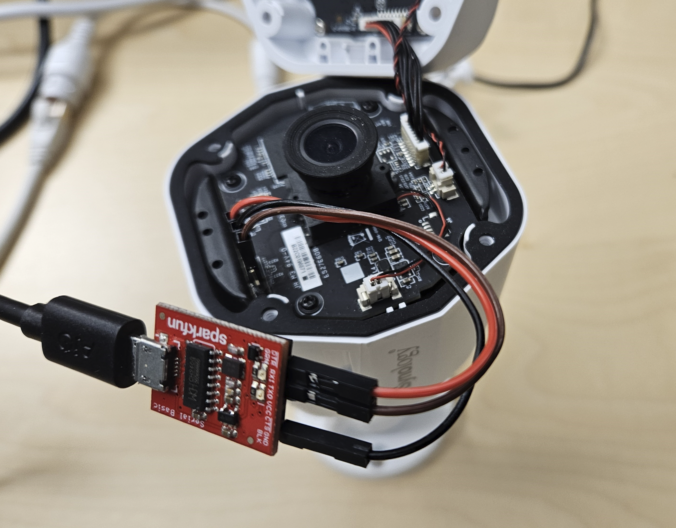
In this final part of this series, we are finally going to explain how the stack-based buffer overflow vulnerability can be exploited to gain unauthenticated remote code execution (RCE) on the Synology BC500 camera.
Compass Security Blog
Offensive Defense
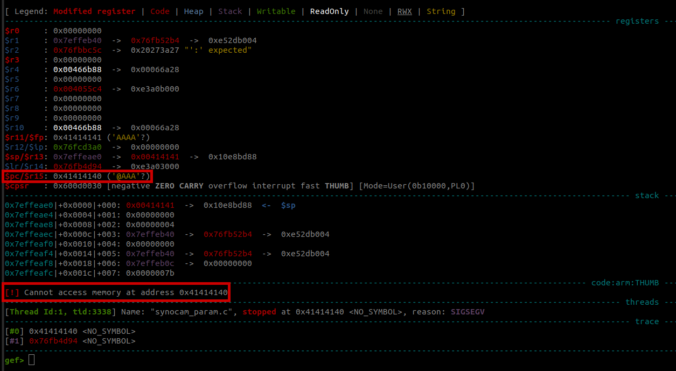
In this fourth part of the series, we analyze the memory corruption identified previously and manage to overwrite the program pointer!
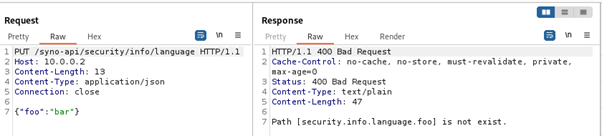
In this third part of the series, we focus on the exposed web services running on TCP ports 80 and 443.
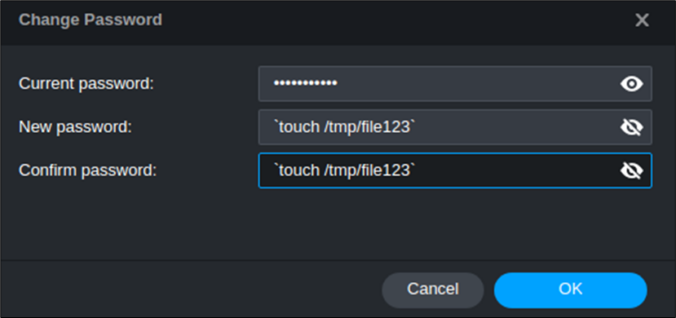
Since a valid exploit chain must achieve code execution without prior authentication, we focus on the available functionality that can be accessed without authentication.
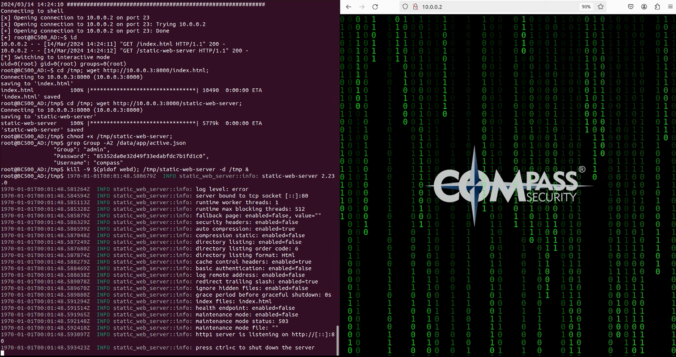
In this second blog post of the series, we start with the reconnaissance phase on the camera, a crucial step in understanding our target.
The aim here is to gather information about the target and identify potential vulnerabilities.
Around a year ago a few Compass analysts watched a talk at the Insomni’Hack conference about the Pwn2Own contest.
This is when they decided to take part! In this blog post, they talk about how they picked their target, got the firmware from the camera, and got into the shell.
© 2024 Compass Security Blog