Microsoft Azure is probably the most widely used cloud platform in Switzerland, powering businesses of all sizes, from startups to multinational companies. According the the official Microsoft page over 95% of Fortune 500 companies rely on Microsoft Azure in one form or another. With this industry-wide adoption, it has become a critical component of modern-day IT infrastructure. However, as more and more companies migrate to cloud or cloud-local hybrid infrastructure, the security risks that go along with these environments increase.
In this post, we will explore common Azure Identity & Access Management (IAM) as well as Entra ID vulnerabilities and misconfigurations, why they pose a threat and how to mitigate them. Whether you are an IT admin, security engineer or cloud architect, understanding these risks helps keeping your company’s cloud assets secure.

What is Identity & Access Management (IAM)?
Identity and Access Management (IAM) is the heart of every cloud environment. Comparable functionality and security features are present in every cloud environment such as Microsoft Azure, Amazon AWS or Google Cloud. IAM is a security framework that controls who can access which cloud resource and what actions they can perform. It ensures that the right users and services have appropriate permissions to perform their respective tasks and duties while preventing unauthorized access.
What is Microsoft Entra ID?
Microsoft Entra ID (formerly known as Azure Active Directory) is Microsoft’s cloud-based identity and access management service. It is used to manage user identities and control their access to applications and resources as well as enforce security policies across the environment.
Entra ID and Azure IAM misconfigurations can leave organizations exposed to several cybersecurity threats including but not limited to data breaches, ransomware attacks as well as compliance violations. Cybercriminals are often targeting cloud environments and aim to exploit common vulnerabilities that can often be prevented with proper cloud security controls.
The 5 Azure IAM / Entra ID Security Risks You Can’t Ignore
Excessive IAM Permissions
Definition
This occurs when users, service principals or applications are assigned roles with more privileges than necessary. Most commonly privileged roles such as Owner or Contributor are used when roles with fewer privileges could have sufficed.
Risk
This allows accounts to access critical functionality or modify resources. If an account with excessive permissions is compromised an attacker can leverage these for privilege escalation as well as lateral movement through the environment. Unauthorized modifications can lead to data breaches, downtime or even resource deletion.
Mitigation
Roles should always be assigned bearing in mind the least privilege principle. High-privileged roles should only be granted with caution. Duties should be segmented and roles should be assigned only as required. Perform regular audits of custom roles as well as role assignments to ensure permissions remain appropriately assigned.
Multi-Factor Authentication Not Enforced
Definition
This vulnerability occurs when Azure accounts are not configured to use or enforce Multi-Factor Authentication (MFA) and rely solely on single-factor authentication like passwords.
Risk
Without MFA, compromised credentials can grant attackers unfettered access to Azure resources, leading to potential data breaches, unauthorized modifications, and lateral movement within the environment.
Mitigation
MFA should be enforced across all accounts, but especially for privileged access. This can be done by implementing conditional access policies, regularly reviewing authentication settings as well as educating users about the importance of strong authentication methods.
Furthermore, privileged Azure accounts should have dedicated conditional access policies such as compliant company devices, IP whitelisting, etc. in addition to MFA.
Enable MFA for users: https://learn.microsoft.com/en-us/partner-center/security/mfa-for-users
Unused or Stale Accounts Still Active
Definition
This can occur when user or service accounts are no longer in use, such as accounts belonging to former employees, expired vendors or obsolete services, remain active in Entra ID without proper deactivation or monitoring.
Risk
The resulting unused accounts pose a significant security risk, as they can be compromised without detection, providing an easy entry point for attackers. If credentials are leaked or stolen, the accounts could be used for unauthorized access, privilege escalation or lateral movement within the cloud environment.
Mitigation
Regularly audit and disable unused accounts using Entra ID Access Reviews and automate lifecycle policies. Strict offboarding procedures should be implemented to remove or at least disable accounts when employees leave. Furthermore, Conditional Access Policies can be used to block inactive accounts. To detect suspicious logins from old or dormant accounts Azure Identity Protection can be utilized.
Azure Identity Protection Documentation: https://learn.microsoft.com/en-us/entra/id-protection/overview-identity-protection
In the Entra ID portal risky users and sign-ins can be checked in the Security – Reports section:
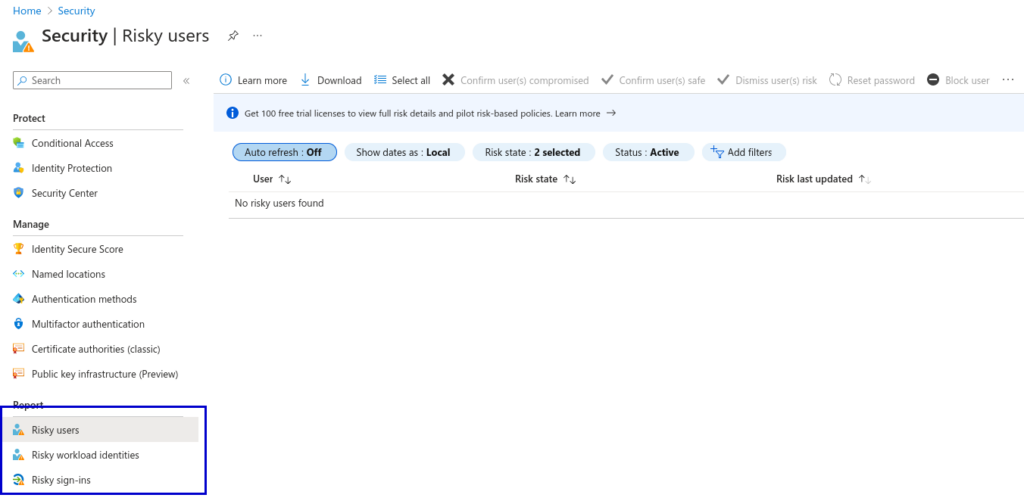
Guest Access Remains Enabled
Definition
When Azure guest access is left enabled, external users can be added to your Azure environment. These external users can then also invite further external users without strict controls.
Risk
Enabling guest access can inadvertently grant external entities access to sensitive internal resources. This increases the risk of unauthorized data exposure, lateral movement as well as potential breaches through third parties.
Mitigation
If your business does not require guest access by external business partners, guest access should be disabled. If external collaboration is needed, strict invitations should be enforced. Furthermore, conditional access controls should be implemented for the guest accounts. Regular audits of the guest accounts and their permissions should be performed, to ensure only authorized users are granted access.
Disabling that guest users can invite further guest users via “External collaboration settings” in the Entra ID portal:
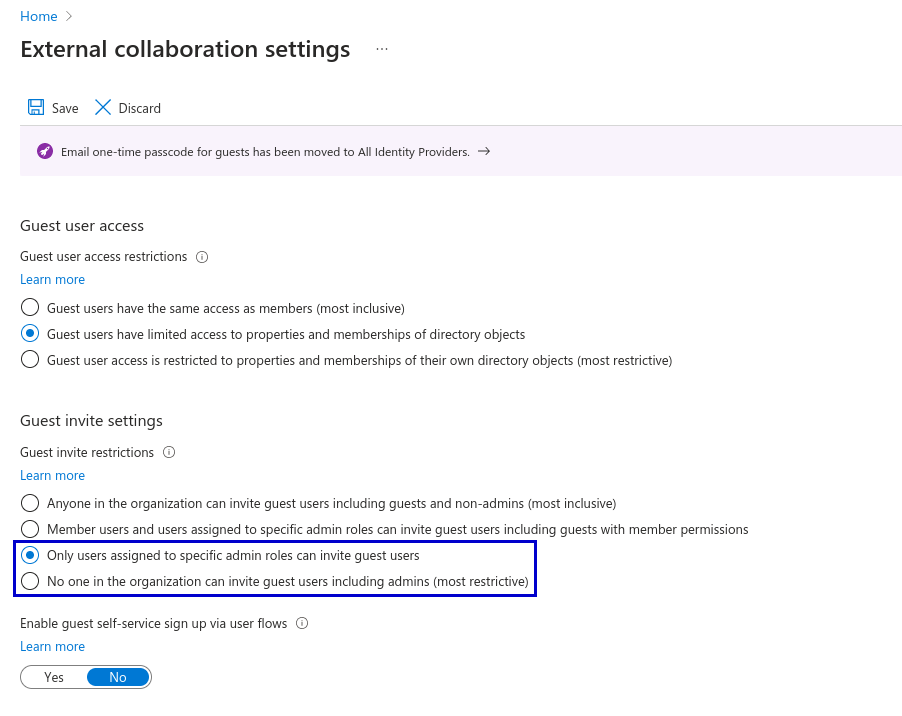
Not Using Privileged Identity Management (PIM) for Azure
Definition
When Azure Privileged Identity Management (PIM) is not enabled for high-privilege roles such as Global Administrator or Owner, permanent administrative access is possible instead of just-in-time (JIT) or approval-based role activation.
Risk
Without PIM, privileged accounts always have elevated access. This increases the risk of privilege escalation and lateral movement upon credential theft or via insider threats. If an attacker compromises a high-privilege account, unrestricted changes to resources can be performed, sensitive data can be stolen or security controls can be disabled.
Mitigation
Enabling Azure PIM to enforce just-in-time access, requires users to activate high-privilege roles only when needed. Approval workflows, time-bound access and notifications for role activations can further improve the security of high-privilege access.
How to set up PIM for Azure: https://learn.microsoft.com/en-us/entra/id-governance/privileged-identity-management/pim-getting-started
Take-aways
Securing Azure environments requires proactive Identity and Access Management practices to prevent common misconfigurations. As outlined above multiple vulnerabilities can arise from neglecting IAM best practices. Regular audits should be performed and the shown mitigation strategies should be implemented to reduce security risks.
By implementing strong IAM controls, businesses can fortify their cloud security posture and mitigate common attack scenarios.
In today’s threat landscape, staying ahead of IAM misconfigurations is not just best practice; it’s essential.
Further Reading and Resources
Over 95% of Fortune 500 companies use Microsoft Azure: https://azure.microsoft.com/en-us/resources/cloud-computing-dictionary/what-is-azure
Overprivileged Permissions: https://learn.microsoft.com/en-us/security/zero-trust/develop/overprivileged-permissions
Least Privilege Access: https://learn.microsoft.com/en-us/entra/identity-platform/secure-least-privileged-access
Access Reviews: https://learn.microsoft.com/en-us/entra/id-governance/access-reviews-overview
Conditional Access: https://learn.microsoft.com/en-us/entra/identity/conditional-access/overv
Leave a Reply