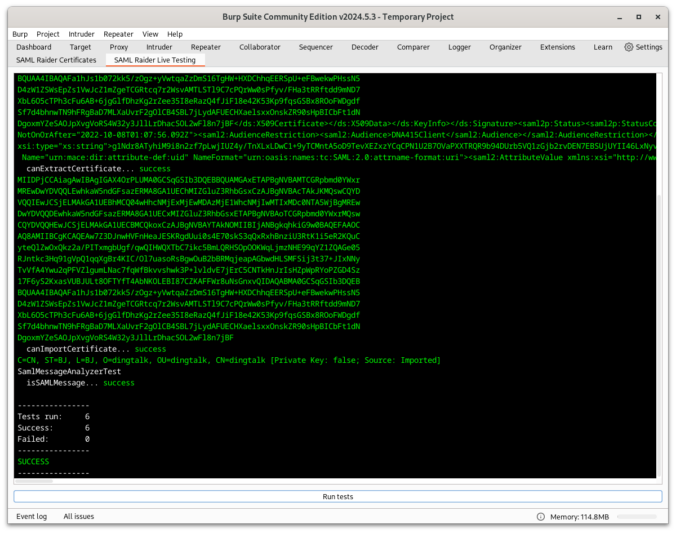
SAML Raider is a Burp Suite extension and the tool of choice for many pentesters for testing SAML infrastructures. This blog post should give a brief introduction to what has changed in the new version 2.0.0. From Improving developer and user experience to bug fixes.
Compass Security Blog
Offensive Defense
TL;DR Release of Conkeyscan – A Confluence Keyword/Secret Scanner, which is tailored towards pentesters. Secrets Everywhere Many companies, especially larger ones, need to store knowledge in a centralized way. A wiki is the usual choice for this. One product that is frequently used for this purpose is Confluence from Atlassian. Similar to how sensitive data […]
To identify and understand threats and weaknesses of smart contracts, it is important to be at least familiar with common smart contract bugs and vulnerabilities, how they can be leveraged by a malicious attacker, and how these issues can be mitigated.
This blog article aims to raise awareness about common smart contract vulnerabilities and their corresponding mitigation strategies.
Introduction Last year, I attended a job fair organized by the Association of Computer Science Students at ETH Zürich. It was a rewarding experience to be able to share my day-to-day work in a field I am so passionate about. We got to talk to numerous students at different stages of their studies, as well […]
At Compass Security, we recently launched our managed bug bounty service. We openly invite hunters to probe our publicly exposed services for vulnerabilities. In return for their valuable feedback, we offer monetary bounties up to CHF 5000. This blog posts presents an interesting vulnerability found by a hunter on the bug bounty program of our subsidiary, Hacking-Lab.
Authentication and authorization are critical components of any application. Various standards and frameworks have been developed to facilitate the development of such components and make applications more secure. Among them, JSON Web Tokens (JWTs) have become popular choice over the years.
In this article, we discuss commons flaws in JWT-based authentication and present our extension to automatically check for these issues in Burp: JWT-scanner.
This is hopefully the most useless blog post you will read this year as this post will detail our experience dealing with ransomware cases. It is one of the most common reasons why we get called in to help and it has become a big business. Chainalysis, for example, has tracked $1.1 billion in ransomware […]
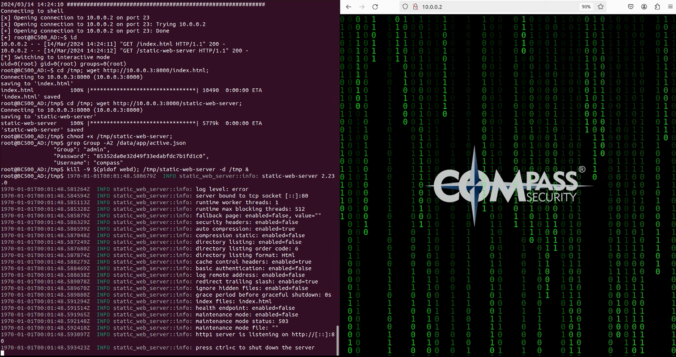
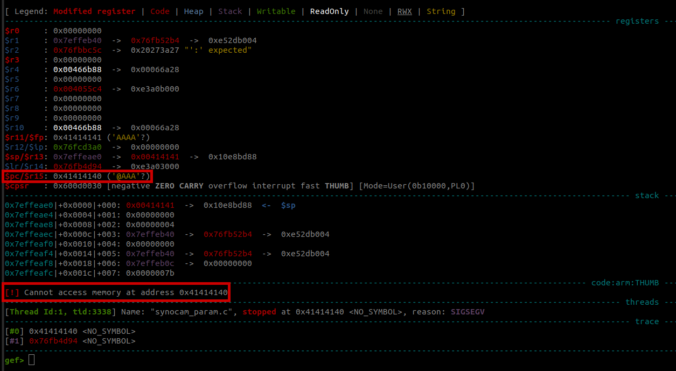
In this final part of this series, we are finally going to explain how the stack-based buffer overflow vulnerability can be exploited to gain unauthenticated remote code execution (RCE) on the Synology BC500 camera.
In this fourth part of the series, we analyze the memory corruption identified previously and manage to overwrite the program pointer!
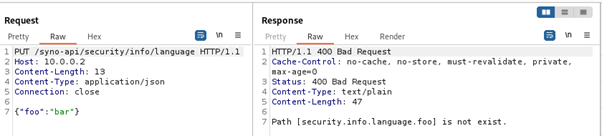
In this third part of the series, we focus on the exposed web services running on TCP ports 80 and 443.
Since a valid exploit chain must achieve code execution without prior authentication, we focus on the available functionality that can be accessed without authentication.
© 2024 Compass Security Blog