc.) after a successful device code phishing attack. This allows an attacker to backdoor the account (FIDO) or perform the self-service password reset for the account with the newly registered sign-in methods. Microsoft deemed this not a vulnerability.
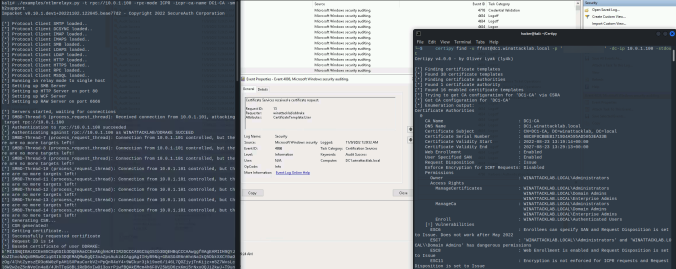
In June last year, the good folks at SpecterOps dropped awesome research on Active Directory Certificate Services (AD CS) misconfigurations. Since then, we find and report these critical vulnerabilities at our customers regularly. One of these new attack path is relaying NTLM authentication to unprotected HTTP endpoints. This allows an attacker to get a valid […]
More and more companies use Microsoft 365, well even we at Compass-Security use it internally. Moving to the cloud solves many issues that our DFIR team had to deal with in the past years. Managed infrastructure means no ProxyShell, Hafnium, etc. We’re grateful for that.
Email authentication and security is another complex topic that was often misconfigured in the past. We often could send phishing email in the name of our clients during assessments. Office 365 makes the life of scammers and phishers somehow harder. We’re also grateful for that.
However we still encounter some O365 environments where it’s possible to send spoofed emails. Why is that, you ask? We also wondered and dug into the O365 features and settings!
A little bit over a year ago, I wrote an article on this blog about CVE-2020-1113 and how it enabled to execute code on a remote machine through relaying NTLM authentication over RPC triggering a scheduled task on the remote system. History repeats itself and a vulnerability of the same category has been fixed by Microsoft in June this year.
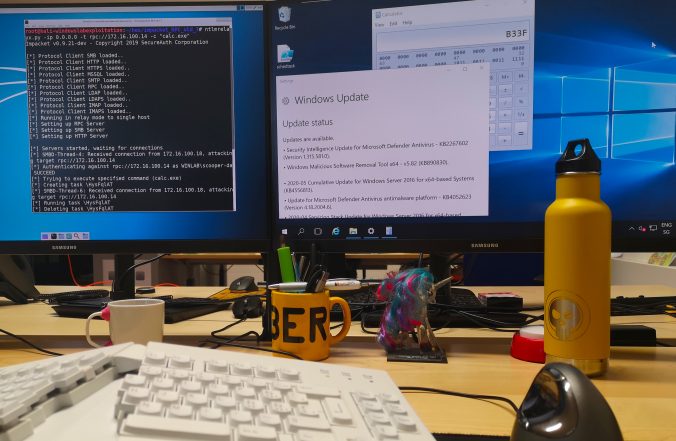
Since a few years, we – as pentesters – (and probably bad guys as well) make use of NTLM relaying a lot for privilege escalation in Windows networks.
In this article, we propose adding support for the RPC protocol to the already great ntlmrelayx from impacket and explore the new ways of compromise that it offers.
This vulnerability was discovered by Compass Security in January 2020, disclosed to Microsoft Security Response Center and assigned CVE-2020-1113 as identifier.
© 2025 Compass Security Blog