Something a bit wild happened recently: A rival of LockBit decided to hack LockBit. Or, to put this into ransomware-parlance: LockBit got a post-paid pentest. It is unclear if a ransomware negotiation took place between the two, but if it has, it was not successful. The data was leaked.
Now, let’s be honest: the dataset is way too small to make any solid statistical claims. Having said that, let’s make some statistical claims!

The Numbers
The leak shows that LockBit is working with 35 different affiliates. Affiliates are basically resellers of LockBit’s encryption tool. LockBit, as the Ransomware-as-a-Service provider only provides the en- and decryptor plus the darknet platform. The actual attacks are done by so-called affiliates based on a commission basis.
The leak contained in total 208 ransomware chats from December 18, 2024 to May 29, 2025, totaling 4423 messages. Out of those 208 conversations, 16 resulted in a payment, around 8%. Of the 97 chats in which the victim contacted the attackers at all, 17% resulted in a ransom payment.
This is a notably lower success rate than typically reported in broader ransomware statistics. Possible explanations include incomplete data, redaction or deletion of successful cases by LockBit
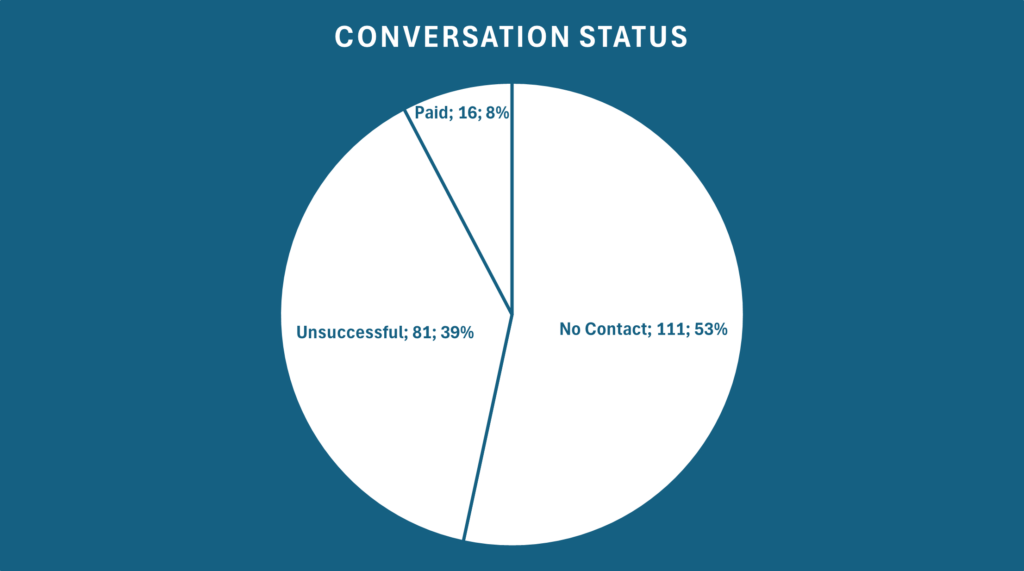
Also worth noting: Every single one that paid got the decryption tool. But two times LockBit’s manageres had to intervene.
Ransom Demand vs. Final Payments
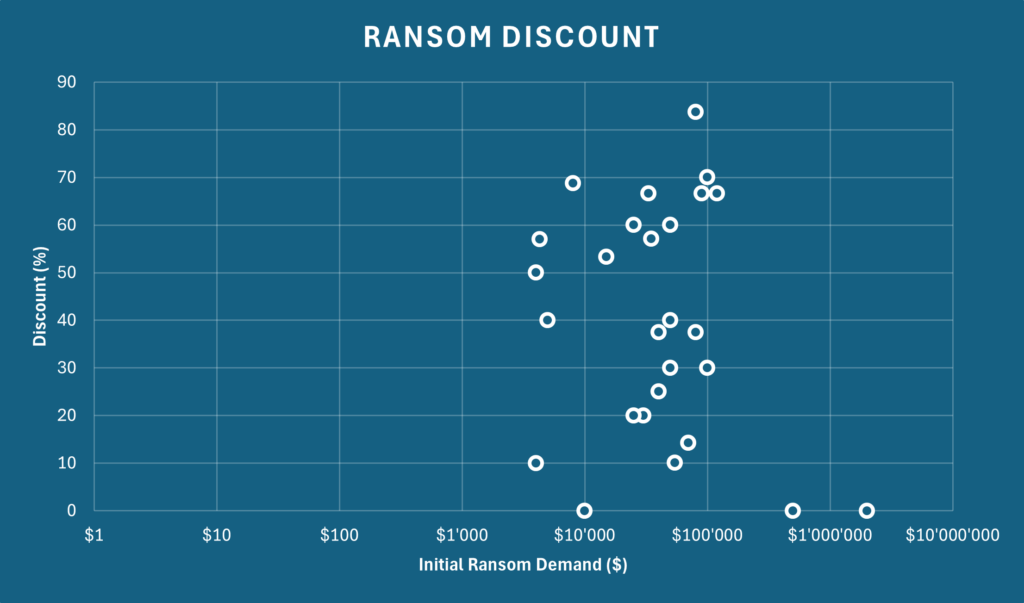
The initial ransom demands ranged from $2,000 to $2,000,000. While some victims paid the full amount, others were able to negotiate substantial discounts, some up to 80% off the original demand.
Cryptocurrency Preferences
Bitcoin remains the primary payment method requested by LockBit affiliates. All affiliates asked for BTC. Despite suggesting some alternatives, most affiliates wanted Bitcoin, except for one that would have taken Monero. Despite Monero offering increased privacy, Bitcoin’s broader infrastructure, liquidity, and exchange support make it the preferred choice for most affiliates.
MTTD (Median Time To Decryptor)
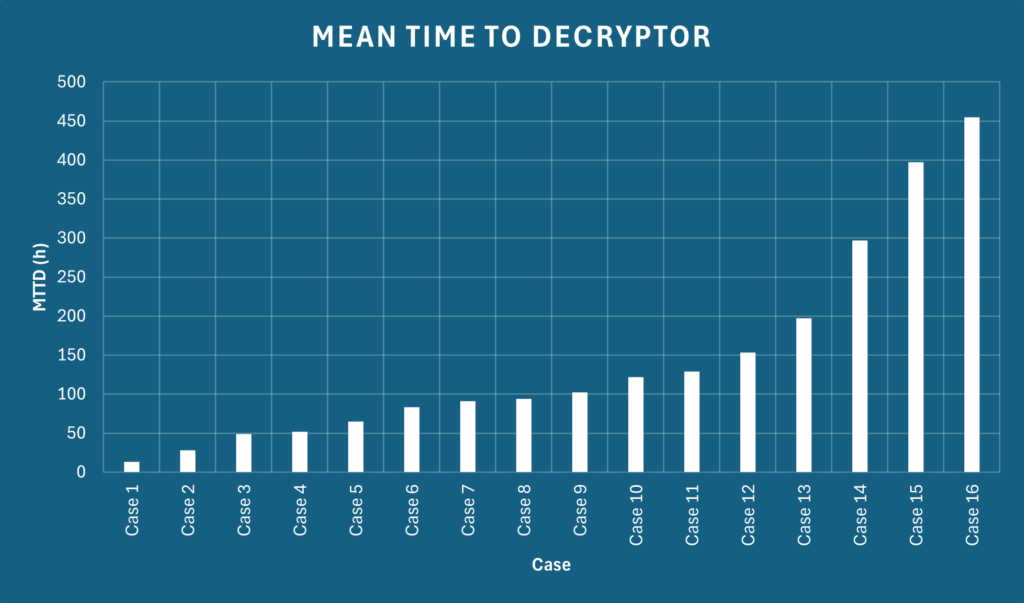
The time from initial victim contact to receipt of a decryption tool varied widely. Of the 17 who paid, the fastest got theirs in just 13 hours, while the slowest took 455 hours (almost 19 days).
The median delivery time was 94 hours, or just under 4 days.
It is important to note, however, that receiving a decryptor does not mean immediate business recovery. Additional time and resources are required for full restoration of systems and data
Victim Profiling
While some affiliates used standardized messaging and demands, others tailored their negotiation strategies based on information from the victim’s stolen data. In one case, a victim claiming financial hardship was presented with their own bank statement. In another, the ransom demand was calibrated according to the victim’s reported cyber insurance coverage.
These examples demonstrate that some affiliates conduct due diligence before or during negotiations to maximize payout.
Conclusions
This breach into LockBit’s operations offers a rare glimpse into the internal mechanics of a major ransomware group. The data provides insight into how affiliates operate, how ransom amounts are negotiated, and how payments are handled.
The primary takeaway for organizations is clear: prevention is significantly less costly than remediation. Investing in cybersecurity measures, including secure architecture, threat detection, employee training, and incident response plans, can reduce the likelihood of an attack and potential damage if one occurs.
Leave a Reply