When it comes to open source intelligence (OSINT), LinkedIn is a treasure trove of information. With millions of professionals voluntarily sharing details about their careers, connections, personal achievements, or keeping up to date with what is happening in their professional sphere, the famous networking platform is not to be underestimated when it comes to OSINT. In our field, LinkedIn is often used to gather a lot of information about a company during a red teaming assessment or social engineering exercise. Whether you’re assessing a company or a person of interest to craft a spear phishing email, LinkedIn offers valuable data if you know where to look. This article presents several ways to use OSINT methods with LinkedIn to get more information about a company or individual while maintaining operational security.
Operational Security
Before you start your analysis, consider how you’ll be accessing LinkedIn. If you are using your personal account, be aware that your searches and profile visits may be visible to the target. If discretion is required, you might consider checking your visibility settings. Nowadays not only the premium account but also the free account is allowed to visit pages in private mode:
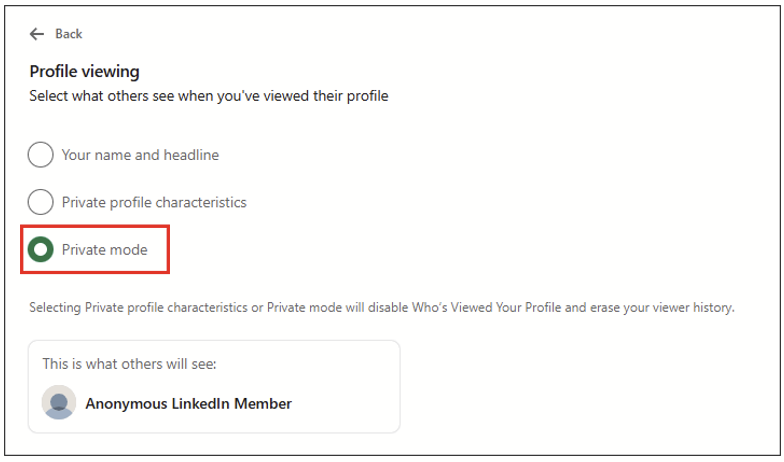
If you want to further minimise the risk of being identified, or simply don’t want to use your personal account for this type of activity, you can create a sock puppet account. This is a fake profile used during an investigation to hide your real persona. However, LinkedIn has robust fake account detection, so this task may be harder than it seems.
Tips and Tricks
Company Investigation
For corporate investigations, LinkedIn is invaluable because it provides a direct window into the dynamics of a company.
On the company profile, you can check:
- About – Provides company description, website, headquarters, and size
- Posts – Reveals recent announcements, partnerships, and events
- Jobs – May disclose technologies, processes or responsibilities through job announcements
- People – Lists current employees, where they live, where they studied, which competences they have and reveals company structure and key personnel
Insights
LinkedIn’s company profile can also provide insights into growth, partnerships, and leadership changes. Insights is a premium feature, but it still gives an overview of the company if you have a non-premium account. In the example below, it’s possible to see that the company had roughly the same number of employees for the last two years and that the median employee tenure is around 5 years.
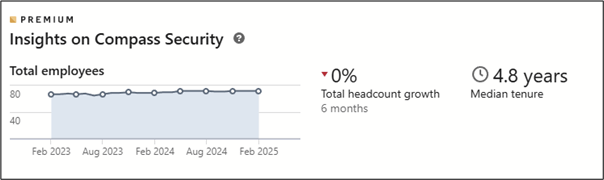
For example, if a company has lost several employees in the same year, this could mean that there are some internal dynamics that you’ll want to investigate (e.g. change of key personnel, mass layoffs for economic reasons, etc.).
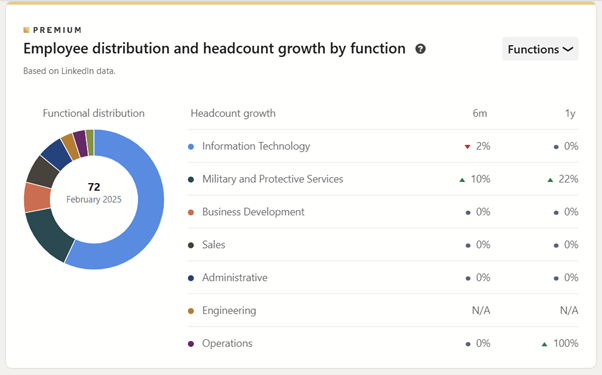
With the premium functionality it’s possible to see the distribution of employees by function. This information should be taken into account when defining an effective pretext for a generic phishing attack against the company.
People Investigation
Last name deanonymization
LinkedIn provides several privacy settings for its users, but sometimes there are workarounds to bypass them.
For example, some people want to hide their last name, but it’s still possible to guess it using the search functions. The image below shows a profile with the last name hidden.
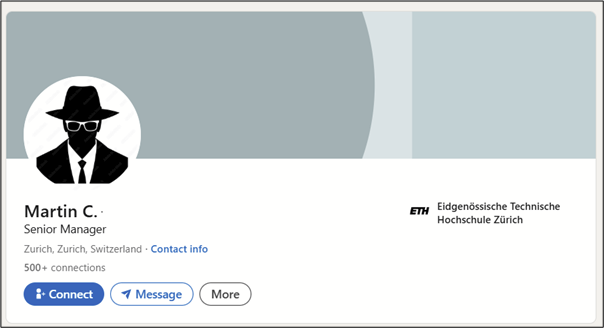
If the first letter of the last name is correct when searching for the person in the LinkedIn search bar, the profile will remain in the results:
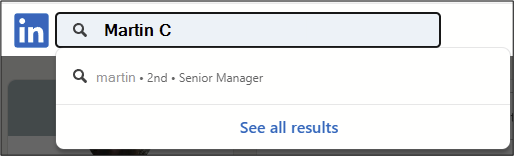
This is also the case if the second letter of the surname is correct, and so on. If one letter is not correct, the profile will disappear from the results:
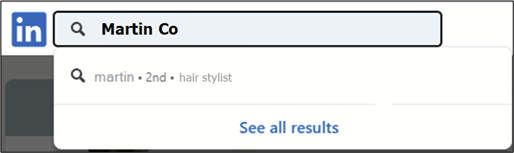
In this way it is possible to guess the surname character by character:
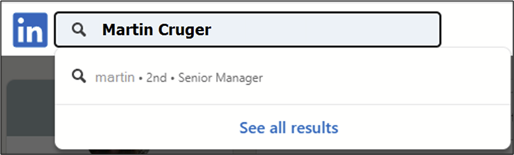
It might also be possible to deanonymize a last name in other ways. Some users chose their full name as their username. If that is the case, the LinkedIn URL shows their full name:
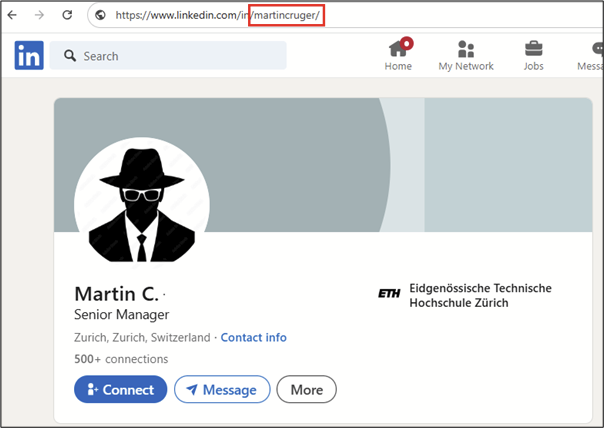
The username in the URL is not the only place where the last name can be found. Many people also share if they have passed a certification by uploading a picture of the successful exam to LinkedIn.
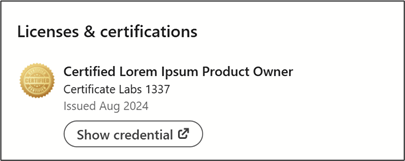
Often, the linked certification image includes the person’s full name:

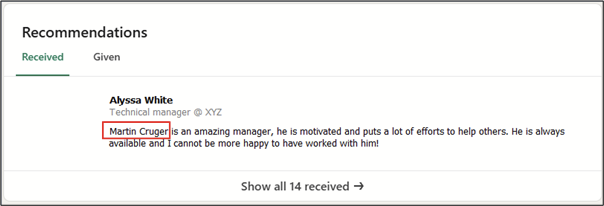
Another way to discover someone’s full name is to read the recommendations that other people have written about them. Sometimes the person writing the recommendation will refer to the recommended person by their full name, as you can see in the example below:
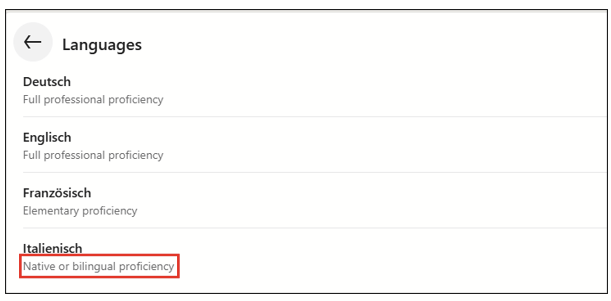
Preferred language
Depending on the phishing scenario, knowing the target’s native/preferred language will increase the likelihood of creating a more effective and convincing pretext. If the information is not explicitly disclosed by the language section…
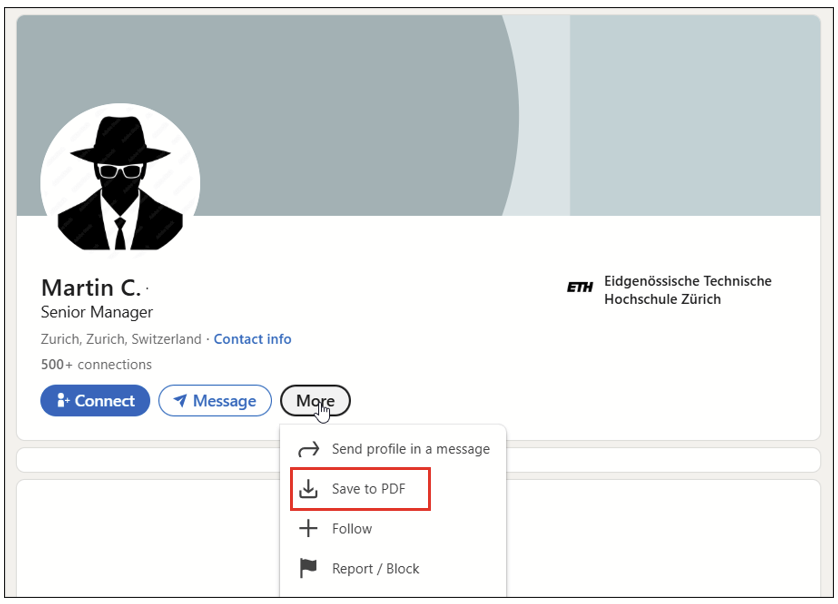
… there is another way to potentially find this information by simply downloading their LinkedIn profile as a PDF.
When a user first creates the LinkedIn account, the default language is automatically retrieved from the browser’s current language setting. For example, here is a LinkedIn account created with the default language set to German, which corresponds to the browser language setting:
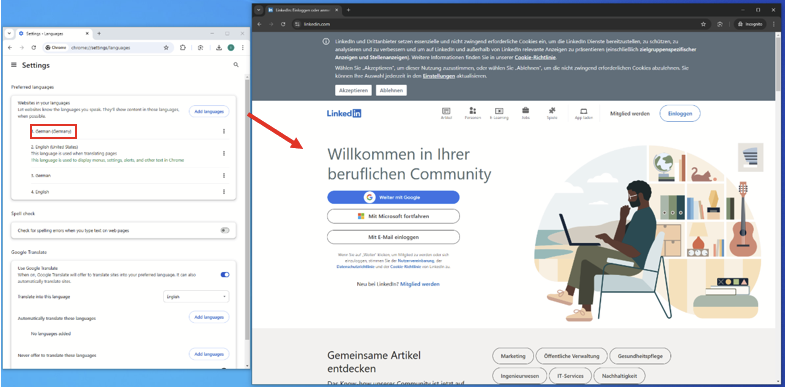
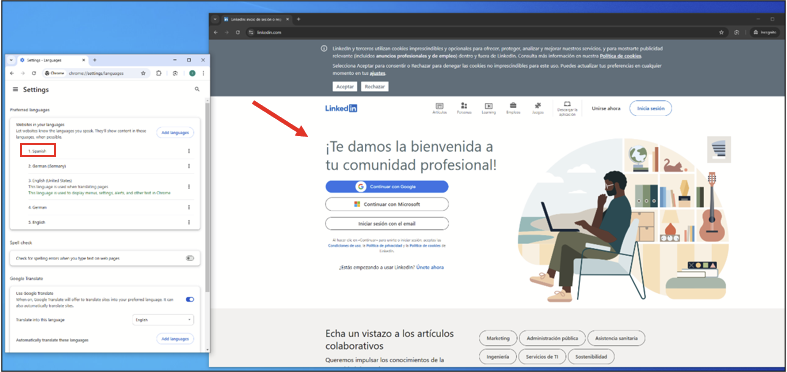
In this example the default language of the account will be Spanish:
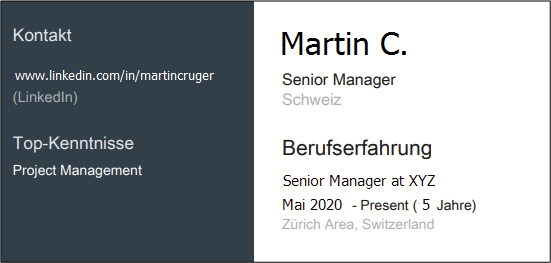
The language preference is leaked in the downloaded LinkedIn PDF profile because the file retains this information regardless of the viewer’s LinkedIn settings. When the downloaded PDF is opened, the titles are displayed in the user’s preferred language, in this case: German:
Verified accounts
Often on social media it is possible to verify the profile by proving to the platform that the person behind the profile is real. This is also possible on LinkedIn, but this feature could reveal some interesting information about the person.
The profile can be verified in three ways:
- Identity verification
- Workplace verification
- Education verification
The last two points are particularly interesting as they could be used for more targeted attacks. If someone verified their profile using their work or school email, it means that email is linked to their LinkedIn account. They could be getting LinkedIn emails like notifications and updates there. A malicious actor could use this information to create a phishing email that appears to be from LinkedIn and thus obtain other information such as LinkedIn credentials, if the user falls for it.
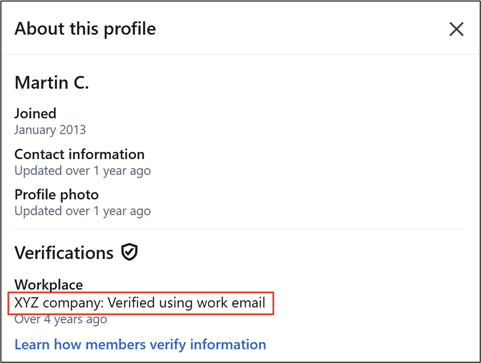
By clicking on the name of a LinkedIn profile, you can find out how a profile has been verified:
Pictures
Over the last decade, the increased use of social networking has led many people to post more and more of their personal lives online. An interesting aspect of this trend from an OSINT perspective is when a job or career change occurs. On their last day at a company, employees are usually excited to leave the old routine for a new adventure, and as a testament to their time there, some decide to post a picture of their office desk or badge on LinkedIn.

The badge contains a lot of information that may seem innocuous at first, but which gives an insight into the company. The image of the badge alone shows the layout of the document, the company logo and where the employee’s picture and name are written. Someone unfamiliar with the company could use this to make a convincing copy of the badge for social engineering purposes. In addition, some badges also contain the employee’s role within the company and various other identifying codes that could be exploited.
It’s then important to take a closer look at the pictures, because they can reveal a lot of information that might be overlooked at first glance!
Leveraging Third-Party Tools
While LinkedIn itself is a great resource, external tools can help with your research, especially if you don’t have a LinkedIn account. Because LinkedIn has privacy settings that can restrict some searches, these methods can often help you find someone’s profile more efficiently.
Google Dorks
Google Dorks can be a powerful tool for finding specific LinkedIn profiles, posts, or company information if you don’t have a LinkedIn account. To use Google Dorks for LinkedIn research, you can combine search operators with keywords to refine your results.
site:linkedin.com inurl:"/in/" "<company_name>" -inurl:"<company_name>"
This restricts the search to LinkedIn profiles (/in/ denotes personal profiles) and ensures that “compass security” appears on the page and within the URL (-inurl).
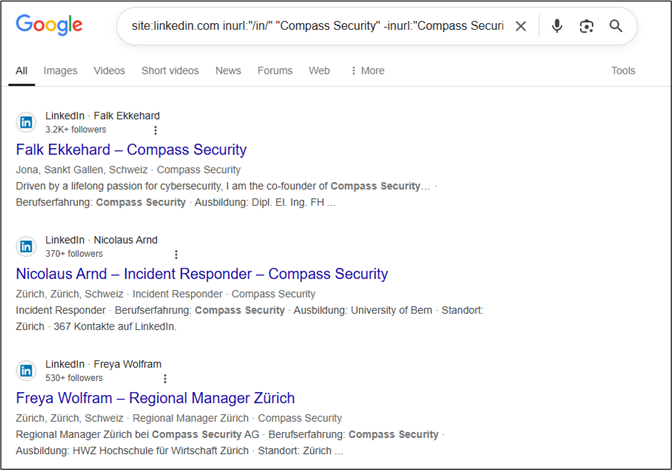
If what you are looking for is a company, the Google Dork will have to be adjusted to use /company/ instead of /in/:
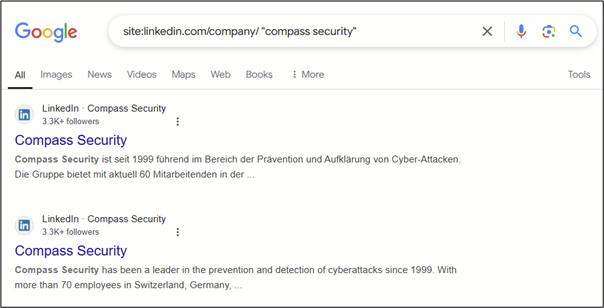
You can also exclude terms with - or search for exact phrases using quotation marks "". These tricks help you get around LinkedIn’s internal search limitations and find precise information quickly. Have fun finding more!
Outlook
If you have a valid email address of the target, you may be able to see if it is linked to a LinkedIn profile. This can provide additional information to create a more effective pretext for a potential phishing attack.
To do this, you should first add a new contact in Microsoft Outlook online with the target’s email address.
If LinkedIn integration is enabled on your site and the target has the “Microsoft profile card” setting enabled…
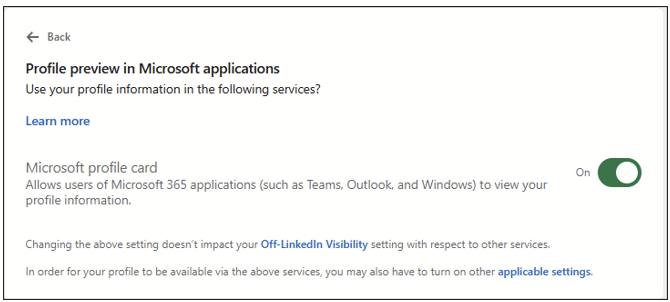
…then when you click the LinkedIn button, you’ll see which account the email address is associated with:
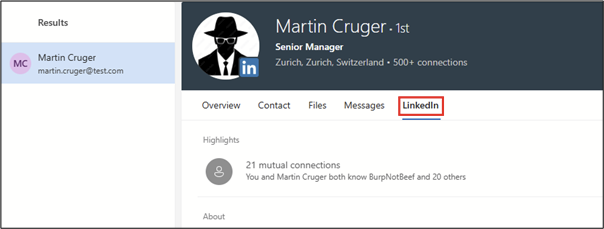
Wayback Machine
The Wayback Machine can help you see the past versions of LinkedIn profiles or company pages. It can be useful for finding a LinkedIn profile if it has been deleted, changed, or made private. To use it, go to https://web.archive.org or https://archive.is and paste the LinkedIn profile URL of the person or company to see if past snapshots exist. If the profile was public when it was archived, you may be able to retrieve details such as contact information, work history, or connections. If you don’t know the exact LinkedIn URL, you can also check archived company or personal websites that may have linked to the profile.
Final Thoughts
LinkedIn is a valuable resource for OSINT, offering a wealth of information about people and companies. With the right approach, you can uncover job roles, company structure, connections, languages, and even personal details that help in gathering information for assessments or creating effective social engineering pretexts.
While this is useful for offensive security purposes, be cautious about what you share and who can view it. Adjust your privacy settings to control access, or better yet, limit the amount of information you share in the first place.
Leave a Reply