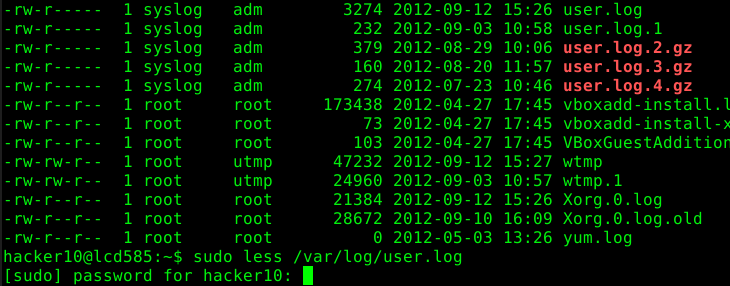
The following article describes common security issues regarding misconfigured sudoers’ files. The article focuses on a single entry which contains several security issues:
hacker10 ALL= (root) /bin/less /var/log/*
The article is split into the following five chapters:
- PART 1: Command Execution
- PART 2: Insecure Functionality
- PART 3: Permissions
- PART 4: Wildcards
- PART 5: Recapitulation
Define the allowed “sudo” commands carefully. Don’t allow commands to be run without knowing all the features it offers.
1. Disallow the execution of further commands by adding the “NOEXEC” flag:
hacker10 ALL= (root) NOEXEC: /bin/less /var/log/*
2. Check if the feature set of the command can be restricted. E.g. check for environment variables shown “LESSSECURE=1” for “less”:
#/etc/profile.d/lesssecure.sh LESSSECURE=1 readonly LESSSECURE export LESSSECURE
#/etc/sudoers Defaults env_reset, env_keep=LESSSECURE
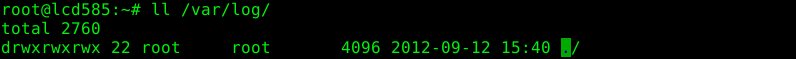
3. Check the file permissions carefully as this might render all your efforts useless:
4. Only use wildcards when you know that a breakout will be impossible.
The first example shows how to access the “/etc/passwd” file directly:
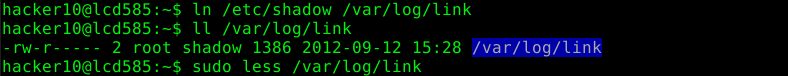
The second example shows how to open an additional file which can later be accessed by typing “:n” in “less”:
![]()
By following these rules you might avoid a malicious user to gain further privileges on your system.
Leave a Reply