When it comes to open source intelligence (OSINT), LinkedIn is a treasure trove of information. With millions of professionals voluntarily sharing details about their careers, connections, personal achievements, or keeping up to date with what is happening in their professional sphere, the famous networking platform is not to be underestimated when it comes to OSINT. […]
Compass Security Blog
Offensive Defense
Page 2 of 3
Renovate is an OSS CLI/bot that updates your software dependencies automatically. It is usually integrated into the CI/CD process and runs on a schedule. It will create a Pull Request / Merge Request (PR/MR) to your repository with dependency updates. It can optionally auto-merge them. If you host it for several repositories or an organization, it […]
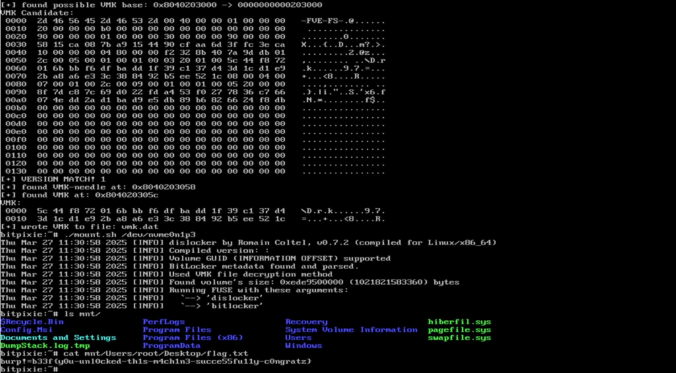
Depending on the customer’s preference, possible initial access vectors in our red teaming exercises typically include deployment of dropboxes, (device code) phishing or a stolen portable device. The latter is usually a Windows laptop protected by BitLocker for full disk encryption without pre-boot authentication i.e. without a configured PIN or an additional key file. While […]
TL;DR: PowerShell tool to enumerate Entra ID objects, assignments and identify highly privileged objects or risky configurations. https://github.com/CompassSecurity/EntraFalcon Entra ID environments can contain thousands of objects – users, groups, service principals, and more – each with unique properties and complex relationships. While manual reviews through the Entra portal might be feasible in smaller environments, they […]
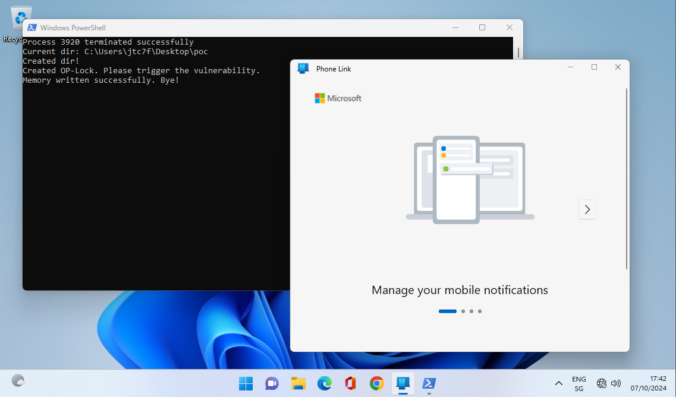
As a pentester you are sometimes thrown into projects where you have no idea where you are going to end up. This project was one of those where you were given a customer laptop and the aim was to “find something interesting”, perhaps a misconfiguration on the customer side. The problem was that the laptop […]
Red Team Operator. A hype-tagged role tag for which one question hits our corporate LinkedIn inbox very often. “Hey there, how can I become a Red Team Operator? Yours sincerely, a recent graduate.” To us, this is like asking how to become a regular starter on a Premier League football team. There’s nothing wrong with […]
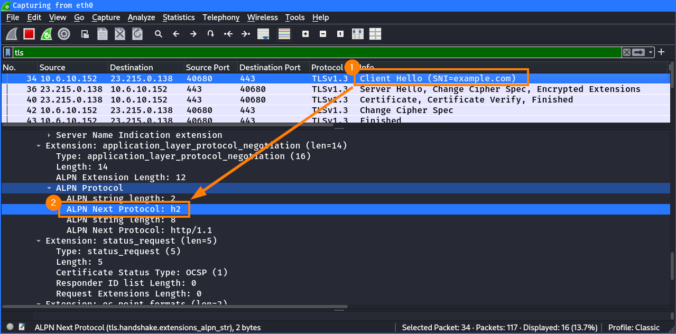
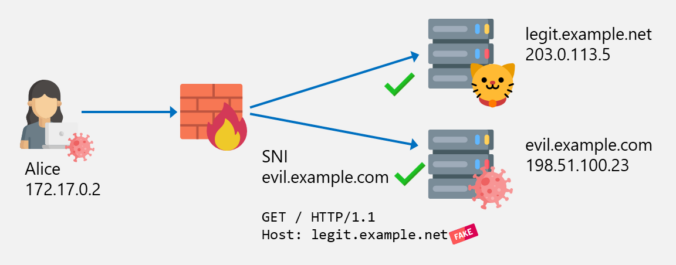
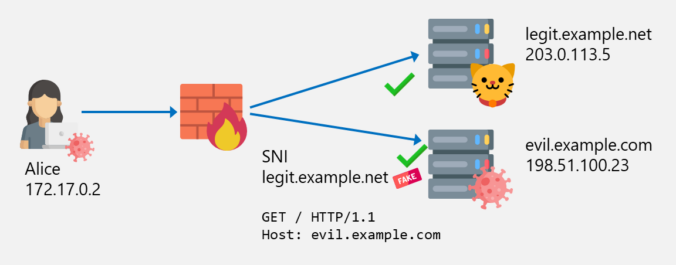
In the previous posts of this series, we looked at different ways to bypass web filters, such as Host header spoofing and domain fronting. As we’ve learned, these techniques can be detected by proxies employing TLS inspection, by checking whether the hostname in the SNI matches the one in the HTTP Host header. If they […]
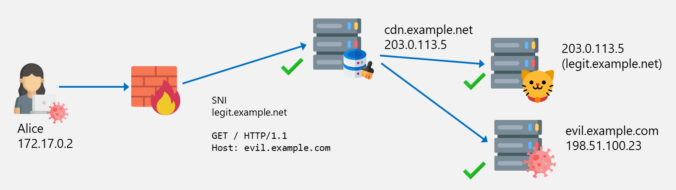
The last two blog posts in this series were about SNI spoofing and Host header spoofing. We also learned that the latter is addressed by some vendors with a technique called “Domain Fronting Detection”. But what exactly is domain fronting? This will be explained in this blog post.
In the last post about bypassing web filters, I discussed how SNI spoofing works and how this can also be prevented by web filters. This post is about another bypass technique called Host Header spoofing.
This is the first part of a series of blog posts about techniques to bypass web filters, looking at increasingly advanced techniques with each part.
The first part is about how SNI spoofing can be used to bypass web filters.
© 2026 Compass Security Blog