NTLM is the legacy authentication protocol in Windows environment. In the past few years, I’ve had the opportunity to write on this blog about NTLM Relaying to DCOM (twice), to AD CS (ESC11) and to MSSQL. Today I will look back on relaying to HTTPS and how the tooling improved.
Compass Security Blog
Offensive Defense
Introducing a certipy parse command to perform stealthy offline AD CS enumeration based on local registry data.
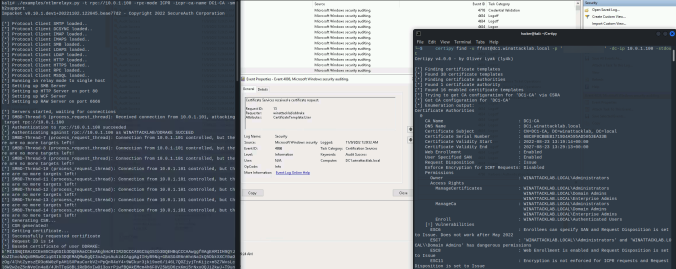
In June last year, the good folks at SpecterOps dropped awesome research on Active Directory Certificate Services (AD CS) misconfigurations. Since then, we find and report these critical vulnerabilities at our customers regularly. One of these new attack path is relaying NTLM authentication to unprotected HTTP endpoints. This allows an attacker to get a valid […]
© 2026 Compass Security Blog