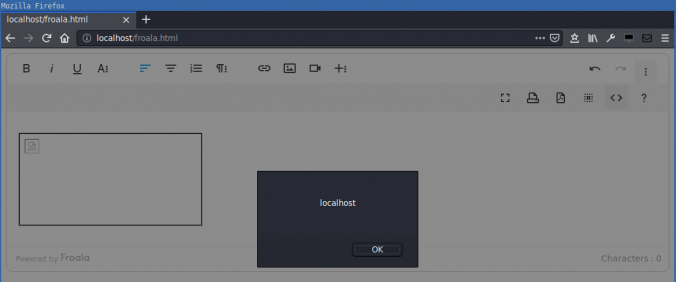
Compass found a DOM-based cross-site scripting (XSS) in the Froala WYSIWYG HTML Editor. HTML code in the editor is not correctly sanitized when inserted into the DOM. This allows an attacker that can control the editor content to execute arbitrary JavaScript in the context of the victim’s session.
Compass Security Blog
Offensive Defense
In my free time, I like to do some bug bounty hunting. For some reasons, I’ve been doing this almost exclusively for Swisscom. One of the reason is that the scope is very broad and I like to have this vast landscape full of possibilities. While preparing the talk we had at BlackAlps (https://www.blackalps.ch) with […]
SharePoint is a very popular browser-based collaboration and content management platform. Due to its high complexity, proprietary technology and confusing terminology it is often perceived as a black-box that IT and security professionals do not feel very comfortable with. These days, web security topics are well understood by many security professionals, penetration testers and vendors. But what […]
Opening up an internal SharePoint farm to the Internet in order to share resources with external parties might seem a good idea, because it helps avoiding expensive infrastructure changes. However, in terms of security, this is not recommended because it does not sufficiently protect internal resources from external threats. The protection of internal resources hinges […]
What is a Hack-Lab? Compass Security provides a monthly playful occasion for the security analysts to get-together and try to hack new devices, dive into current technologies and share their skills with their fellows. This also includes the improvement of internal tools, the research of newly identified publicly known attacks, and security analysis of hardware […]
Compass Security employees identify and report on a regular basis security vulnerabilities as part of their daily assessments (or just out curiosity). Stefan Horlacher identified and reported back in June 2013 several flaws in SAP BusinessObjects Explorer. We’re happy to publish today the details as the flaws have been patched and a reasonable grace period […]
Cross-Site Scripting (XSS) has lost one rank in the newly released OWASP Top Ten 2013 candidate. Compared to the 2010 version, it’s now on rank three, overtaken by “Broken Authentication and Session Management”. Has XSS become less common then? No, I don’t think so. Compass Security has always been strong in web application security testing […]
Introduction Several native JavaScript functions or properties like .eval() and .innerHTML as well as several jQuery functions like .html() and .append() are considered as “unsafe”, but why? The reason is that they allow DOM manipulation using strings containing HTML code (e.g.”<b>This text is bold</b>“), which can lead to DOM Based Cross-Site Scripting vulnerabilities. To be […]
The community hosts a neat little project called AntiSamy[1] which lends its name from the well known MySpace worm[2] and which comes in handy when trying to mitigate Cross-site Scripting[3] attacks. Whereby XSS is sometimes hard to mitigate when business is asking for HTML formatting in user supplied inputs. At that point, AntiSamy might become […]
Today, Compass Security published a public advisory regarding nevisProxy, a product from AdNovum, used by several Swiss financial institutions. nevisProxy is a secure reverse proxy with an integrated web application firewall (WAF). It acts as a central upstream entry point for web traffic to integrated online applications. nevisProxy controls user access and protects sensitive data, […]
© 2025 Compass Security Blog