In this blog article, we would like to share key insights from the “Defeating Microsoft’s Default BitLocker Implementation” security training by Hands-On Security and emphasize the potential risks and consequences associated with this attack technique. Our target audience includes businesses looking to safeguard sensitive data on their Windows devices, as well as individuals with an elevated requirement for protecting their data.
Compass Security Blog
Offensive Defense
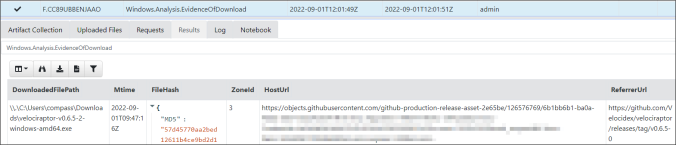
This post provides ideas of processes to follow and gives basic guidance on how to collect, triage and analyze artifacts using Velociraptor
This post is intended to explain what you typically want to check for during an OpenID Connect assessment and also provide you with a guide to setup your own OpenID Connect test environment.
This year three Compass analysts, Stephan Sekula, Dobin Rutishauser, and Philipp Promeuschel, attended the BlackHat and DefCon
I am given the opportunity to teach Exploiting & Defense in the Bern University of Applied Sciences (Berner Fachhochschule) in the module Application and Software-Security.
The “Internet of Things” (IoT) grows quickly. More and more devices are connected to the Internet to automate tasks and simply life. Fridges automatically order milk, cars are taught to self-drive via a simple update and bridges send live updates about their structural integrity. According to Gartner’s 2016 Tech Trends, IoT will define the shape of tomorrow’s […]
Until recently, the majority of organizations believed that they do not have to worry about targeted attacks, because they consider themselves to be “flying under the radar”. The common belief has been: “We are too small, only big organizations like financial service providers, military industry, energy suppliers and government institutions are affected”. However, this assumption […]
“Fake President Fraud” or “CEO Fraud” is a social engineering attack where an adversary tries to convince a member of the financial department of a company to send out a payment to the attacker’s bank account. The attack can be divided into three steps. Establish Contact: Typically only employees responsible for bank transfers get contacted by […]
As in past years, Compass Security will participate in the upcoming CyberSec Conference in Yverdon-les-Bains (formerly Application Security Forum – Western Switzerland). This year, we will contribute in two events: First, Antoine Neuenschwander and Alexandre Herzog will conduct a day long training session on Tuesday, November 3rd. Participants will be able to exercise their skills […]
Ein Hintegrundartikel zur SRF Einstein Sendung vom Donnerstag, 3. September 2015 um 21:00 Uhr zum Thema “Cybercrime, wie sicher ist das Know-how der Schweiz”. (Trailer online) In diesem Artikel zeigen wir Ihnen die Vorgehensweisen von Angreifern auf, die versuchen unerlaubten Zugriff auf fremde Systeme zu erlangen — beispielsweise im Netzwerk eines KMUs. Schematisch sind diese Vorgehensweisen […]
© 2025 Compass Security Blog