My colleague Mirko and I recently attended the “Defeating Microsoft’s Default BitLocker Implementation” security training by Hands-On Security. The training was excellent and got us really excited about the topic. In just two days, Pascal Gujer and Joel Frei taught the group the skills and knowledge needed to bypass a default BitLocker configuration on a T470 ThinkPad. Importantly, these methods can be used on most modern business machines, not just this particular model.
The attack has also gained significant attention in the security community this year, with many blog articles being published and Youtube videos where BitLocker is bypassed in under a minute being released.
In this blog article, we would like to share key insights from the training and emphasize the potential risks and consequences associated with this attack technique. Our target audience includes businesses looking to safeguard sensitive data on their Windows devices, as well as individuals with an elevated requirement for protecting their data.
Background
BitLocker is a disk encryption feature in Microsoft Windows operating systems that helps protect the confidentiality of the data on a computer by encrypting the hard drive. If a laptop is lost or stolen, an attacker who gains physical possession of the machine cannot access the data or tamper with the system, even when removing the disk and accessing it from another system. This prevents unauthorized data access as well as Evil Maid attacks where an attacker with (temporary) access to a device attempts to install a backdoor into the system.
On most modern business laptops (Lenovo ThinkPad, HP Elite Book, Microsoft Surface), the cryptographic key material to decrypt the disk during boot is stored in a Trusted Platform Module (TPM). A TPM is a hardware-based security chip that provides a secure tamper-resistant environment for storing key material and performing cryptographic operations.
BitLocker Configuration
BitLocker can be run in different modes:
- TPM-only: The operating system boots normally to the logon screen without any user interaction.
- PIN Protector: The user must provide a PIN during boot.
- Startup Key Protector: The user must provide a startup key (typically stored on a USB thumb drive) during boot.
For maximum security, the PIN and startup key protectors can be combined, such that the user must provide a PIN (knowledge factor) and a key file (possession factor) during boot. In our experience, virtually all customers have TPM-only mode configured on their Windows devices. On Windows 11 where BitLocker is enabled by default, TPM-only mode is used unless configured otherwise.
BitLocker Architecture
To understand the attack and mitigations, it is important to have a solid understanding of some BitLocker implementation details.
In the TPM-only mode, the Volume Master Key (VMK) is released during boot and sent to the CPU. The CPU then fetches the encrypted Full Volume Encryption Key from the BitLocker partition metadata and decrypts it with the VMK to obtain the plaintext Full Volume Encryption Key. This is visualized in the image below:
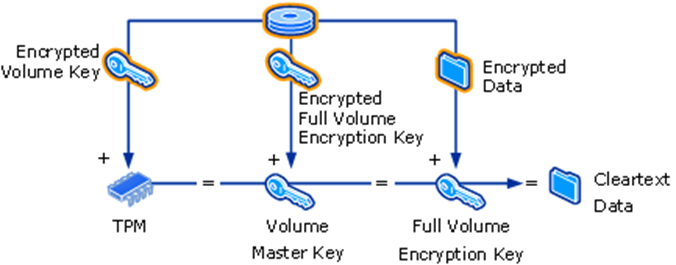
(Source: Microsoft documentation)
In other words, with access to the VMK and the encrypted BitLocker partition, the disk can be decrypted. It is worth emphasizing that the plaintext VMK is sent to the CPU over physical wires. This gives an attacker the opportunity to sniff the data channel and intercept the VMK. Given the VMK, the attacker can obtain the Full Volume Encryption Key and access the disk. Alternatively, since the recovery passphrase is stored encrypted under the VMK in the disk metadata, the recovery passphrase can be obtained once the VMK is known.
While the image above only covers the TPM-only mode scenario, the following image shows the mechanism for other key protectors:
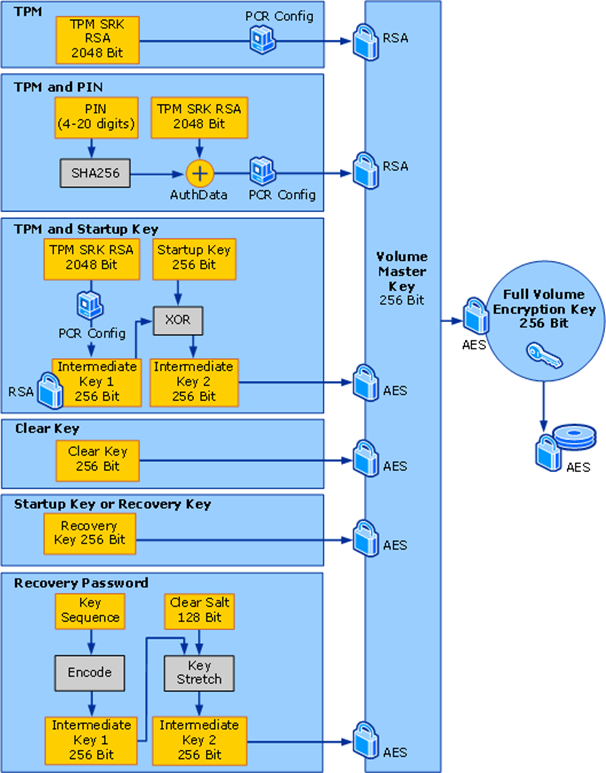
(Source: Microsoft documentation)
The most common boot scenarios are briefly described below:
- TPM: In the TPM-only mode, the user is not required to provide a protector to unlock the TPM. During boot, the boot environment is measured, meaning that the firmware and software that is loaded is tracked and the measurement values are stored in the Platform Configuration Registers (PCR). The TPM only releases the key if the PCR values contain expected values. This guarantees that the key is only released if the authentic Windows operating system is booted. In particular, this prevents an attacker from booting another operating system and then mounting the disk, as the PCR registers would contain invalid values.
- TPM and PIN: The VMK is only released to the CPU after the user has provided the correct PIN. (The PCR values are checked as well, just as in the TPM-only mode.)
- TPM and Startup Key: The VMK is only released to the CPU after the user has provided the correct startup key. (The PCR values are checked as well, just as in the TPM-only mode.)
Attack
This section outlines the steps involved in carrying out the attack. The goal is not focus on nitty gritty details, but rather demonstrate the feasibility of the attack. No esoteric techniques or expensive hardware that can only be found in an advanced lab is required. In fact, all these steps were carried out with equipment that costs less than 1000 CHF. The attack is thus very affordable. Depending on the target device, attacks with much cheaper hardware have been demonstrated.
TPM Bus Sniffing
The goal of the attack is to sniff the communication between the TPM chip and the CPU. Business laptops usually feature a discrete TPM, i.e., a dedicated physical tamper resistant chip on the motherboard. There are other TPM types (integrated, firmware, software, virtual), for which the attack does not work.
On the ThinkPad T470, the TPM can be accessed by removing the back cover, which can be achieved by removing a few screws and prying open the back:
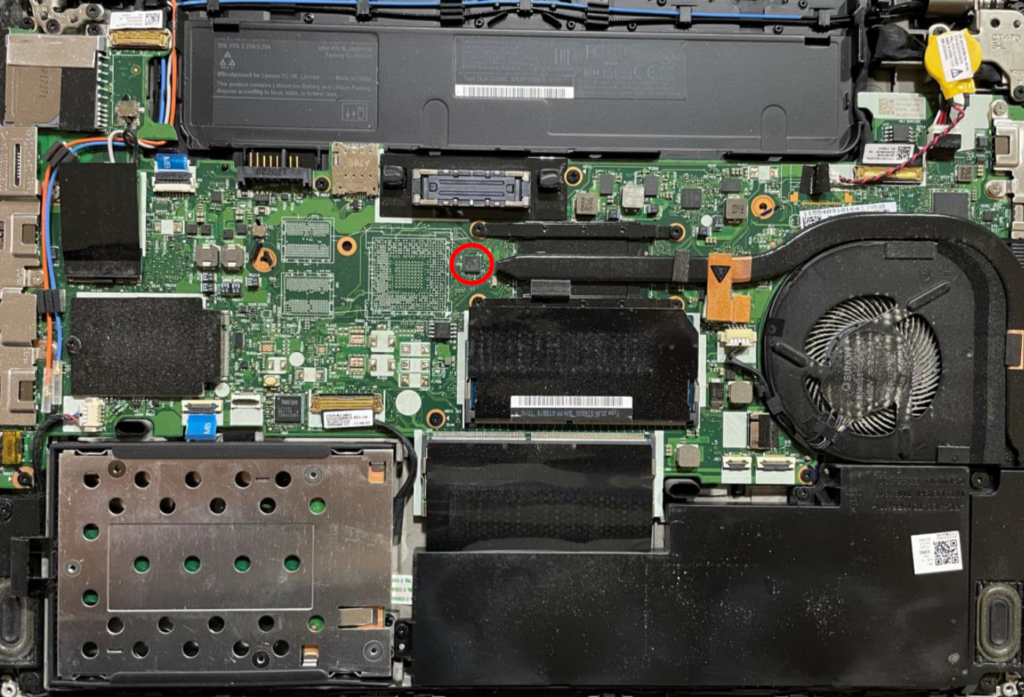
This process takes less than a minute or even mere seconds with some practice. The following picture shows the chip in more detail:

After locating the TPM chip, the attacker solders cables onto the relevant PINs. In the case of the T470, the Serial Peripheral Interface (SPI) communication protocol is used. Therefore, an attacker needs to connect five cables:
- MOSI
- MISO
- Channel Select (CS)
- Clock (CLK)
- Ground
The TPM pins themselves are very small, making it difficult to solder a cable. Instead, one usually looks for larger components on the mother board (e.g., resistors, capacitors, debug ports, larger connected chips) that are connected to the same bus used by the TPM to communicate with the CPU. On the motherboard of the T470, the TPM is connected to a relatively large SPI flash controller. By soldering onto the respective pins, the SPI communication channels can be sniffed. The following picture shows the SPI flash controller chip and the soldered wires:
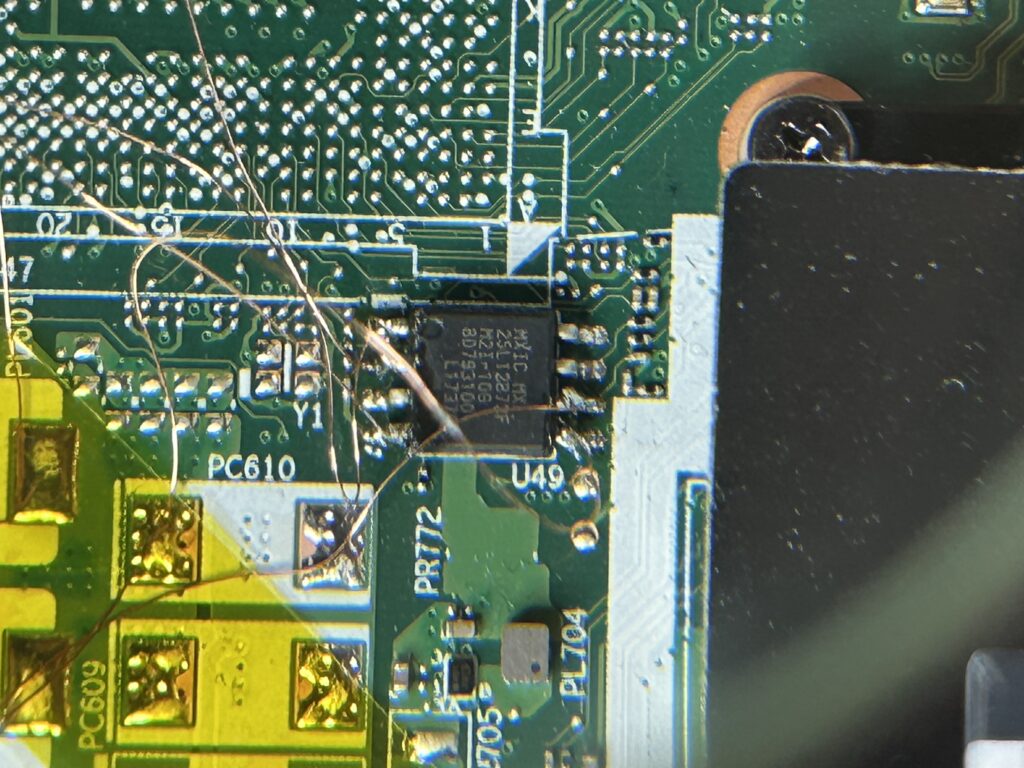
These wires were then connected to a DreamSourceLab logic analyzer (DSLogic U3Pro16) to sniff the bus communication:

DSView can be used to record and analyze the recorded SPI TPM traffic. There is even a built-in decoder to search for the VMK in the recorded trace:
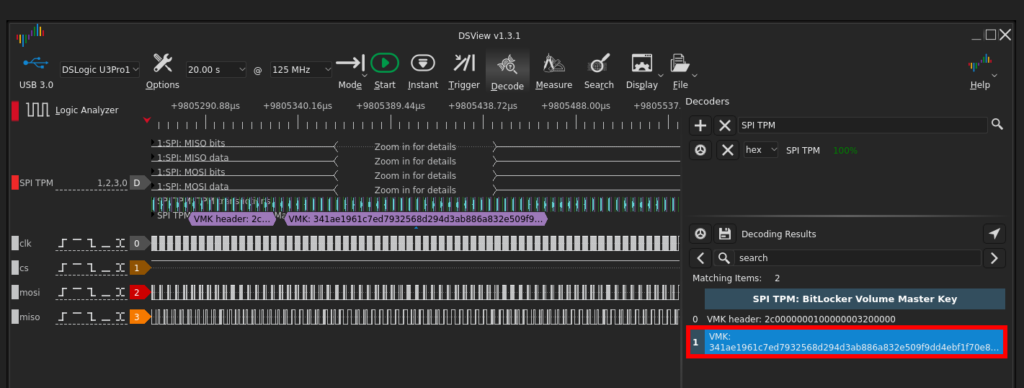
Afterwards, the BitLocker recovery key can be obtained with the Sigrok BitLocker Key Extractor tool:
$ bitlocker-recovery-password-decryptor.py 341ae1961c7ed7932568d294d3ab886a832e509f9dd4ebf1f70e85261bd07171 bitlocker-disk.img
###############################################################################
# #
# BitLocker Recovery Password Decryptor #
# #
# by Pascal Gujer (@pascal_gujer) v1.1 #
###############################################################################
Extracting BitLocker key material with dislocker-metadata...
Parsing output...
Nonce: 9019ee4ee24bda0103000000
MAC: 30ca25ab9ef248ba376aa3b909f656e0
Encrypted Recovery Password: c6f012bf3b25eaa5cbcdf0e805e29199ce6a17275796f033beeb1a08
VMK: 341ae1961c7ed7932568d294d3ab886a832e509f9dd4ebf1f70e85261bd07171
Decrypting recovery password...
The decrypted recovery password is authentic:
1c000000010000000010000002c0057df57f9340902243c8c98a6038
[+] Sucessfully retrieved the BitLocker Recovery Password in human readable format:
540694-352055-360327-181841-097328-563937-390819-158752
At this point, the attacker can access all data stored on the disk and/or install backdoors (Evil Maid attack).
Mitigation
This section discusses various mitigation strategies as well as operational considerations that require attention in practice.
PIN / Startup Key
Recall from a previous section that the attack exploits the fact that in TPM-only mode the VMK is automatically released and sent to the CPU during boot, allowing the attacker to recover it by sniffing the bus communication.
The most secure approach to prevent the TPM from automatically releasing the key is configuring a PIN protector (a knowledge factor) or a startup key (a possession factor). If either of the two are configured, the VMK is not released until the protector is provided. An attacker without knowledge / possession of the protector thus cannot sniff the VMK during the boot process.
For maximum security, both a PIN protector and a startup key protector should be required. We have seen this setup work very well in practice.
Tamper Protection
Business laptops often implement a tamper protection mechanism that attempts to detect hardware tampering, for example:
- Lenovo ThinkShield Built in Platform Security (aka Tamper Switch)
- HP Tamper Lock
These tamper protection mechanisms are usually implemented with a physical switch that opens or closes a circuit when the backplate is removed. If tamper protection is detected, the system will either prompt the user for the BIOS password or the BitLocker recovery key during the next boot cycle.
Tamper protection can be enabled / disabled in the BIOS settings. A sample configuration is provided in the following screenshot:
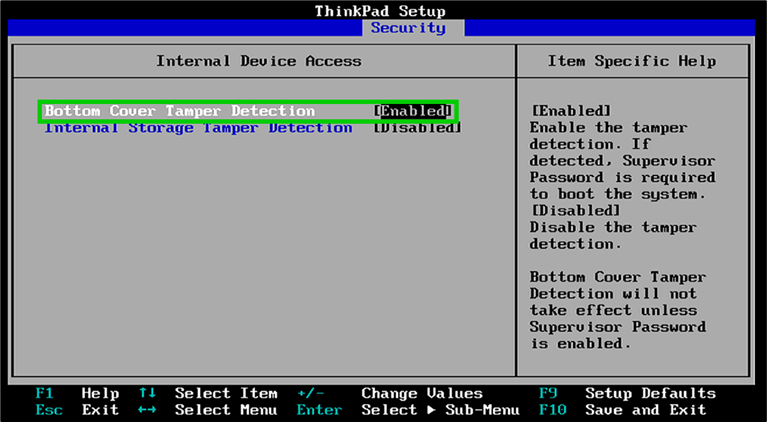
From a security perspective, prompting the user for the BitLocker recovery key is arguably slightly more secure than prompting for the BIOS password.
However, it should be noted that a careful attacker who is aware of tamper protection switches can rather easily bypass this protection mechanism by dremeling holes to access the PINs instead of removing the entire back cover. Depending on the switch type, it may also be possible to unsolder it. Tamper protection should therefore not be considered a primary defense mechanism against TPM sniffing attacks.
Operational Considerations
Whilst PIN and startup key protectors, or preferably a combination thereof, provide strong technical protection against TPM bus sniffing attacks, there are some important operational considerations. Without proper processes, the security guarantees provided by BitLocker might be significantly diminished or the whole protection rendered ineffective.
Recovery
When BitLocker is enabled on a laptop, there is a need for a recovery process because users can potentially lose access to the system due to various reasons. For example, they may lose / forget their BitLocker encryption key or password, experience hardware failures that prevent normal booting, or encounter issues with system updates or configuration changes. In such cases, the system can be recovered through a BitLocker recovery key.
It is crucial that there is a robust process that ensures the recovery key is only handed out over a secure channel, and that the employee is authenticated. If a simple phone call to the IT support team suffices to obtain the recovery key, even the strongest security configuration can be bypassed easily.
PIN Management
In practice, we have encountered setups where the same (simple) PIN was configured on a fleet of thousands of machines. These PINs are shared among all employees and are never rotated. Naturally, it cannot be guaranteed that the PIN can be kept secret, and a motivated attacker might very well be able to learn it through several means. An attacker in possession of the PIN can carry out the same attack as described in the previous section, with the only exception that they have to enter the PIN during boot to release the VMK.
It is therefore recommended that each machine is configured with a unique BitLocker PIN that is chosen by the employee during the initial setup of their hardware.
Startup Key Storage
The key file is usually stored on a USB thumb drive and is not protected with any user authentication mechanism, such as a fingerprint reader. If the attacker can get a hold of the laptop and the USB thumb drive, they can again carry out the attack outlined in the previous section. The only difference is that they have to plug in the drive to boot the machine.
Expectation Management
When evaluating defense mechanisms, it is crucial to not only focus on the benefits but also be aware of the limitations. Depending on the environment or the type of adversary, the most secure BitLocker configuration might not offer adequate protection. This is probably best illustrated with one of my all-time favorite XKCDs:
(Source: https://xkcd.com/538/)
Leave a Reply