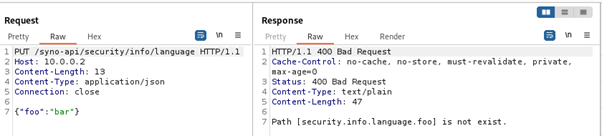
In this third part of the series, we focus on the exposed web services running on TCP ports 80 and 443.
Since a valid exploit chain must achieve code execution without prior authentication, we focus on the available functionality that can be accessed without authentication.