Introduction As you may know, Compass Security participated in the 2023 edition of the Pwn2Own contest in Toronto and was able to successfully compromise the Synology BC500 camera using a remote code execution vulnerability. If you missed this, head over to the blog post here https://blog.compass-security.com/2024/03/pwn2own-toronto-2023-part-1-how-it-all-started/ Unfortunately, the same vulnerability was also identified by other […]
Compass Security Blog
Offensive Defense
Renovate is an OSS CLI/bot that updates your software dependencies automatically. It is usually integrated into the CI/CD process and runs on a schedule. It will create a Pull Request / Merge Request (PR/MR) to your repository with dependency updates. It can optionally auto-merge them. If you host it for several repositories or an organization, it […]
As a pentester you are sometimes thrown into projects where you have no idea where you are going to end up. This project was one of those where you were given a customer laptop and the aim was to “find something interesting”, perhaps a misconfiguration on the customer side. The problem was that the laptop […]
Given the explosion of development and interest in deep learning models in the past year, we decided to research on the topic to increase our know-how and find applications where these technologies can be leveraged in offensive security engagements.
This posts explores the use of machine learning for voice cloning and how it can be used for social engineering.
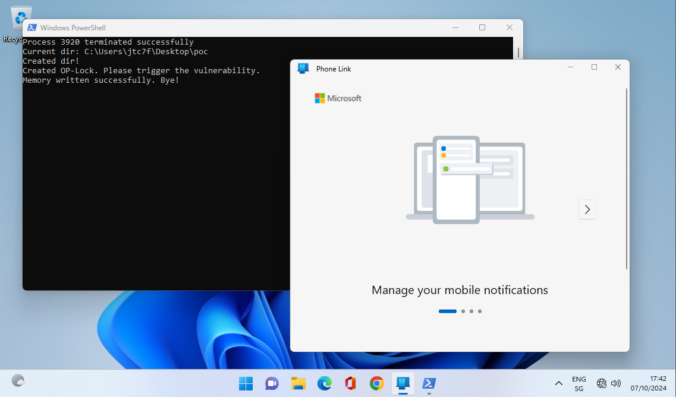
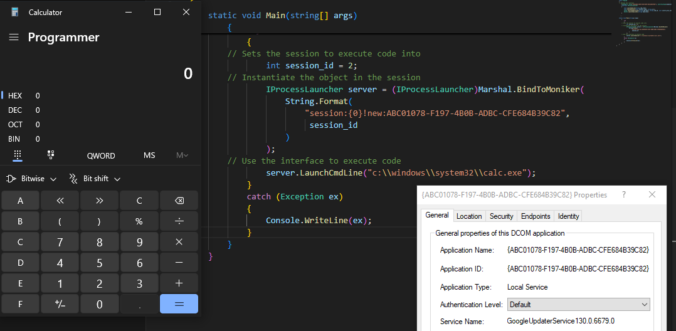
Once again, reading blogs and tweets from James Forshaw led me to wonder how things work. This time, I was working on DCOM for my last blog post and while reading about cross-session activation, I had trouble believing what I was reading.
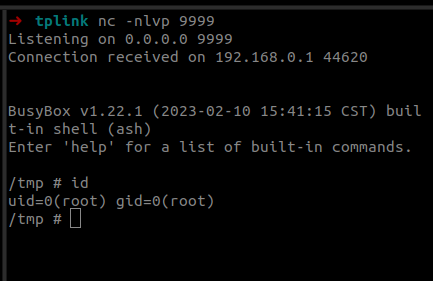
Last year we participated in the Pwn2Own 2023 Toronto competition and successfully exploited the Synology BC500 camera. The DEVCORE Internship Program team managed to exploit a bug in the TP-Link Omada Gigabit VPN Router. So I was naturally curious and wanted to figure out how difficult it would be to recreate that exploit having access only to a high-level bug description and the firmware.
To identify and understand threats and weaknesses of smart contracts, it is important to be at least familiar with common smart contract bugs and vulnerabilities, how they can be leveraged by a malicious attacker, and how these issues can be mitigated.
This blog article aims to raise awareness about common smart contract vulnerabilities and their corresponding mitigation strategies.
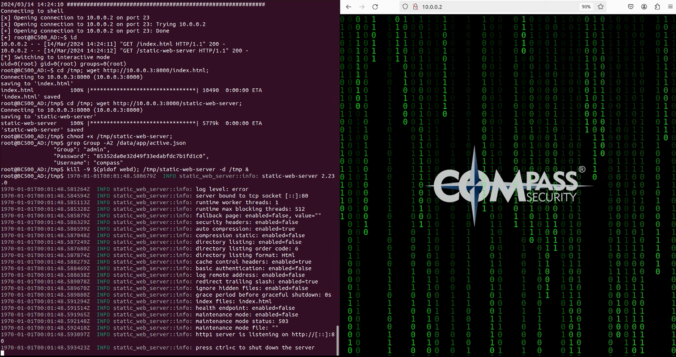
In this final part of this series, we are finally going to explain how the stack-based buffer overflow vulnerability can be exploited to gain unauthenticated remote code execution (RCE) on the Synology BC500 camera.
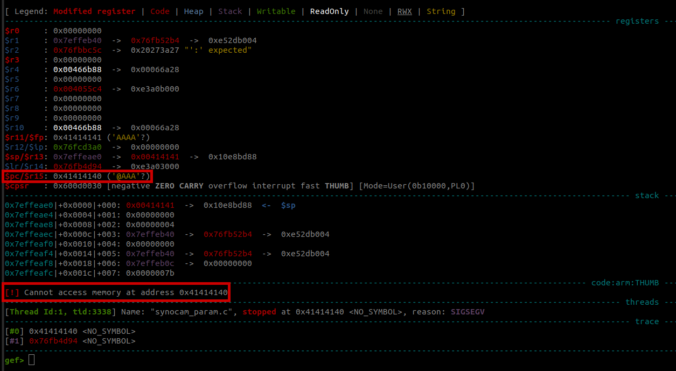
In this fourth part of the series, we analyze the memory corruption identified previously and manage to overwrite the program pointer!
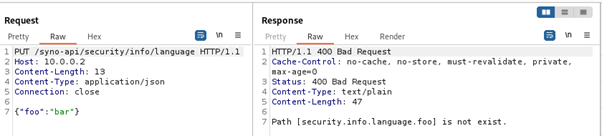
In this third part of the series, we focus on the exposed web services running on TCP ports 80 and 443.
Since a valid exploit chain must achieve code execution without prior authentication, we focus on the available functionality that can be accessed without authentication.
© 2025 Compass Security Blog