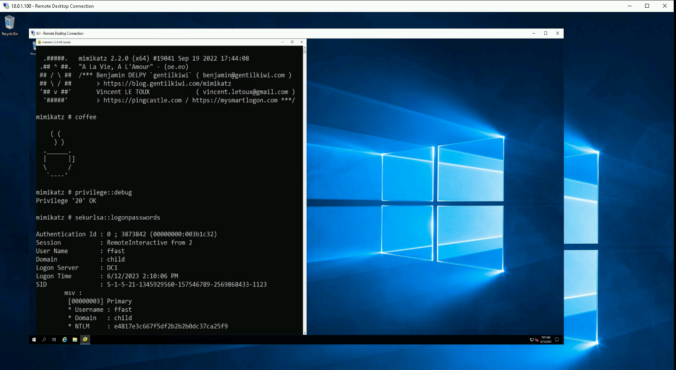
When accessing a remote server, one should always assume it has been compromised or might be in the near future. It is particularly crucial for users with administrative privileges to establish a secure connection to the Remote Desktop Protocol (RDP) service in order to not fall victim to credential theft or impersonation. To achieve this, there exist several measures in Windows. In this blog post, we’ll look at some of them, their benefits and their drawbacks.
Compass Security Blog
Offensive Defense
SharePoint is a very popular browser-based collaboration and content management platform. Due to its high complexity, proprietary technology and confusing terminology it is often perceived as a black-box that IT and security professionals do not feel very comfortable with. These days, web security topics are well understood by many security professionals, penetration testers and vendors. But what […]
Opening up an internal SharePoint farm to the Internet in order to share resources with external parties might seem a good idea, because it helps avoiding expensive infrastructure changes. However, in terms of security, this is not recommended because it does not sufficiently protect internal resources from external threats. The protection of internal resources hinges […]
What is a Hack-Lab? Compass Security provides a monthly playful occasion for the security analysts to get-together and try to hack new devices, dive into current technologies and share their skills with their fellows. This also includes the improvement of internal tools, the research of newly identified publicly known attacks, and security analysis of hardware […]
Introduction It can be very tricky to analyze the relevant service account and its file system permissions in order to evaluate if a compromised ASP.NET application can access sensitive resources (file system / network / processes) on the web server. Especially from IIS 6 to IIS 7.5 there is quite a big change in how […]
The following article describes common security issues regarding misconfigured sudoers’ files. The article focuses on a single entry which contains several security issues: hacker10 ALL= (root) /bin/less /var/log/* The article is split into the following five chapters: PART 1: Command Execution PART 2: Insecure Functionality PART 3: Permissions PART 4: Wildcards PART 5: Recapitulation Define […]
The following article describes common security issues regarding misconfigured sudoers’ files. The article focuses on a single entry which contains several security issues: hacker10 ALL= (root) /bin/less /var/log/* The article is split into the following five chapters: PART 1: Command Execution PART 2: Insecure Functionality PART 3: Permissions PART 4: Wildcards PART 5: Recapitulation The last […]
The following article describes common security issues regarding misconfigured sudoers’ files. The article focuses on a single entry which contains several security issues: hacker10 ALL= (root) /bin/less /var/log/* The article is split into the following five chapters: PART 1: Command Execution PART 2: Insecure Functionality PART 3: Permissions PART 4: Wildcards PART 5: Recapitulation Another pitfall […]
The following article describes common security issues regarding misconfigured sudoers’ files. The article focuses on a single entry which contains several security issues: hacker10 ALL= (root) /bin/less /var/log/* The article is split into the following five chapters: PART 1: Command Execution PART 2: Insecure Functionality PART 3: Permissions PART 4: Wildcards PART 5: Recapitulation In this […]
The following article describes common security issues regarding misconfigured sudoers’ files. The article focuses on a single entry which contains several security issues: hacker10 ALL= (root) /bin/less /var/log/* The article is split into the following five chapters: PART 1: Command Execution PART 2: Insecure Functionality PART 3: Permissions PART 4: Wildcards PART 5: Recapitulation In this […]
© 2025 Compass Security Blog