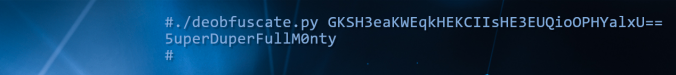
During internal penetration tests or Windows client hardening engagements, we often find configuration files with obfuscated passwords. The post demonstrates a general approach and required tools to effectively make use of such credentials.
Compass Security Blog
Offensive Defense
© 2026 Compass Security Blog