We put more and more sensitive data on mobile devices. For many private conversations we use mobile applications, such as WhatsApp. This smooth access to the data and the Internet provides multiple benefits in our lives. On the other side, new attack vectors are created. Phishing messages do not need to be delivered in an email anymore and corporate data may be leaked without compromising a laptop if a smartphone was also used for work-related activities.
Because of the above, mobile devices also become a subject of forensic investigations. A possibility to quickly extract and analyze data disregarding of what device and operating system needs to be analyzed is crucial to provide a high-quality incident response. Cellebrite facilitates us in performing these types of investigations. Thanks to its immense number of supported devices and frequent releases with new enhancements, we can respond to an incident without unnecessary delays. While Cellebrite takes care of data extraction, we concentrate on aspects that cannot be yet automated, that is finding logical correlation between obtained data and analyzing the meaning of it within context of the incident.
Data Extraction
So how does the data-collection look like? To demonstrate the capabilities of Cellebrite we will dump all WhatsApp messages from a Google Pixel 3 device. Note that no exploits will be used in this process and the device needs to be unlocked.
After starting Cellebrite UFED on a forensic machine and connecting Pixel 3 to it, our device will be detected automatically.
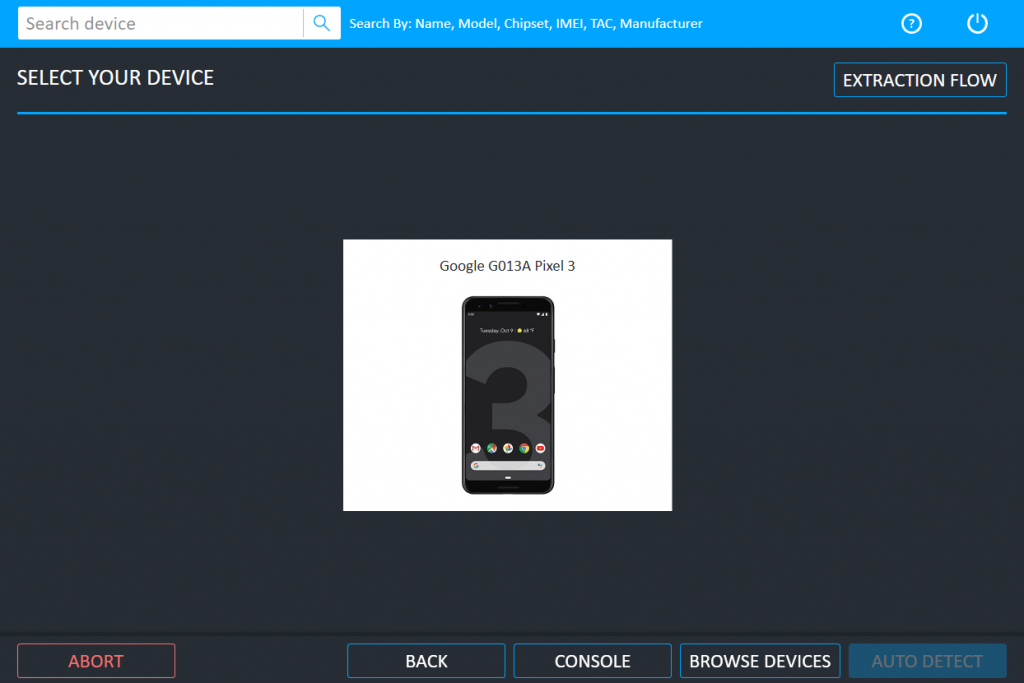
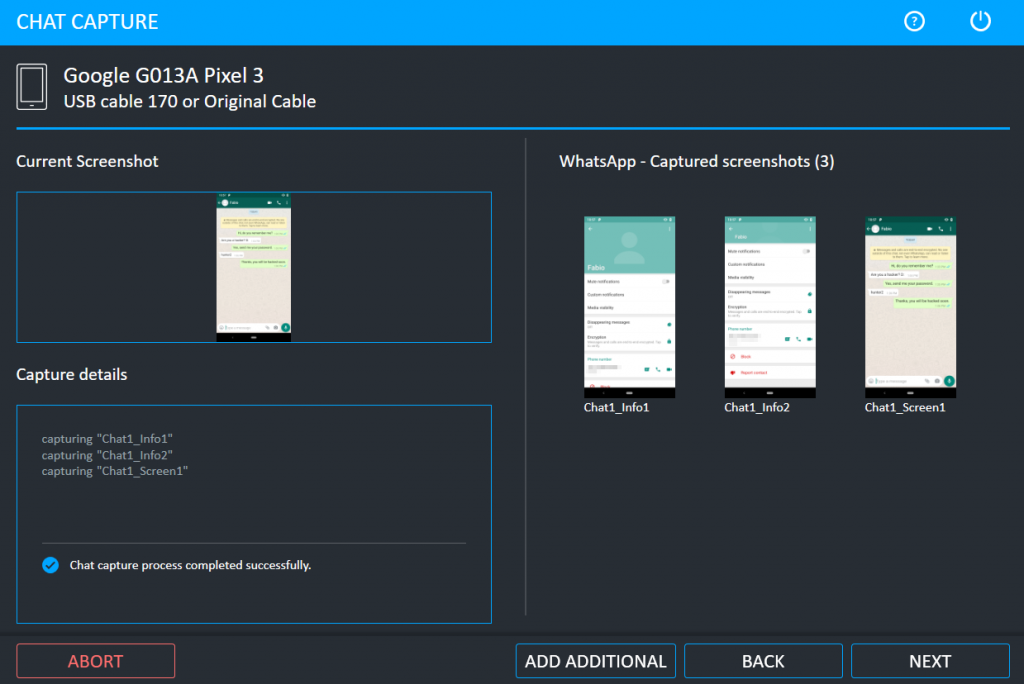
One of the suggested extraction types is chat capture, other allow to retrieve information such as files or call logs.
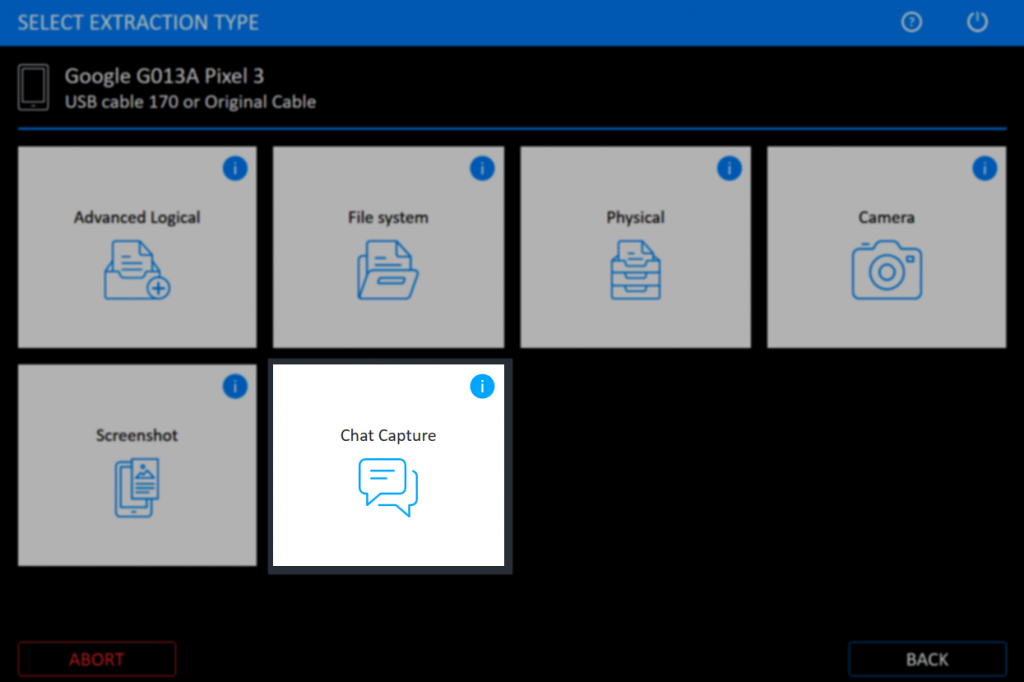
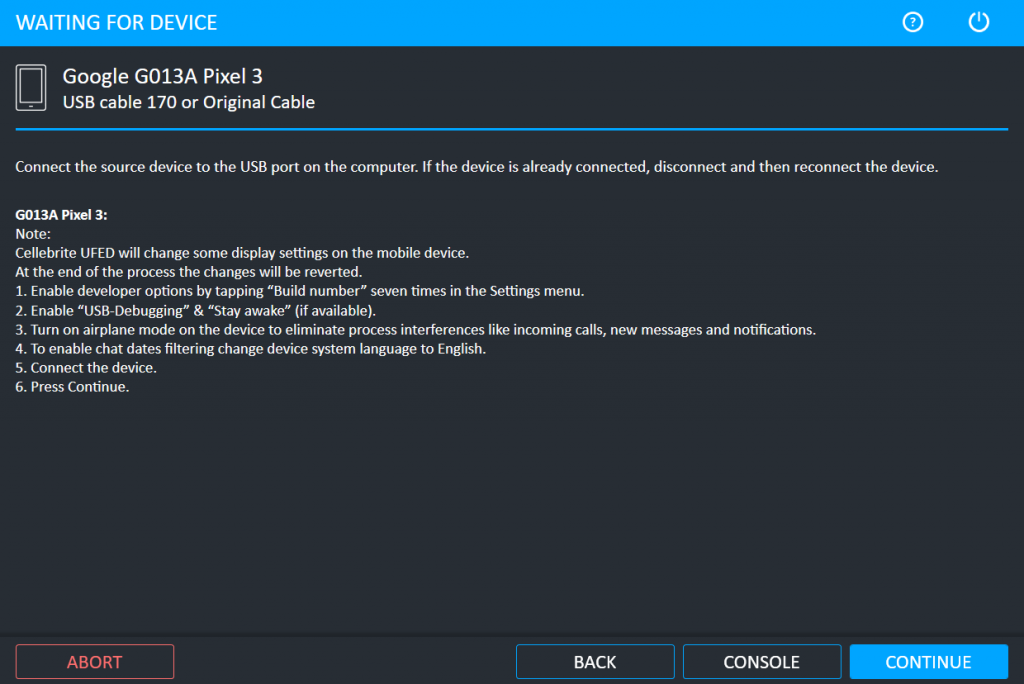
If an action needs to be performed on the device, the user is clearly instructed what to do.
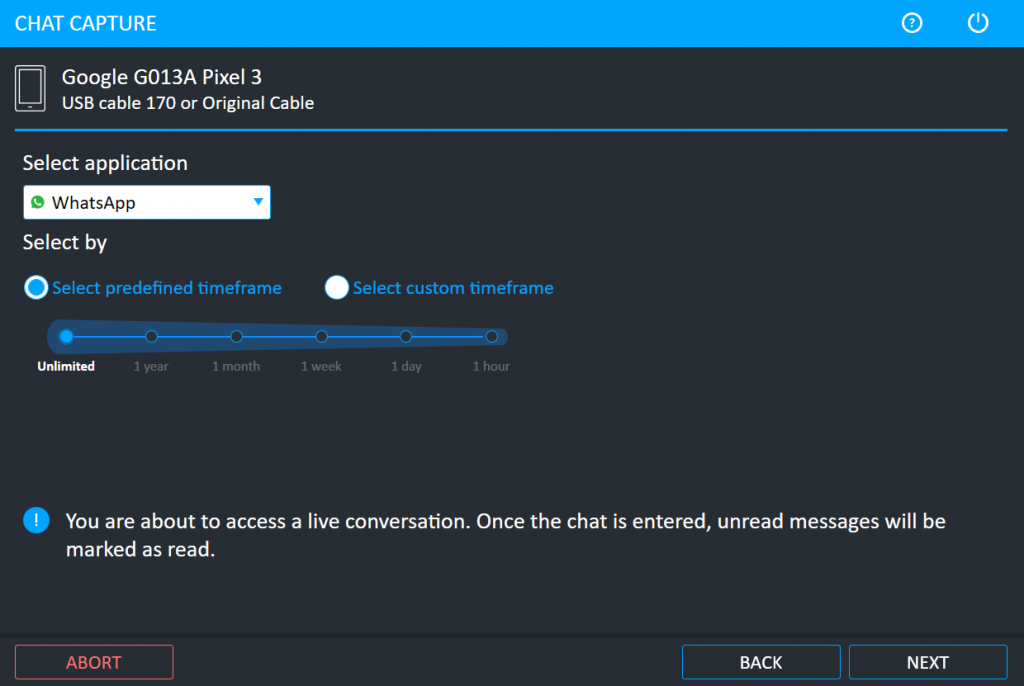
We choose the extraction properties and let Cellebrite do the extraction for us.
In just a few seconds Cellebrite automatically extracted WhatsApp conversations and made screenshots of them.
Note that it is not a vulnerability of WhatsApp that such an extraction is possible. Once we are able get the unlocked device, we have the same access rights as the device’s owner would have, in particular, we can use WhatsApp and other applications that are not additionally secured with another passcode or biometric authentication. After the WhatsApp conversations are extracted, we could analyze them conveniently without using the smartphone and search for example for a proof of unauthorized leakage of corporate data or the initial attack vector that caused the security incident. Depending on the type of the incident, it may be advantageous to disconnect the device from the Internet once the incident is noticed in order to prevent destroying or manipulating evidence present on the device from remote.
Conclusion
The version of UFED we own cannot do much beyond what could be done manually by a skilled mobile analyst. However, having such a device significantly speeds-up mobile forensic investigations as the analyst does not have to gather and interpret data from the relevant apps manually but can highly automate it and put it into context with a potential attack. Basically, UFED enables to focus on the “business side” of crime.
Besides that, considering physical extraction, a penetration tester or rather security analyst might find UFED useful to answer basic questions around the security of specific apps.
Leave a Reply