Introduction
The number one form of communication in corporate environments is email. Alone in 2015, the number of business emails sent and received per day were estimated to be over 112 billion [1] and employees spend on average 13 hours per week in their email inbox [2]. Unfortunately, emails are at times also misused for illegitimate communication. Back in the days when the concept of email was designed, security was not the main focus of the inventors and some of the design short comings are still problematic today. The sender rarely uses encryption and the receiver cannot check the integrity of unprotected emails. Not even the metadata in the header of an email can be trusted as an attacker can easily forge this information. Even though many attempts have been made into securing email communication, there are still a lot of unsecured emails sent every day. This is one of the reasons why attackers still exploit weaknesses in email communication. In our experience, a lot of forensic investigations include an attacker either stealing/leaking information via email or an employee unintentionally opening Malware he received via email. Once this has happened, there is no way around a forensic investigation in order to answer key question such as who did what, when and how? Because many corporate environments use Microsoft Exchange as mailing system, we cover some basics on what kind of forensic artifacts the Microsoft Exchange environment provides.
Microsoft Exchange Architecture
In order to understand the different artifacts we first take a look at the basic Microsoft Exchange architecture and the involved components. The diagram below this paragraph shows the architectural concepts in the On-premises version of Exchange 2016. Edge Transport Servers build the perimeter of the email infrastructure. They handle external email flow as well as apply antispam and email flow rules. Database availability groups (DAGs) form the heart of Microsoft’s Exchange environment. They contain a group of Mailbox servers and host a set of databases. The Mailbox servers contain the transport services that are used to route emails. They also contain the client access service, which is responsible for routing or proxying connections to the corresponding backend services on a Mailbox server. Clients don’t connect directly to the backend services. When a client sends an email through the Microsoft Exchange infrastructure, it always traverses at least one Mailbox server.
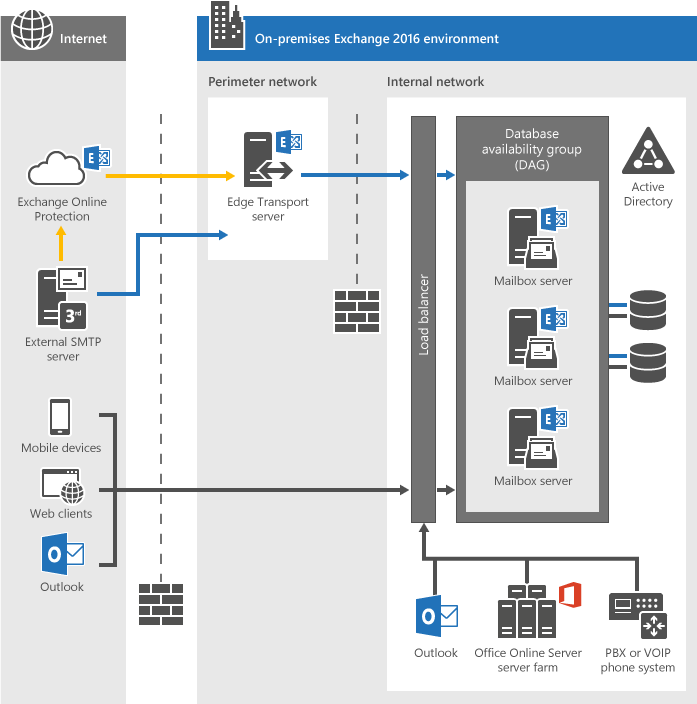 [3] (Exchange 2016 Architecture, Microsoft)
[3] (Exchange 2016 Architecture, Microsoft)
Compliance Features
Microsoft Exchange provides multiple compliance features. Each of those compliance features provides a different set of information to an investigator and it is important to have a basic understanding of their behavior in order to understand which feature can provide answer to which question. The most important compliance features are covered in the following paragraphs.
Message Tracking
The message tracking compliance feature writes a record of all activity as emails flow through Mailbox servers and Edge Transport servers into a log file. Those logs contain details regarding the sender, recipient, message subject, date and time. By default the message tracking logs are stored for a maximum of 30 days if the size of the log files does not grow bigger than 1000MB.
The following example shows the message tracking log entries created when the user “[email protected]” sends a message with the MessageSubject “Meeting” to the user “[email protected]“. Note that in this example both users have their mailboxes on the same server.
EventId Source Sender Recipients MessageSubject
------- ------ ------ ---------- --------------
NOTIFYMAPI STOREDRIVER {}
RECEIVE STOREDRIVER [email protected] {[email protected]} Meeting
SUBMIT STOREDRIVER [email protected] {[email protected]} Meeting
HAREDIRECT SMTP [email protected] {[email protected]} Meeting
RECEIVE SMTP [email protected] {[email protected]} Meeting
AGENTINFO AGENT [email protected] {[email protected]} Meeting
SEND SMTP [email protected] {[email protected]} Meeting
DELIVER STOREDRIVER [email protected] {[email protected]} Meeting
The message content is not stored as part of message tracking logs. By default, the subject line of an email message is stored in the tracking logs, however this can be disabled in the configuration settings. [4]
Single Item Recovery
Single Item Recovery is a compliance feature that essentially allows you to recover individual emails without having to restore them from a full database backup. If a user deletes an email in Outlook, it goes to the “Deleted Items” folder. When the user deletes this email from the “Deleted Items” folder, the email will be placed into the “Dumpster” (soft delete). The following screenshots show how the “Dumpster” can be accessed:
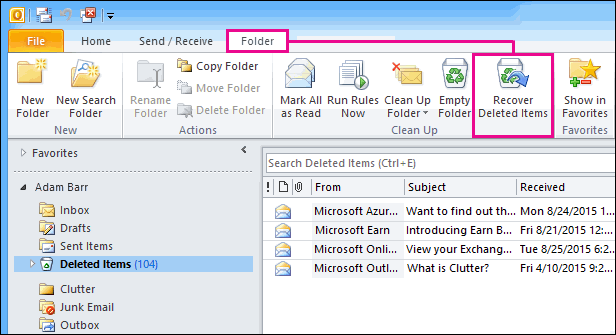 [5] (Recover deleted items in Outlook, Microsoft)
[5] (Recover deleted items in Outlook, Microsoft)
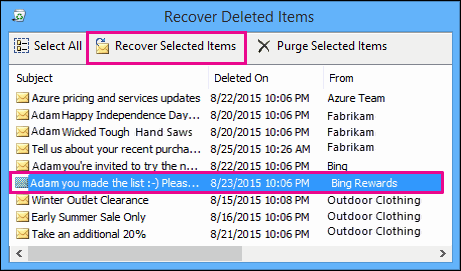
When clicking on the “Recover Deleted Items” trash symbol, the “Dumpster” gets opened as shown on the following screenshot:
[5] (Recover deleted items in Outlook, Microsoft)
From the “Dumpster”, messages can either be recovered or purged completely (hard delete). They can still be recovered if a backup of the mailbox is available of course. When Single Item Recovery is enabled it means that emails remain recoverable for administrators, even if the mailbox owner deletes the messages from the inbox, empties the “Deleted Items” folder and then purges the content of the “Dumpster”. Single Item Recovery is not enabled by default and has to be enabled prior to the date of an investigation. In order to recover a message, the following information is needed [6]:
- The source mailbox that needs to be searched.
- The target mailbox into which the emails will be recovered.
- Search criteria such as sender, recipient or keywords in the message.
With the information above, an email can be found using the Exchange Management Shell (EMS) as shown in the following example.
Search-Mailbox "Alice" -SearchQuery "from:Bob" -TargetMailbox "Investigation Search Mailbox" -TargetFolder "Alice Recovery" -LogLevel Full
In-Place Hold
In-Place Hold can be used to preserve mailbox items. If this compliance feature is enabled, an email will be kept, even if it was purged by a user (deleted from the “Dumpster” folder). Also if an item is modified, a copy of the original version is retained. The In-Place hold is usually activated during investigations in order to preserve the Mailbox content of an individual. The individual do not notice that they are “on hold”. A query with parameters can be used to granularly define the scope of items to hold. By default In-Place Hold is disabled and if neither Single Item Recover nor the In-Place Hold is enabled, an email will be permanently deleted if a user purges (deletes) it from the “Dumpster.
Mailbox Auditing
Mailboxes can contain sensitive information including personally identifiable information (PII). Therefore it is important that it gets tracked who logged on to a mailbox and which actions were taken. It is especially important to track access to mailboxes by users other than the mailbox owner, the so called delegates.
By default mailbox auditing is disabled and when enabled it requires more space on the corresponding mailbox. If enabled, one can specify which user actions (for example, accessing, moving, or deleting a message) are logged per logon type (administrator, delegate user, or owner). Audit log entries also include further important information such as the client IP address, host name, and processes or clients used to access the mailbox. If the auditing policy is configured to only include key records such as sending or deleting items there is no noticeable impact in terms of storage and performance.
Administrator Auditing
This compliance feature is used to log changes that an administrator makes to the Exchange Server configuration. By default, the log files are enabled and kept for 90 days. Changes to the administrator auditing configuration are always logged. The log files are stored in a hidden dedicated mailbox which cannot be opened in Outlook or OWA.
Others
Exchange email flow rules, also known as transport rules can be used to look for specific conditions in messages that pass through an Exchange Server. Those rules are similar to the Inbox rules, a lot of email client’s offer. The main difference between an email flow rule and a rule one would setup in an email client is that email flow rules take action on messages while they are in transit, as opposed to after the message is delivered. Further, email flow rules have a richer set of conditions, exceptions as well as actions, which provide the flexibility to implement many types of messaging policies. [7]
Journaling allows recording a copy of all email communications and sending it to a dedicated mailbox on an Exchange Server. Archiving on the other hand can be used to backup up data, removing it from its native environments and store a copy on another system. Finally there is always the option of a full backup of an Exchange database. This creates and stores a complete copy of the database file as well as transaction logs.
Summary
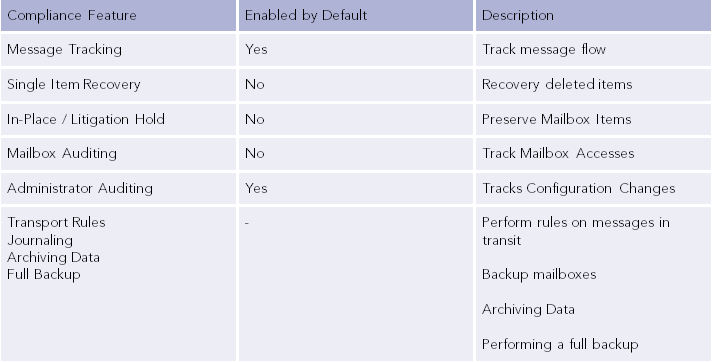
As we have seen, Microsoft Exchange provides various compliance features that help during forensic investigations involving email analysis. Having an understanding of which artifacts are available is key. The following table summarises the compliance features discussed in this post:
Courses and Beer-Talk Reference
In order to directly share our experience in this field we choose “Exchange Forensics” as topic for our upcoming beer talks. Don’t hesitate to sign up if you are interested. For more information click on the link next to the location you would like to attend:
- Berlin 5. September 2016 https://www.compass-security.com/en/agenda/calendar-detail/beer-talk-zum-thema-exchange-forensic-in-berlin/
- Jona 8. September 2016 https://www.compass-security.com/en/agenda/calendar-detail/beer-talk-zum-thema-exchange-forensic-in-jona/
- Bern 15. September 2016 https://www.compass-security.com/en/agenda/calendar-detail/beer-talk-zum-thema-exchange-forensic-in-bern/
If you like to dive even deeper, we provide the Security Training: Forensic Investigations. It covers:
- Introduction to forensic investigations
- Chain of custody
- Imaging
- Basic of file systems
- Traces in slack space
- Traces in office documents
- Analysis of windows systems
- Analysis of network dumps
- Analysis of OSX systems
- Analysis of mobile devices
- Forensic readiness
- Log analysis
If you are interested please visit our “Security Trainings” section to get more information: https://www.compass-security.com/services/security-trainings/kursinhalte-forensik-investigation/ or get in touch if you have questions.
Sources and References:
[0] E-mail Forensics in a Corporate Exchange Environment, Nuno Mota, http://www.msexchange.org/articles-tutorials/exchange-server-2013/compliance-policies-archiving/e-mail-forensics-corporate-exchange-environment-part1.html
[1] Email-Statistics-Report-2015-2019, The Radicati Group, Inc., http://www.radicati.com/wp/wp-content/uploads/2015/02/Email-Statistics-Report-2015-2019-Executive-Summary.pdf
[2] the-social-economy, McKinsey & Company, http://www.mckinsey.com/industries/high-tech/our-insights/the-social-economy
[3] Exchange 2016 Architecture, Microsoft, https://technet.microsoft.com/de-ch/library/jj150491(v=exchg.160).aspx
[4] Message Tracking, Microsoft, https://technet.microsoft.com/en-us/library/bb124375(v=exchg.160).aspx
[5] Recover deleted items in Outlook, Microsoft, https://support.office.com/en-us/article/Recover-deleted-items-in-Outlook-2010-cd9dfe12-8e8c-4a21-bbbf-4bd103a3f1fe
[6] Recover deleted messages in a user’s mailbox, Microsoft, https://technet.microsoft.com/en-us/library/ff660637(v=exchg.160).aspx
[7] Mail flow or transport rules Microsoft, https://technet.microsoft.com/en-us/library/jj919238(v=exchg.150).aspx
Leave a Reply