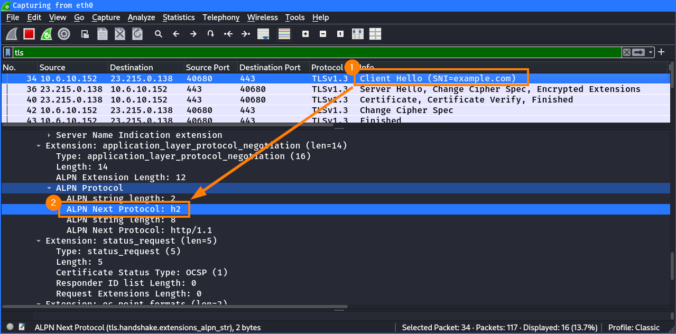
In the previous posts of this series, we looked at different ways to bypass web filters, such as Host header spoofing and domain fronting. As we’ve learned, these techniques can be detected by proxies employing TLS inspection, by checking whether the hostname in the SNI matches the one in the HTTP Host header. If they […]
Compass Security Blog
Offensive Defense
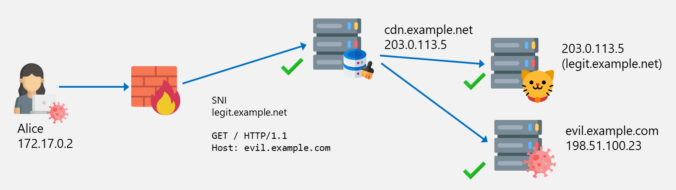
The last two blog posts in this series were about SNI spoofing and Host header spoofing. We also learned that the latter is addressed by some vendors with a technique called “Domain Fronting Detection”. But what exactly is domain fronting? This will be explained in this blog post.
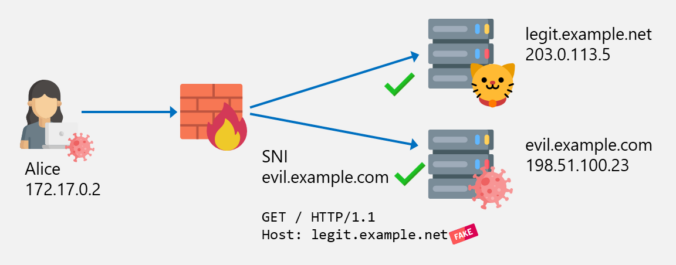
In the last post about bypassing web filters, I discussed how SNI spoofing works and how this can also be prevented by web filters. This post is about another bypass technique called Host Header spoofing.
This is the first part of a series of blog posts about techniques to bypass web filters, looking at increasingly advanced techniques with each part.
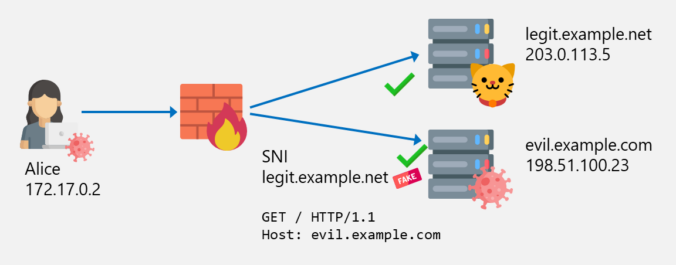
The first part is about how SNI spoofing can be used to bypass web filters.
This blog post introduces our new custom queries for BloodHound Community Edition (CE) and explains how you can use them effectively to analyze your Active Directory infrastructure. TL;DR: Check out our new BloodHound CE custom queries! Active Directory and BloodHound The majority of our customers run a Microsoft Active Directory infrastructure, either exclusively on-prem or […]
During a customer project, we could bypass the biometric authentication mechanism of Ionic Identity Vault on Android, because the Android KeyStore entry does not require any authentication. This post shows how this was done and how it can be exploited.
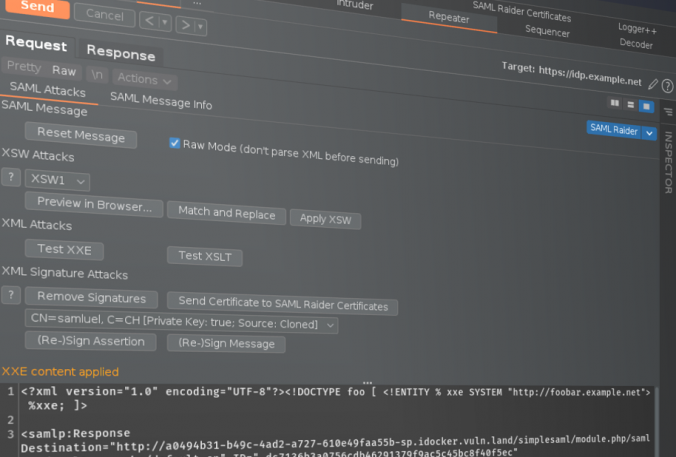
SAML Raider 1.4.0 is out which contains several new features like UI changes, new text editor, raw mode, XSW match/replace, parameter name definition and attack templates for XXE and XSLT attacks.
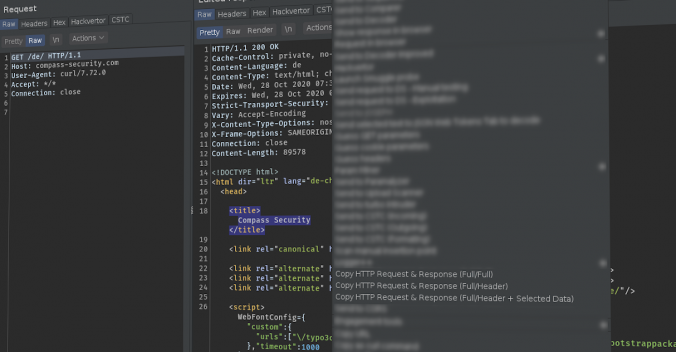
Writing good reports is key in penetration tests / security assessments, since this is the final result delivered to the customer. Vulnerabilities should be described in a way so that the customer can understand and also reproduce the issue. For web application pentests, the best way is often to show the HTTP requests and responses to explain an issue. This Burp Suite extension “Copy Request & Response” can assist you while the report.
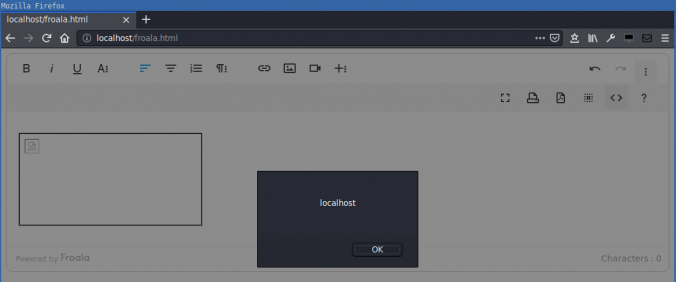
Compass found a DOM-based cross-site scripting (XSS) in the Froala WYSIWYG HTML Editor. HTML code in the editor is not correctly sanitized when inserted into the DOM. This allows an attacker that can control the editor content to execute arbitrary JavaScript in the context of the victim’s session.
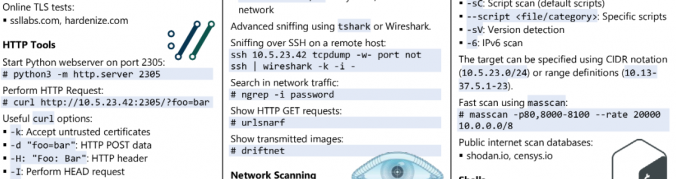
Everyone knows: cheat sheets are cool! They are very useful if you already know the basics about a topic but you have to look up details when you are not sure about something.
© 2025 Compass Security Blog