In the previous posts of this series, we looked at different ways to bypass web filters, such as Host header spoofing and domain fronting. As we’ve learned, these techniques can be detected by proxies employing TLS inspection, by checking whether the hostname in the SNI matches the one in the HTTP Host header. If they […]
Compass Security Blog
Offensive Defense
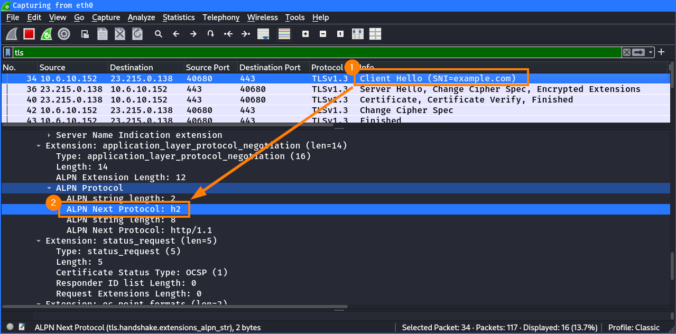
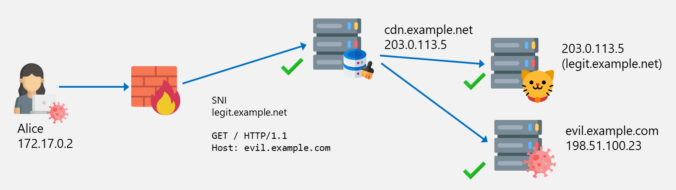
The last two blog posts in this series were about SNI spoofing and Host header spoofing. We also learned that the latter is addressed by some vendors with a technique called “Domain Fronting Detection”. But what exactly is domain fronting? This will be explained in this blog post.
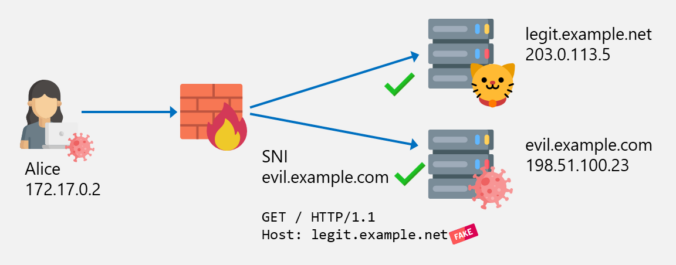
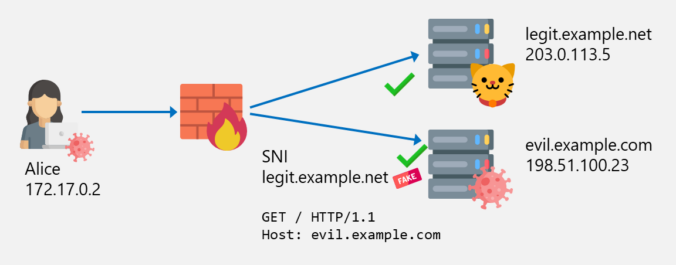
In the last post about bypassing web filters, I discussed how SNI spoofing works and how this can also be prevented by web filters. This post is about another bypass technique called Host Header spoofing.
This is the first part of a series of blog posts about techniques to bypass web filters, looking at increasingly advanced techniques with each part.
The first part is about how SNI spoofing can be used to bypass web filters.
Mozilla created an extensive page [7] concerning the best current choice of SSL/TLS cipher suites, primarily for web servers. Compass Security agrees broadly with the article, but recommends some additional restrictions in order to provide the most resistance against active and passive attacks versus TLS secured connections: Use 3DES cipher instead of RC4 Disable SSLv3 support […]
© 2026 Compass Security Blog