What is a Hack-Lab?
Compass Security provides a monthly playful occasion for the security analysts to get-together and try to hack new devices, dive into current technologies and share their skills with their fellows.
Topics
The following topics, tools and technology has been discussed during this Hack-Lab:
- ESPloitation,
- Kubernetes,
- BACnet analysis,
- DNS Attacks and Hardening,
- Multi-SDR
Wrap-Up
Topic #1 – ESPloitation
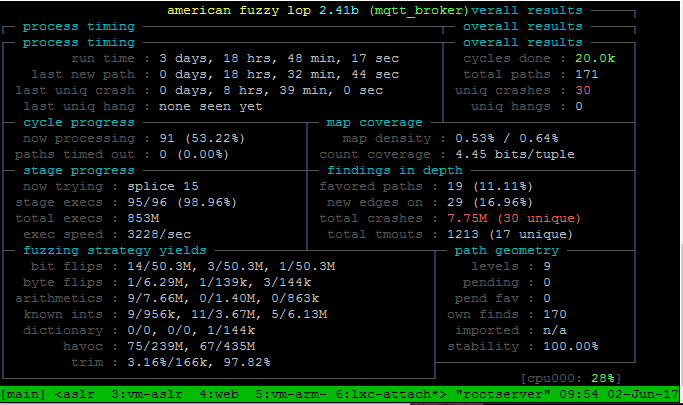
Dobin Rutishauser has given an overview of the Xtensa microcontroller architecture. Our team analysed and discussed several design decisions which have an influence on memory corruption exploitation on this platform. At the same time we improved the corresponding internal whitepaper and slides about this topic. At the end Dobin performed fuzzing on the MQTT broker of an IoT framework for this platform, with promising results. This is part of an ongoing long-term project, where the results will be published separately.
Involved Technologies
- Whiteboard
- Xtensa / ESP32 architecture manual
- American Fuzzy Lop (AFL)
Topic #2 – Kubernetes
The goal of this topic was to get an overview over the current options to quickly set up a Kubernetes cluster and orchestrating a simple application. As there is a vast amount of different guides – quite a few are outdated and result in an insecure cluster – tools and components available, we had to concentrate on the more recent options and decided to go for the following three approaches:
- Manually setting up a production-grade cluster from scratch
- Setting up a single node development instance using Minikube
- Using Kubernetes Operations (kops) to set up an instance on Amazon Web Services (AWS)
Involved Technologies
- Kubernetes
- Docker
- Virtualization
- Amazon Web Services (AWS)
Topic #3: BACnet Analysis
Testing of BACnet IP related software for vulnerability analysis. Additionally we checked a smart meter for BACnet IP flaws. Evaluated the detection of BACnet-enabled devices via NMAP NSE scripts.
Involved Technologies
- BACnet IP
Topic #4 – DNS Attacks and Hardening
Analysts elaborated several hardening and configuration guidelines to protect latest DNS software products (BIND9) against popular DNS attacks such as:
- Cache Poisoning / Cache Snooping
- Reflection / Amplification Attacks
- Resource Utilization (DoS) Attacks
- Leakage of sensitive internal Information
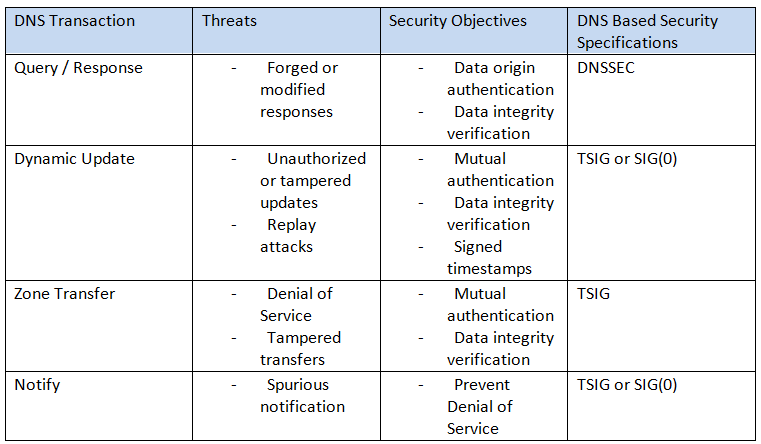
Further, advanced recommendations to secure different types of DNS transactions have been formulated to prevent the above attacks. An overview thereof is summarized in the table below:
Source: Secure Domain Name System (DNS) Deployment Guide, Ramaswamy Chandramouli, Scott Rose (http://dx.doi.org/10.6028/NIST.SP.800-81-2)
Topic #5: Multi-SDR
GNU Radio PMR 446: After some radio demodulation problems in the virtual machine, I switched to the host system. This solved the problems.
I demodulated successfully eight PMR 446 (walkie talkie) channels simultaneous to eight different WAV files.
Leave a Reply