With the rise of remote working, Microsoft Teams has become the de-facto standard for video conferences, chat, and collaboration. The nature of the Teams architecture are some central systems that route information between parties. With that comes that Teams client software must be allowed to communicate to the Internet. Microsoft even recommends letting Teams traffic bypass inspection proxies for compatibility reasons. Its network communication pattern has significant overlap with malicious C2 traffic und thus it is nearly impossible for blue teams to spot adversary communication. Therefore, Teams is an interesting candidate to be abuses for C2 traffic. Thus, we put some research into this.
Compass Security Blog
Offensive Defense
The anonymous data on our cases allows us to answer the question “What is a typical DFIR case at Compass Security?” and we conclude its the analysis, containment, eradication and recovery of one or a few devices in a Windows domain which is probably no surprise :)
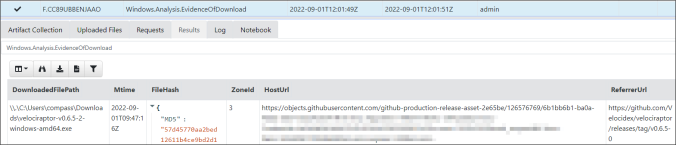
This post provides ideas of processes to follow and gives basic guidance on how to collect, triage and analyze artifacts using Velociraptor
Agile software development models have become the de-facto standard. They are taught at universities and implemented in practice as far as possible. Anyone who doesn’t develop software using agile processes is on the verge, and already tilting towards that. At least that is how it seems. Consequently, the question is not whether the integration of […]
The article discusses the very basics to keep systems ready for analysis of lateral movement. We present some guidelines in form of a cheat sheet and a tool (Readinizer) that you can run, to ensure that everything is set up as in the guidelines provided.
Black box analysis of a not so smart card in ID-1 form factor that is in use for the billing of washing machines and tumble driers.
This post is intended to explain what you typically want to check for during an OpenID Connect assessment and also provide you with a guide to setup your own OpenID Connect test environment.
Present State of Affairs We have been teaching forensics and network incident analysis for quite a while. We have investigated into a reputable number of cases and we are not the only doing so. Hence, one would expect a certain degree of automation in analysis. However, the high frequency of software release cycles somehow leads […]
Dieser Blog Post dient als Hintergrundartikel zum SRF Thementag «Blackout»: Wenn die Schweiz plötzlich keinen Strom mehr hätte vom Montag, 2. Januar 2017, 13.00 bis 22.00 Uhr (SRF News, SRF Kultur Wissen Beitrag) Wie ist die Vorgehensweisen von Hackern, die unerlaubten Zugriff auf fremde Systeme erlangen wollen? — beispielsweise im Netzwerk eines Energieversorgungsunternehmens. Basierend auf diesen […]
This post will give a quick intro into software defined radio (SDR) basics and provide guidance for the decoding of a very simple form of digital modulation (on-off keying). Device Wireless Specs Wireless junk hacking is not too difficult. Usually, devices transceive in the 433MHz or 868MHz ISM radio bands. As these bands are somewhat lax […]
© 2025 Compass Security Blog