NTLM is the legacy authentication protocol in Windows environment. In the past few years, I’ve had the opportunity to write on this blog about NTLM Relaying to DCOM (twice), to AD CS (ESC11) and to MSSQL. Today I will look back on relaying to HTTPS and how the tooling improved.
Compass Security Blog
Offensive Defense
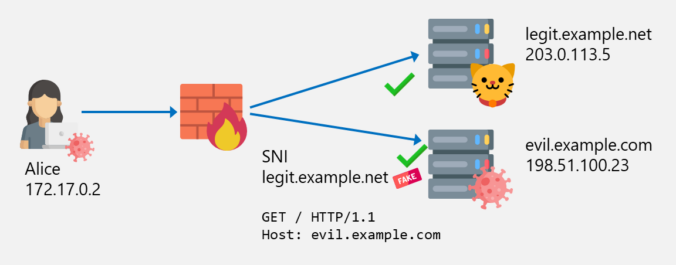
In the previous posts of this series, we looked at different ways to bypass web filters, such as Host header spoofing and domain fronting. As we’ve learned, these techniques can be detected by proxies employing TLS inspection, by checking whether the hostname in the SNI matches the one in the HTTP Host header. If they […]
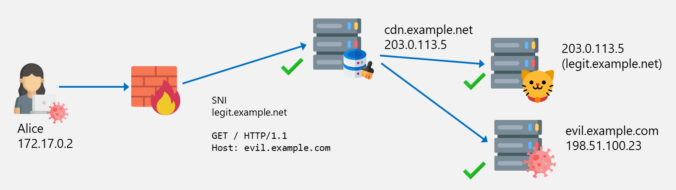
The last two blog posts in this series were about SNI spoofing and Host header spoofing. We also learned that the latter is addressed by some vendors with a technique called “Domain Fronting Detection”. But what exactly is domain fronting? This will be explained in this blog post.
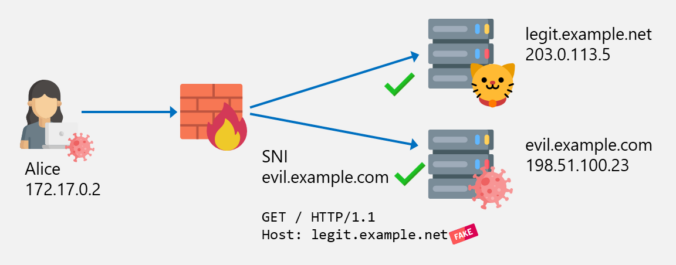
In the last post about bypassing web filters, I discussed how SNI spoofing works and how this can also be prevented by web filters. This post is about another bypass technique called Host Header spoofing.
This is the first part of a series of blog posts about techniques to bypass web filters, looking at increasingly advanced techniques with each part.
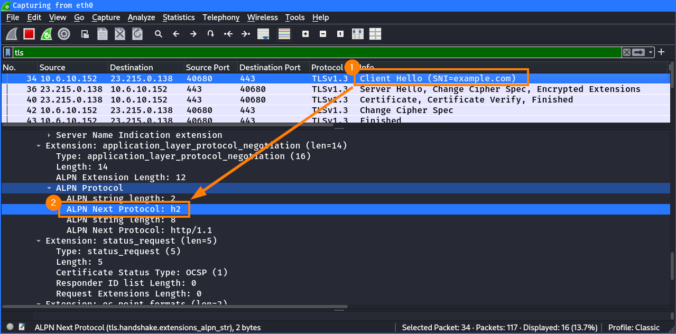
The first part is about how SNI spoofing can be used to bypass web filters.
Secure web communications using HTTPS isn’t anything fancy anymore these days. It ensures traffic from a user to your web application cannot be eavesdropped or tampered with, given it has been set up securely using SSL/TLS. But, do you trust your web application’s code to entirely disregard unencrypted requests? Are you sure your Apache/IIS is […]
© 2026 Compass Security Blog