Introduction As you may know, Compass Security participated in the 2023 edition of the Pwn2Own contest in Toronto and was able to successfully compromise the Synology BC500 camera using a remote code execution vulnerability. If you missed this, head over to the blog post here https://blog.compass-security.com/2024/03/pwn2own-toronto-2023-part-1-how-it-all-started/ Unfortunately, the same vulnerability was also identified by other […]
Compass Security Blog
Offensive Defense
Depending on the customer’s preference, possible initial access vectors in our red teaming exercises typically include deployment of dropboxes, (device code) phishing or a stolen portable device. The latter is usually a Windows laptop protected by BitLocker for full disk encryption without pre-boot authentication i.e. without a configured PIN or an additional key file. While […]
Last year we participated in the Pwn2Own 2023 Toronto competition and successfully exploited the Synology BC500 camera. The DEVCORE Internship Program team managed to exploit a bug in the TP-Link Omada Gigabit VPN Router. So I was naturally curious and wanted to figure out how difficult it would be to recreate that exploit having access only to a high-level bug description and the firmware.
To identify and understand threats and weaknesses of smart contracts, it is important to be at least familiar with common smart contract bugs and vulnerabilities, how they can be leveraged by a malicious attacker, and how these issues can be mitigated.
This blog article aims to raise awareness about common smart contract vulnerabilities and their corresponding mitigation strategies.
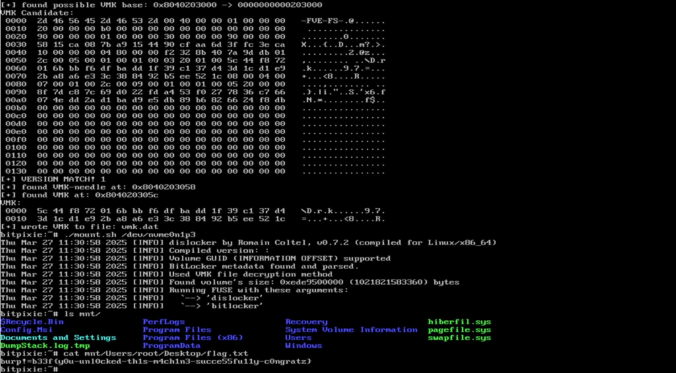
In this final part of this series, we are finally going to explain how the stack-based buffer overflow vulnerability can be exploited to gain unauthenticated remote code execution (RCE) on the Synology BC500 camera.
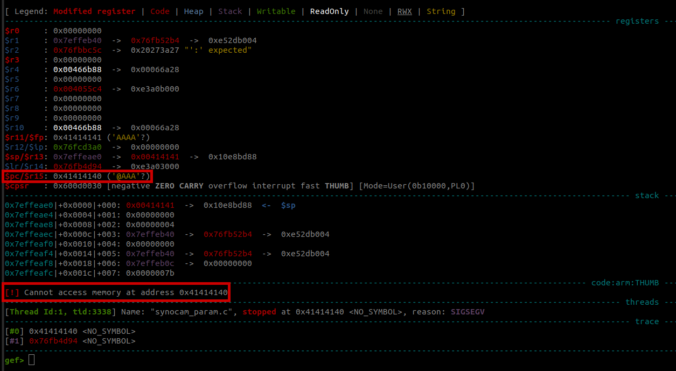
In this fourth part of the series, we analyze the memory corruption identified previously and manage to overwrite the program pointer!
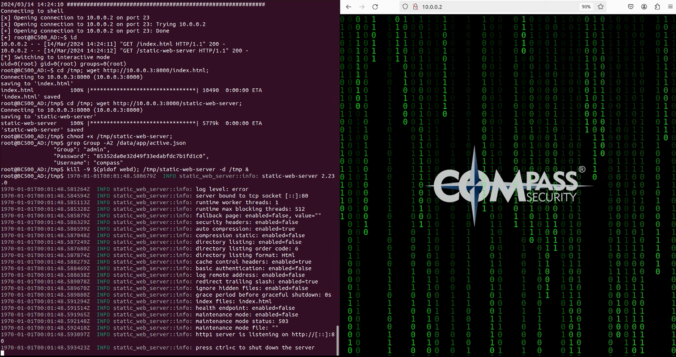
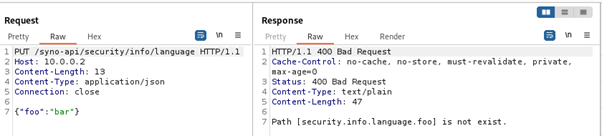
In this third part of the series, we focus on the exposed web services running on TCP ports 80 and 443.
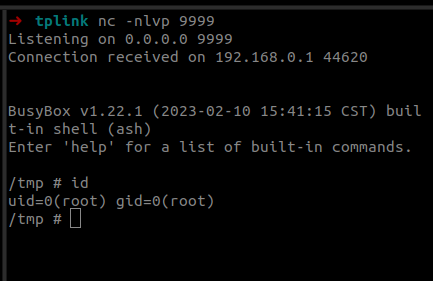
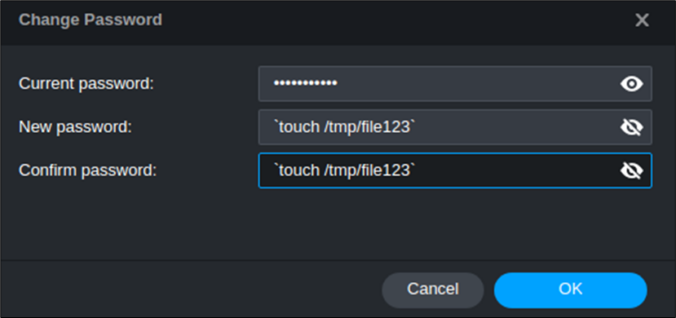
Since a valid exploit chain must achieve code execution without prior authentication, we focus on the available functionality that can be accessed without authentication.
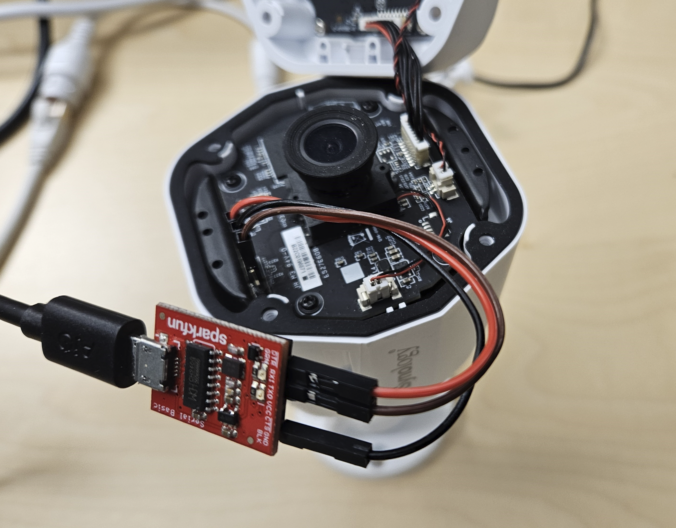
In this second blog post of the series, we start with the reconnaissance phase on the camera, a crucial step in understanding our target.
The aim here is to gather information about the target and identify potential vulnerabilities.
Around a year ago a few Compass analysts watched a talk at the Insomni’Hack conference about the Pwn2Own contest.
This is when they decided to take part! In this blog post, they talk about how they picked their target, got the firmware from the camera, and got into the shell.
In today’s interconnected world, it is a well-known fact that systems with Internet exposure are under continual threat of cyber-attacks. This risk extends from private websites to corporate infrastructure. With the increasing modernization of Industrial Control Systems (ICS), these vital components also become more exposed to such threats. But what is the extent and nature […]
© 2025 Compass Security Blog