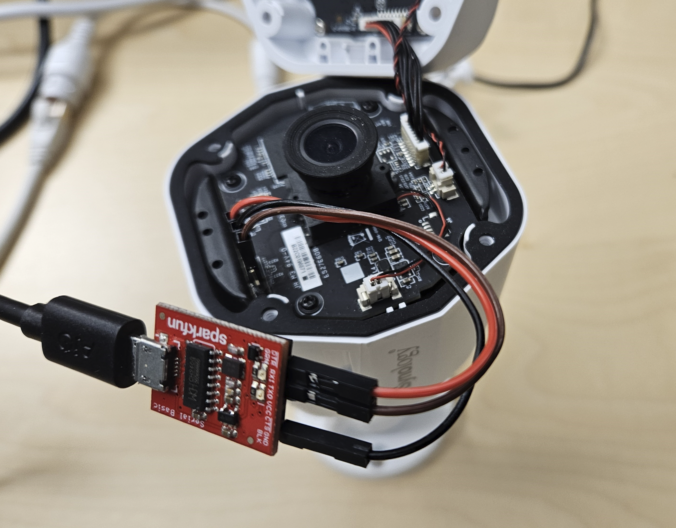
Around a year ago a few Compass analysts watched a talk at the Insomni’Hack conference about the Pwn2Own contest.
This is when they decided to take part! In this blog post, they talk about how they picked their target, got the firmware from the camera, and got into the shell.