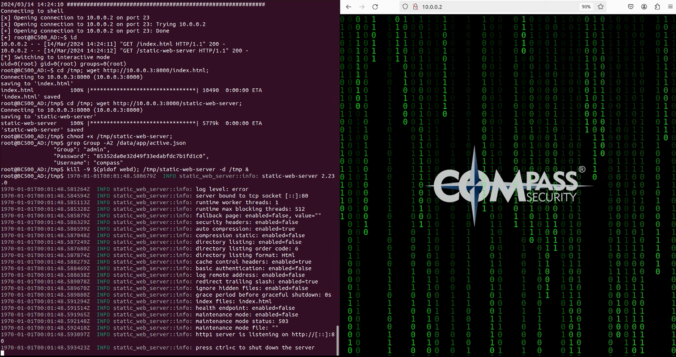
In this final part of this series, we are finally going to explain how the stack-based buffer overflow vulnerability can be exploited to gain unauthenticated remote code execution (RCE) on the Synology BC500 camera.
Compass Security Blog
Offensive Defense
In this blog article, we would like to share key insights from the “Defeating Microsoft’s Default BitLocker Implementation” security training by Hands-On Security and emphasize the potential risks and consequences associated with this attack technique. Our target audience includes businesses looking to safeguard sensitive data on their Windows devices, as well as individuals with an elevated requirement for protecting their data.
© 2025 Compass Security Blog