In today’s interconnected world, it is a well-known fact that systems with Internet exposure are under continual threat of cyber-attacks. This risk extends from private websites to corporate infrastructure. With the increasing modernization of Industrial Control Systems (ICS), these vital components also become more exposed to such threats. But what is the extent and nature of attacks against industrial infrastructure? Do certain countries, such as Ukraine, face a disproportionately high number of attacks? In this exploration, we delve into these questions, using data collected from honeypots mimicking different ICS products in both Ukraine and Germany, to better understand the landscape of cyber intrusions in this specific field.
Fundamentals of Industrial Control Systems
Industrial Control Systems (ICS) are crucial for monitoring and managing complex industrial processes and systems. They form a significant part of the broader Operational Technology (OT) family. These systems encompass various subgroups and components, including Programmable Logic Controllers (PLC), Supervisory Control and Data Acquisition (SCADA) systems, and Human-Machine Interfaces (HMI), among others.
In the evolving landscape of those systems, there has been a emergence of devices that serve as a bridge between traditional ICS components, using industrial protocols, and more modern technologies featuring, e.g., Internet connection via cellular network, HMI displays integrated into web interfaces, and more. The integration of modern technology into traditional Industrial Control Systems (ICS) not only facilitates greater operational flexibility but also significantly increases the attack surface, particularly due to the capability for direct remote management over the Internet.
Overview of Documented Cyberattacks on ICS Infrastructure
Often, attackers compromise the business network of an industrial company without directly impacting the Industrial Control System (ICS) infrastructure. A prime example of this is the incident at Colonial Pipeline, where the business systems were impacted by a ransomware attack. The attackers stole data and encrypted many internal business systems. As a precaution, the pipeline operations were temporarily halted to mitigate any risk to the operational network [1] [2]. To successfully interfere with an industrial process, attackers typically need a deep understanding of the underlying protocols, industrial processes, and sometimes ways to circumvent Safety Instrumented Systems (SIS).
Due to the scarcity of publicly available data, obtaining a comprehensive view of direct attacks on ICS infrastructure remains challenging. A short overview about some public records:
- 2010: Stuxnet ist the most popular attack regarding ICS infrastructure. The malware exploited four previously unknown security vulnerabilities. It specifically targeted Siemens PLC hardware used in uranium enrichment centrifuges. Stuxnet overran the centrifuges while manipulating sensor data to remain undetected, assumingly destroying about one-fifth of Iran’s centrifuges [3].
- 2010: Presumed Iranian actors gained access to the SCADA system of a small dam in New York. However, the attack did not have any impact since the small remotely controllable sluice gate was disconnected for maintenance at the time of the intrusion [4][3].
- 2013: Identified in 2013, the Havex malware utilized the OPC protocol to map industrial equipment and gather information about industrial systems. It is believed that the attackers targeted over 2’000 industrial sites, mainly in Europe and the US [5][6].
- 2014: An undisclosed German steel mill suffered a significant cyber-attack on its ICS infrastructure. Attackers used social engineering to access the business network, subsequently compromising the industrial control systems. This caused a loss of control of the blast furnace, resulting in massive physical damage to the plant [7].
- 2015: On December 23, 2015, a coordinated attack on three Ukrainian energy companies caused a power outage, affecting over 225’000 people. Around 50 regional substations experienced malicious remote operation conducted by multiple attackers. Furthermore, some industrial control systems had their existing firmware overwritten, making them inoperable [8].
- 2016: On December 17, 2016, another attack named CRASHOVERRIDE struck the Ukrainian energy sector. The malware involved, causing a power outage for an undisclosed number of people. Unlike other ICS malware attacks, this one did not target specific product vulnerabilities. Instead, it exploited industrial communication protocols (OPC, IEC 61850, IEC 101, and IEC 104) to map network infrastructure and identify targets. Furthermore, the malware had the capability to erase systems and overwrite configuration files of industrial control systems [9].
- 2011-2016: Various HMI systems from multiple manufacturers fell victim to an extensive, multi-year attack campaign on ICS. In some cases, initial access was obtained through a vulnerability in General Electric’s publicly accessible HMI system. This flaw allowed the system to execute an infected file, loading and running the Blackenergy malware. Additionally, it is likely that publicly accessible web-based SCADA software from Advantech/Broadwin were directly targeted as well [10].
- 2019: A former employee used the still working remote access to tamper with the water cleaning process of the Post Rock Rural Water District with intention to harm. An employee noticed the changes and reversed the actions [11][12].
- 2022: In September 2022, the hacktivist group GhostSec claimed to have compromised 55 Berghof Automation PLCs. The group disclosed some seized data from various controllers, identified as integrated HMI controllers accessible via a web browser. The precise impact of the attack remains unknown, highlighting that even less experienced groups can pose a threat to inadequately secured industrial control systems [13].
- 2023: In November and December 2023, the Iranian-backed hacktivist group Cyber Avengers successfully compromised ICS devices at two water distribution facilities in the United States [14] and Ireland [15] by using the default password (CVE-2023-6448). While the US attack had no consumer impact, in Ireland, 160 households experienced a two-day freshwater cutoff.
These examples show that ICS are attacked by a variety of threat actors, including advanced persistent threats (APTs), hacktivists, and even insiders.
The Honeypot Environment
While there are established honeypot solutions like Conpot or XPOT, their recognition among attackers might influence the results. Therefore, it was decided to manually recreate the web interface of existing products. It was hoped this approach would make the systems less recognizable as honeypots, at least on the first few interactions.
System Architecture and Design
Given that manufacturers typically do not release source code for their systems, publicly reachable products were identified using shodan.io, an IoT search engine. Due to the large availability of example systems, it was chosen to partially recreate four different products:
- A Programmable Logic Controller (PLC) with a web interface.
- An Industrial Cellular Gateway, which connects industrial systems to the Internet via mobile networks.
- A Human-Machine Interface (HMI) system with a web interface.
- A web-based SCADA (Supervisory Control and Data Acquisition) solution.
The static web content was copied from publicly available systems. For dynamic data, the API responses were studied and manually replicated. Functions that could alter the original system – such as information modifications, restarts, or firmware installations – were not tested or included in the replicas. Where assumptions about the behavior of these systems were necessary, generic error messages were implemented instead. All identifiable details, including company names, IP addresses, location data, and MAC addresses, were replaced with fictional counterparts, ensuring that the original systems remained unidentifiable.
When accessing these emulated systems, visitors are greeted by the login page of the respective product. In line with the product manuals, the default credentials are valid on three of the four products. Visible information within these systems was carefully adjusted to reflect country-specific details, like location information, cellular providers, time zones etc. Additionally, some advanced functionalities were emulated, such as a web-based Command Line Interface (CLI). This feature allows for operations like internal network enumeration with ping, including simulated responses from various internal IP addresses.
Each product was operated on dedicated Virtual Private Servers (VPS) operated by one of eight different cloud providers located in Ukraine or Germany. The systems were made accessible on their default ports, 80, 8080, and a non-standard HTTP port. Furthermore, additional infrastructure for monitoring and management have been deployed.
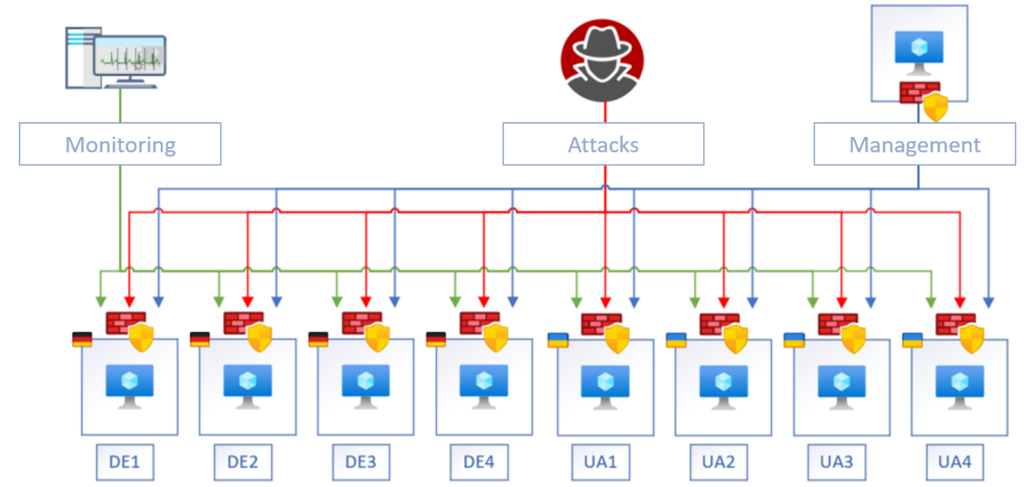
During the study, all network traffic was recorded and later analyzed using the Intrusion Detection System Suricata. This analysis used approximately 600 custom-written rules along with around 6,500 existing rules to categorize and analyze HTTP requests. Additional classifications, such as the type of attack, the year of the related CVE (Common Vulnerabilities and Exposures) or exploit, were manually added, particularly for larger clusters.
Interaction categorization
A whitelist approach was adopted to categorize every request as malicious or non-malicious. The following criteria were used.
HTTP requests not classified as malicious:
- All requests generated through the use of publicly available functions of the four ICS products.
- Queries for standard resources, like robots.txt, favicon.ico, and similar files.
- Requests exhibiting significant structural errors.
- Connection requests.
HTTP requests classified as malicious:
- Any requests not falling into the above categories are considered malicious.
- Any requests containing malicious code which is detect by a Suricata rule.
Results
Data was collected over a period of nearly three months, spanning from July 16, 2023, to October 14, 2023. During this time, the emulated ICS products recorded a total of 83’947 HTTP interactions, providing a large dataset for analysis.
Out of the total interactions, 46’930 were categorized as malicious, while 37’017 were identified as non-malicious requests. The systems located in Germany recorded a marginally higher number of malicious requests, totaling 24’842, compared to those in Ukraine, which registered 22’088 such requests.
Geographic Origin and Target Tendencies
In this experiment, the source IP of each attack was determined using the MaxMind GeoLite2 Country database. However, it is crucial to note that attributing cyber-attacks to specific countries based solely on source IP addresses is not reliable. Attackers often conceal their true location using methods like Proxies, VPNs, or by hijacking systems in different countries.
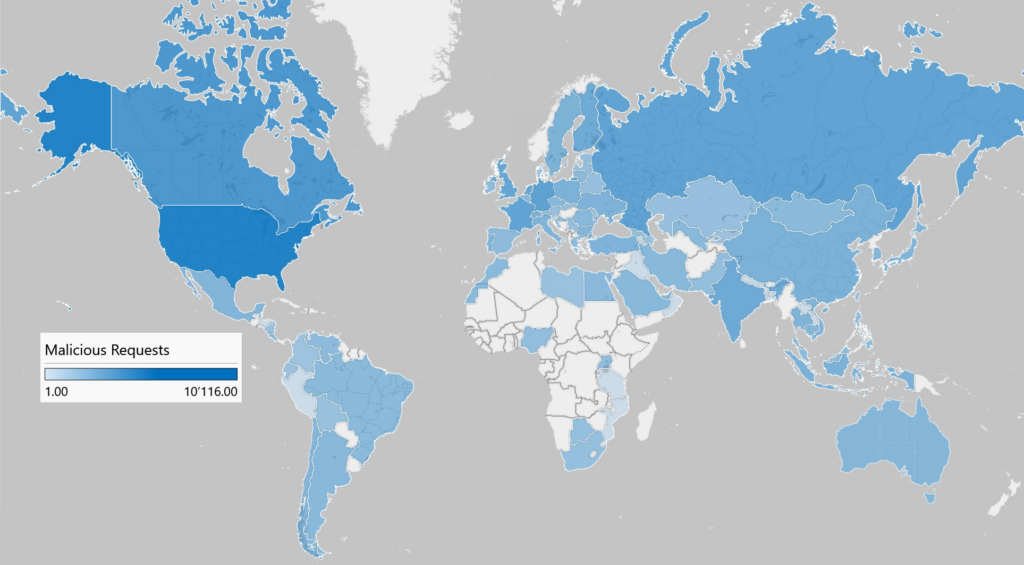
The map below visualizes the number of malicious HTTP-Requests to the honeypots attributed to various countries by the source IP. It shows that the honeypots received malicious requests from around the world. The United States tops the list with over 10’000 requests, followed by Canada and Germany. 41% of the malicious requests originated from those three countries.
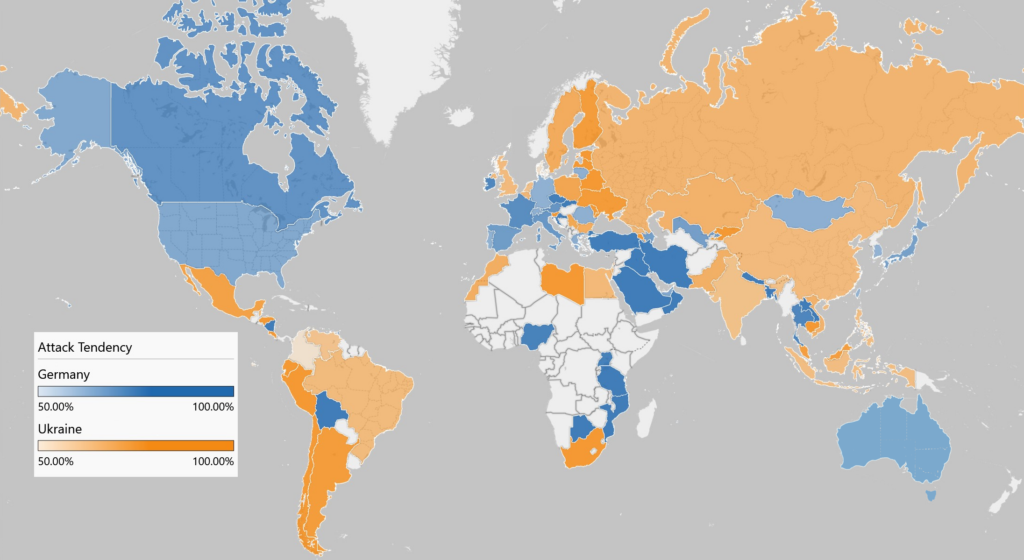
A notable detail is the disproportion between malicious requests targeting Ukraine and Germany, with certain countries like Canada, France, and Turkey showing a heavy bias toward German systems. In contrast, the Russian Federation, Finland, Poland, and Sweden have sent more malicious requests to Ukraine. The intensity of the color on the map reflects the target tendency, with darker colors indicating a higher tendency to target the honeypots situated in either Ukraine or Germany.
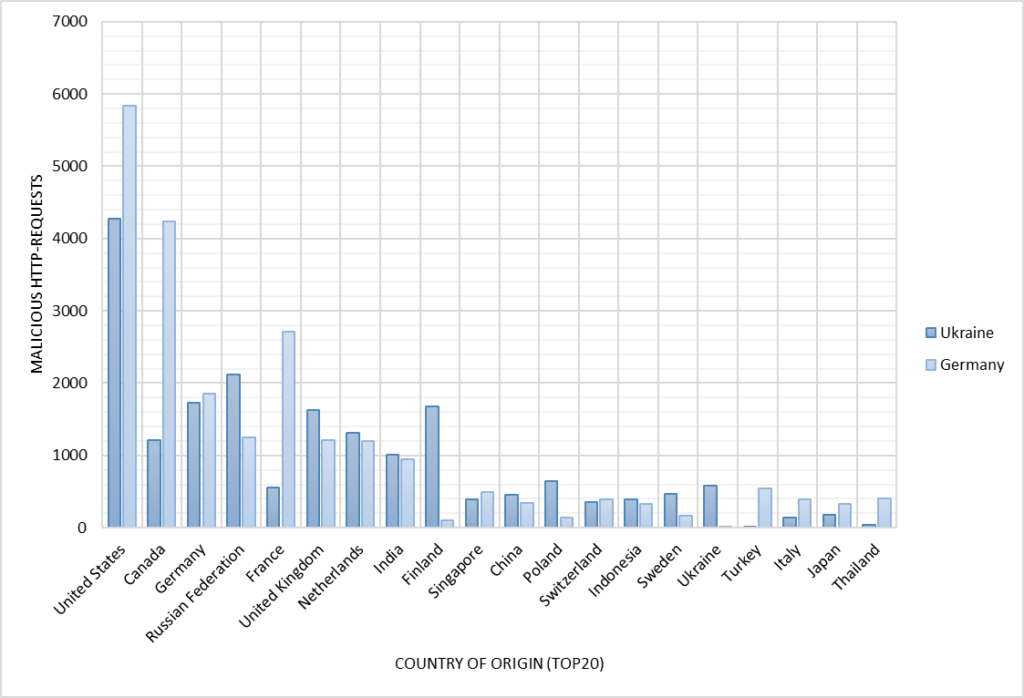
The bar chart below categorizes the top 20 countries by the number of malicious requests they have made to honeypot systems in Germany and Ukraine.
Automated Attacks
The vast majority of attacks were not specifically targeting the simulated ICS. Instead, most attacks were rather typical web-based attacks observed on the Internet. This is explained by the fact that all systems exposed online are subject to constant scanning, and automated exploit attempts are made against a wide range of products.
87.5% of the malicious request (41’054) have been categorized as forced browsing. These requests are part of reconnaissance activities, where attackers aim to discern product types, management portals, or directly access sensitive information. For instance, 8’049 requests tried to verify the presence of PHPMyAdmin, a popular database management framework. Another significant portion of these requests targeted the /.env file, presumably linked to the Laravel PHP web framework, which could contain sensitive information or secrets.
4’007 malicious requests contained payloads leading to code execution, SQL injection, SSRF, XXE or authentication bypasses. At least 2’662 of those requests aimed to exploit specific vulnerabilities in specifics products. The majority of the exploits allows the attacker to execute their own code on the underlying operating system. The targets varied across a large number of products, including:
- Networking devices such as routers from brands like D-Link, Netlink, LB-LINK, ToTolink, Netis, Linksys, and Fortinet.
- Web CMS solutions, notably WordPress (along with its plugins), Joomla, Drupal, and Kentico.
- Various applications and infrastructure components from VMware, Citrix, Zimbra, Apache, and Atlassian.
For 2’700 requests the payload age (based on the CVE or exploit code publishing date) has been determined. The data shows a consistent pattern of attacks using vulnerabilities from previous years, not just the most recent ones.
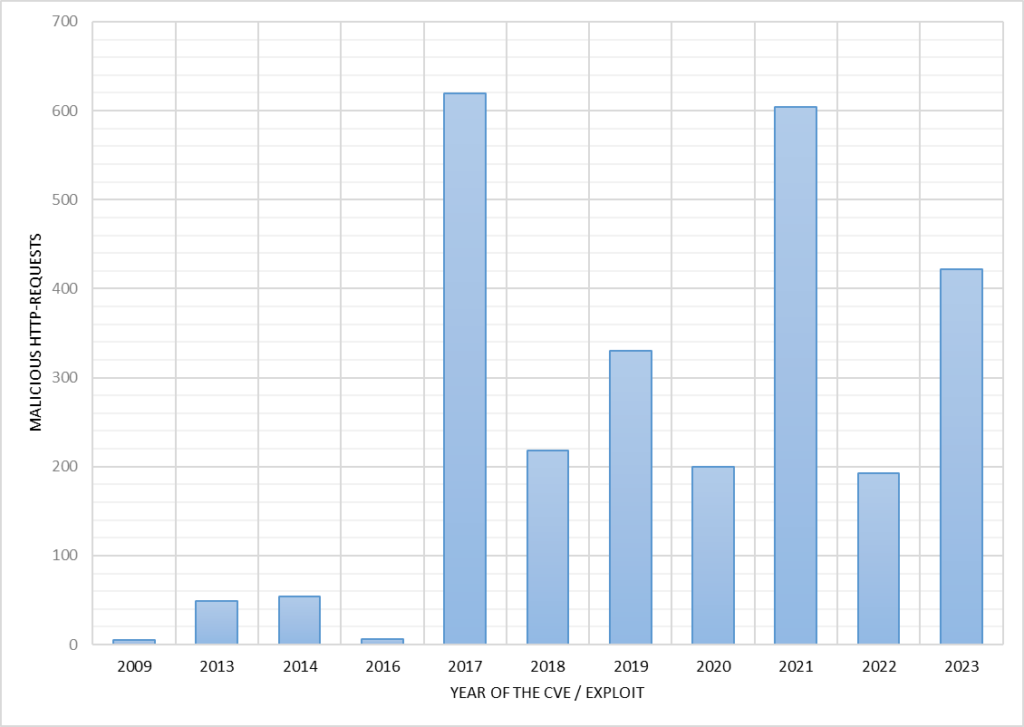
Additionally, there were 1’573 requests attempting to log in to various products like WordPress, Artifactory, and Tenda routers.
ICS-Specific Attacks
Targeting Other ICS Products
Reconnaissance activities targeting ICS were also evident. Across all eight systems, including those operating on non-standard HTTP ports, there were in total 61 requests probing for the presence of a page associated with the Siemens SIMATIC S7 Controller:
GET /Portal/Portal.mwsl HTTP/1.1
User-Agent: curl/7.54.0
Connection: close
Host: [Redacted]
The bulk of these requests originated from two IP addresses located in the UK, followed by a significant number from Germany. A smaller portion of the requests came from IP addresses in the Netherlands and Russia.
Targeting the Emulated ICS Products
296 login attempts targeted the two emulated products. Out of those, a staggering 295 were directed at the Industrial Cellular Gateway, while the remaining single attempt targeted the SCADA system. In 10 instances, the attackers successfully used the correct username and password combination. However, contrary to expectations, these successful logins did not lead to any further authenticated requests on the products. Despite originating from various IP addresses in Russia, Poland, and Turkey, the attacks used similar credentials and identical HTTP request parameters like User-Agent, Accept and Accept-Language. This uniformity suggests the attack might be conducted by the same attacker or multiple attackers using the same toolkit.
POST /checklogin.php?action=1 HTTP/1.1
Origin: http://[Redacted]:8080
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/93.0.4577.82 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif ,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Language: en-US
Cookie: PHPSESSID=ts41gvbiam5a9vkp6d5oq9lgft
Host: [Redacted]:8080
Content-Length: 44
username=admin&password=password&Login=Login
One product faced 84 attempts to exploit the vulnerability CVE-2023-1698. This vulnerability allows attackers to run commands on the operating system of the product. The attacks were geographically dispersed, with 43 HTTP requests targeting the system in Germany and 41 in Ukraine.
In 80 cases, the attacker issued the payload to execute the command id which would show the current users. In two separate requests, the command cat /etc/passwd was used, aiming to access information about user accounts. In two other cases they tried to download a script from an external source using wget.
From 24 out of total 29 IP addresses, malicious requests were sent to systems in both Germany and Ukraine:
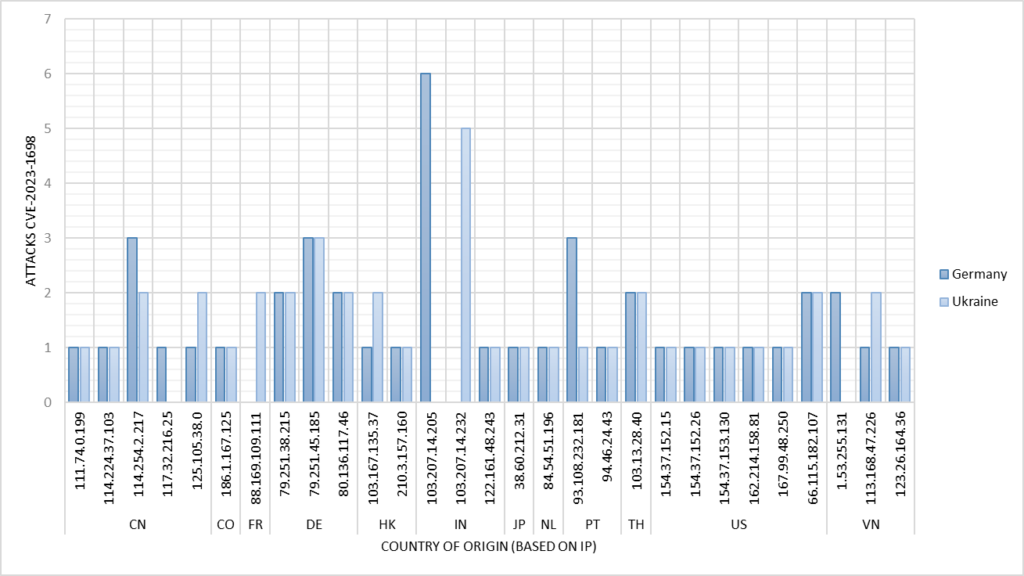
Notably, this specific exploitation attempt was absent in the other six honeypots, each emulating different ICS products, highlighting a targeted attack pattern on this particular vulnerability. Consequently, the attackers carried out reconnaissance activities to identify the product prior to launching attacks that contained specific exploits.
An example of the activities conducted by one of the attacker IP addresses:
| Timestamp | System | Activity |
|---|---|---|
| 03.08.2023 02:53:02 | Honeypot DE | Performing a HTTP-Request on web root |
| 03.08.2023 02:55:04 | Honeypot UA | Performing a HTTP-Request on web root |
| 03.08.2023 02:57:05 | Honeypot DE | Send an HTTP Request with the exploit |
| 03.08.2023 02:57:05 | Honeypot UA | Send an HTTP Request with the exploit |
Beyond the Honeypots: Identifying a Critical SCADA Security Flaw
While constructing the SCADA honeypot, a misconfiguration in the original SCADA solution was identified. This flaw permitted unauthorized admin login access on the solution. Upon further examination, it was discovered that at least 20 water supply facilities using the same product were susceptible to this vulnerability.
This critical issue was immediately reported to both the manufacturer and the Computer Emergency Response Teams (CERT) of the affected country. The CERT classified the issue as high priority and took immediate action. This discovery, though incidental to the main research, underscores the pressing necessity for heightened security measures in this domain.
Conclusion and Recommendations
The data gathered from the honeypots does not provide any surprising new insights. Maybe due to the fact that the honeypots could be easily recognizable as decoy systems, possibly because they are hosted as Virtual Private Servers (VPS). Deploying these systems over cellular networks in the respective countries could yield different results and potentially provide more covert and realistic scenarios. However, the analysis of the collected data confirms several points:
- There is a significantly high volume of automated reconnaissance and exploitation attacks targeting devices accessible via the Internet.
- Known vulnerabilities in ICS components are actively exploited.
- Blocking IPs based on their country of origin can lower the number but does not mitigate these attacks.
Based on this, we give the following recommendations:
- In general, it is not recommended to expose non-security components directly to the Internet. If any remote access is required at all, it is recommended to use Virtual Private Networks (VPN) or another layer of security to protect the systems against direct attacks. If possible, only whitelisted IPs should be allowed. Furthermore, the ICS network should be isolated from the business network as well.
- A strong patch management process should be established. Security patches on Internet exposed systems should be applied within hours.
- Multifactor authentication and strong credentials should be used.
- Logging and monitoring of devices to detect attacks or suspicious usages should be performed.
Further recommendations regarding ICS security:
- Recommendations NCSC (CH)
- Recommendations BSI (DE)
- Recommendations CISA (US)
- Recommendations NIST (US)
References
- https://www.techtarget.com/whatis/feature/Colonial-Pipeline-hack-explained-Everything-you-need-to-know
- https://www.law.georgetown.edu/environmental-law-review/blog/cybersecurity-policy-responses-to-the-colonial-pipeline-ransomware-attack/
- Hemsley, Kevin E., and E. Fisher, Dr. Ronald. History of Industrial Control System Cyber Incidents. United States: N. p., 2018. Web. https://doi.org/10.2172/1505628
- https://www.justice.gov/opa/pr/seven-iranians-working-islamic-revolutionary-guard-corps-affiliated-entities-charged
- https://www.cisa.gov/news-events/ics-advisories/icsa-14-178-01
- https://www.dragos.com/blog/industry-news/the-evolution-of-cyber-attacks-on-electric-operations/
- https://www.bsi.bund.de/SharedDocs/Downloads/EN/BSI/Publications/Securitysituation/IT-Security-Situation-in-Germany-2014.pdf
- https://info.publicintelligence.net/NCCIC-UkrainianPowerAttack.pdf
- https://www.dragos.com/wp-content/uploads/CrashOverride-01.pdf
- https://www.cisa.gov/news-events/ics-alerts/ics-alert-14-281-01e
- https://www.waterisac.org/portal/updated-october-21-2021-insider-threat-%E2%80%93-former-employee-indicted-unauthorized-computer
- https://www.waterisac.org/system/files/articles/travnichek-indictment.pdf
- https://www.otorio.com/blog/pro-palestinian-hacking-group-compromises-berghof-plcs-in-israel/
- https://edition.cnn.com/2023/12/01/politics/us-water-utilities-hack/index.html
- https://therecord.media/water-outage-in-ireland-county-mayo
Leave a Reply