In 2024 we looked at the possibility of leveraging open weights LLMs for source code analysis. The answer was clearly negative, as a small code base could easily take 200K tokens, more than any context window offered by open weights models. The table below summarizes the top LLMs by context window as of today. Context […]
Compass Security Blog
Offensive Defense
TL;DR: PowerShell tool to enumerate Entra ID objects, assignments and identify highly privileged objects or risky configurations. https://github.com/CompassSecurity/EntraFalcon Entra ID environments can contain thousands of objects – users, groups, service principals, and more – each with unique properties and complex relationships. While manual reviews through the Entra portal might be feasible in smaller environments, they […]
This blog post introduces our new custom queries for BloodHound Community Edition (CE) and explains how you can use them effectively to analyze your Active Directory infrastructure. TL;DR: Check out our new BloodHound CE custom queries! Active Directory and BloodHound The majority of our customers run a Microsoft Active Directory infrastructure, either exclusively on-prem or […]
TLDR: Scan GitLab job logs for credentials using https://github.com/CompassSecurity/pipeleak Many organizations use (self-hosted) GitLab instances to manage their source code and a lot of infrastructure is managed in code (IaC), thus these configurations must be source-controlled as well, putting a lot of responsibility on the source code platform in use. Often deployments are automated using CI/CD […]
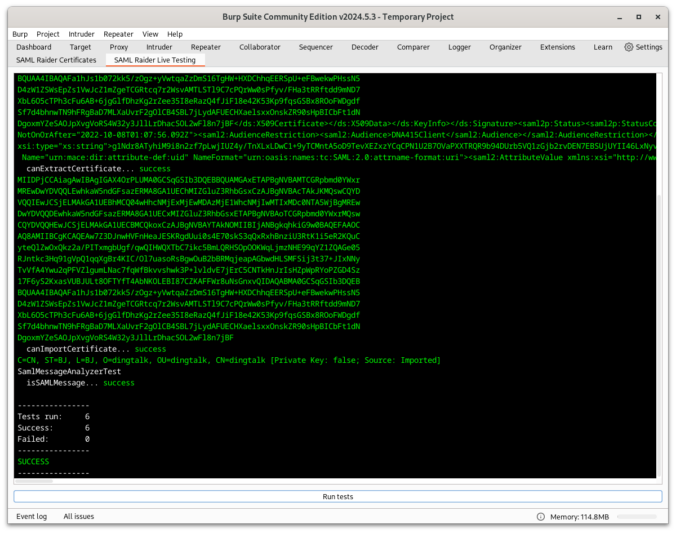
SAML Raider is a Burp Suite extension and the tool of choice for many pentesters for testing SAML infrastructures. This blog post should give a brief introduction to what has changed in the new version 2.0.0. From Improving developer and user experience to bug fixes.
TL;DR Release of Conkeyscan – A Confluence Keyword/Secret Scanner, which is tailored towards pentesters. Secrets Everywhere Many companies, especially larger ones, need to store knowledge in a centralized way. A wiki is the usual choice for this. One product that is frequently used for this purpose is Confluence from Atlassian. Similar to how sensitive data […]
Authentication and authorization are critical components of any application. Various standards and frameworks have been developed to facilitate the development of such components and make applications more secure. Among them, JSON Web Tokens (JWTs) have become popular choice over the years.
In this article, we discuss commons flaws in JWT-based authentication and present our extension to automatically check for these issues in Burp: JWT-scanner.
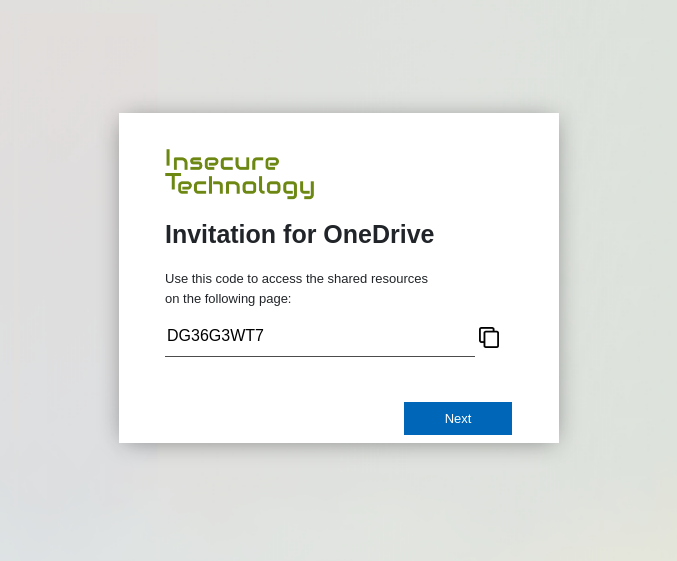
TL;DR An attacker is able to register new security keys (FIDO) or other authentication methods (TOTP, Email, Phone etc.) after a successful device code phishing attack. This allows an attacker to backdoor the account (FIDO) or perform the self-service password reset for the account with the newly registered sign-in methods. Microsoft deemed this not a vulnerability.
Device code phishing is nothing new. In fact it has been around for some years now. Despite the awesome capabilities of device code phishing, it is not widely used by threat actors. Therefore, it probably does not receive much attention from Microsoft. Compass Security is releasing two tools that can work hand in hand in a device code phishing exercise or even your next red team engagement.
A journey into the discovery of privilege escalation vulnerabilities in the Lenovo Update process.
© 2025 Compass Security Blog