Writing good reports is key in penetration tests / security assessments, since this is the final result delivered to the customer. Vulnerabilities should be described in a way so that the customer can understand and also reproduce the issue. For web application pentests, the best way is often to show the HTTP requests and responses to explain an issue. This Burp Suite extension “Copy Request & Response” can assist you while you write the report.
Introduction
When copying request/response from Burp, the workflow is often like this:
- Select the request
- Copy to clipboard
- Switch to your reporting tool (Word, Markdown, Web App, LaTeX Editor,
$YOUNAMEIT) - Paste the request
- Switch back to Burp
- Select the response (or only part of it if body is too big and you ony want to show the issue)
- Copy to clipboard
- Switch back to the report
- Paste again
- Add context to explain the request / response
The Copy Request & Response Burp Suite extension adds new context menu entries that can be used to simply copy the request and response from the selected message to the clipboard.
The workflow can then look like this:
- Select what you want to copy from the context menu
- Switch to the reporting tool
- Paste
- Add context to explain the request / response
Much easier, right? 😉
From a technical view, this is probably the most boring Burp Suite extension. However, it allows you to spend more time on testing than documenting.
Features
The extension offers the following copy methods in the context menu of selected messages and request / responses:
- Copy entire request & response of selected message
- Copy entire request & response header
- Copy entire request & response header + selected response data
Screenshot:

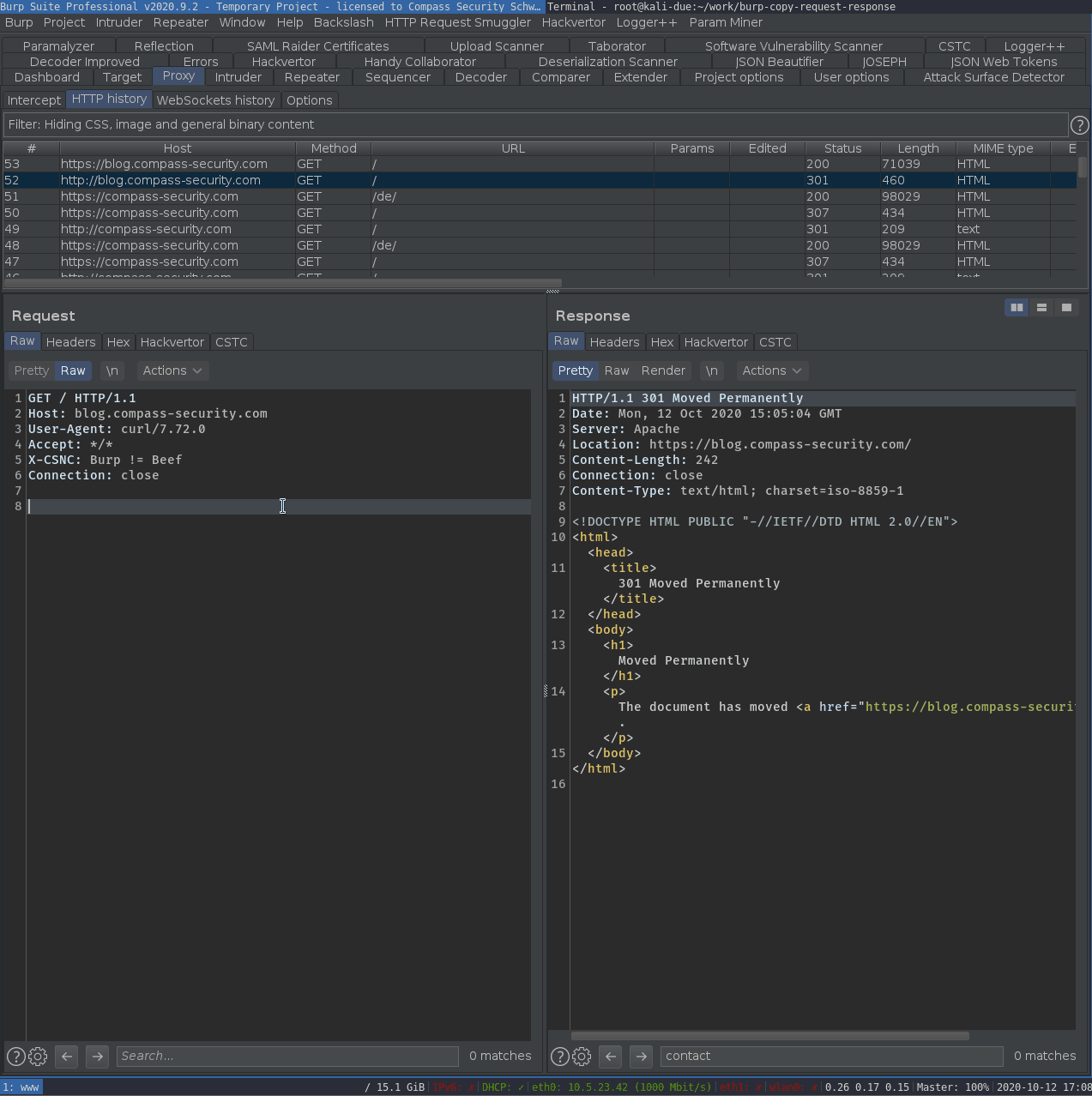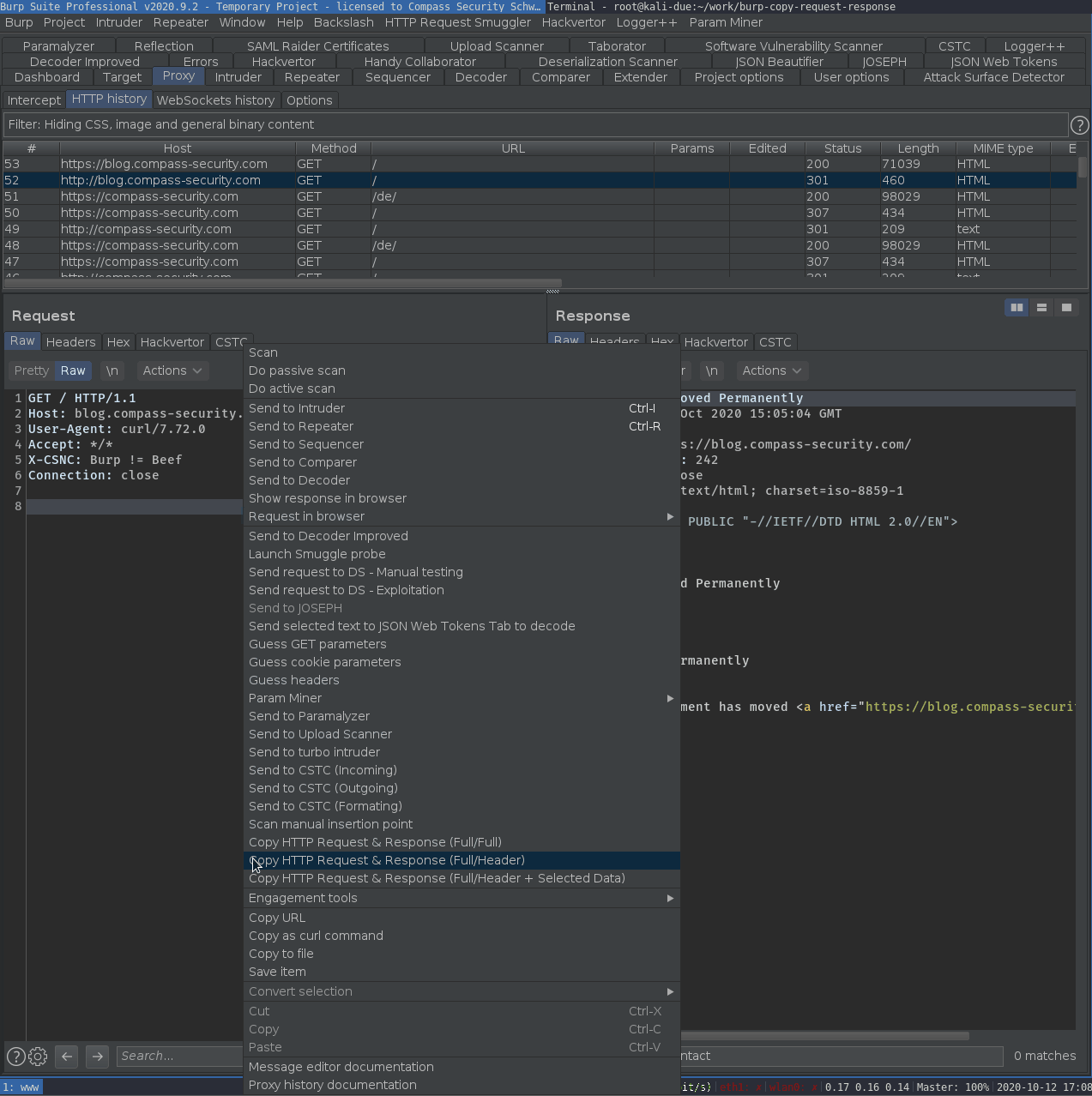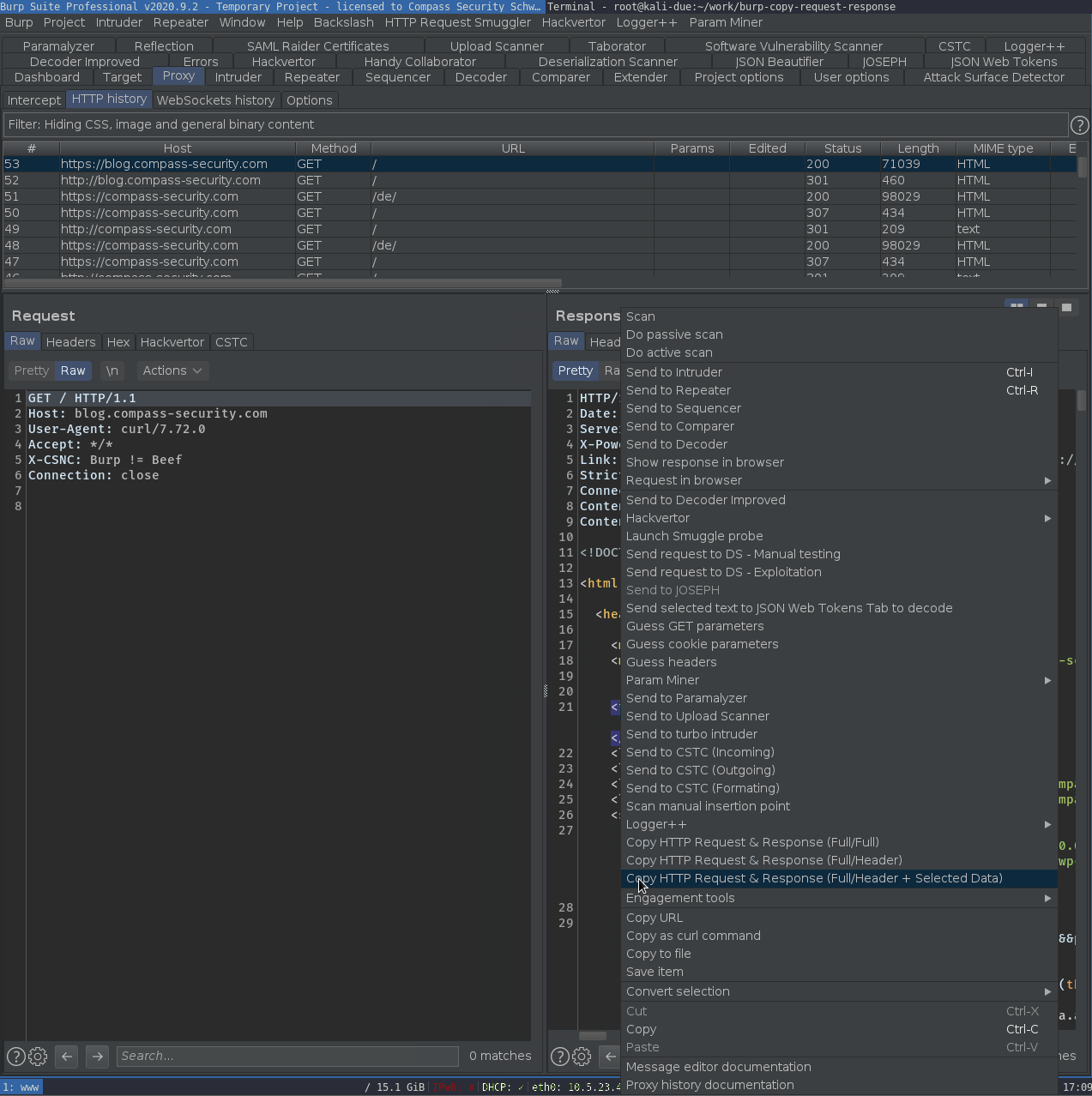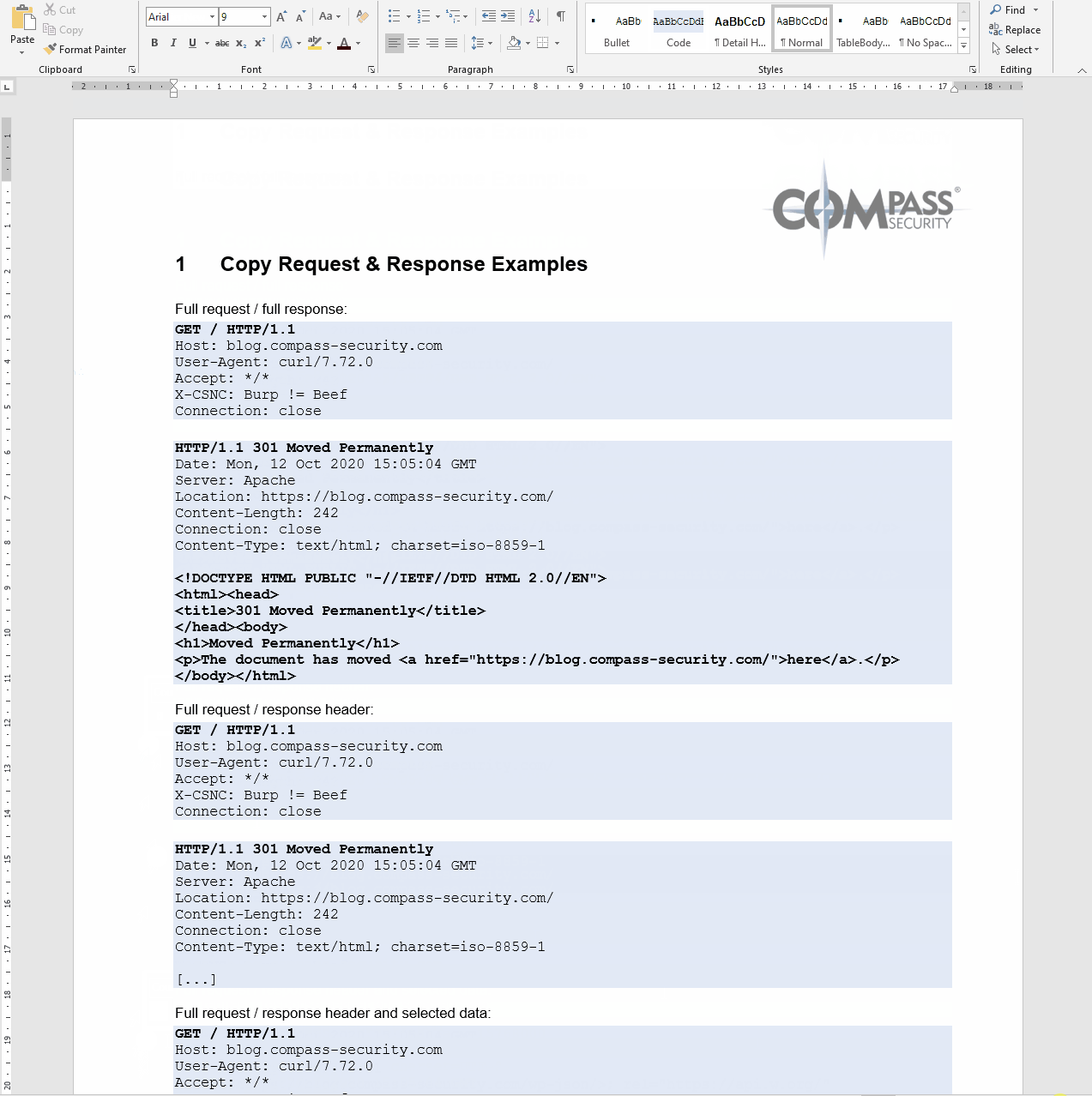
Demo
The following demo shows the 3 different copy methods:
Requirements
- Python environment / Jython for Burp Suite
Download & Installation
The extension can be found on GitHub: https://github.com/CompassSecurity/burp-copy-request-response.
See the PortSwigger documentation on how to install Python extensions: https://portswigger.net/support/how-to-install-an-extension-in-burp-suite.
The extension is also available in the Burp BApp Store: https://portswigger.net/bappstore/0d05f52c00a64cb2b2bea68744f6316c
Installation via BApp Store:
Known Issue
If you are testing in a virtual machine, the clipboard can be messed up when text is still selected after choosing a context menu entry. Therefore, when the copy method of selected response data is choosen, the copying process is started in a separate thread and copies the content after 2 seconds to the clipboard. So you have to wait 2 seconds before switching to your reporting tool.
I know, this is an ugly hack. Better ideas / fixes / PRs are welcome!
Questions
You can contact me (Twitter, E-Mail), write in the comments below or open a GitHub issue if you have any questions / ideas.
Happy hacking (and documenting 😉)!
Emanuel
Leave a Reply