JSON Web Token, or more commonly known as JWT, is an open standard [1] that defines a compact and self-contained structure for securely transmitting information between multiple parties. The contained information can be verified and trusted through digital signatures. JWTs can be integrity protected using a secret using the HMAC algorithm or a public / private key pair using RSA / EC signature algorithms.
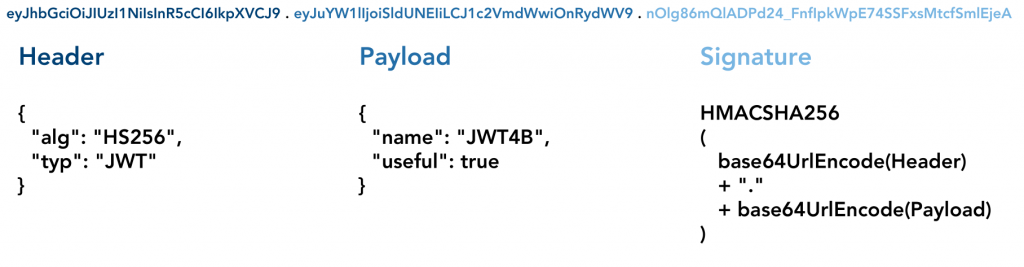
JWTs consist of three different segments which are separated by a dot. The first two segments are Base64 encoded JSON arrays containing multiple values, the signature is created over both header and payload.
Testing for JWT vulnerabilities is time consuming, as up till now when using Burp Suite [2], the transmitted tokens had to be decoded, manipulated, encoded (by a third-party tool such as the website JWT.IO [3] ) and inserted back into Burp Suite. Next to the time overhead needing a separate tool that does not integrate well, JWTs might have a limited validity which requires the necessary steps to be performed very fast.
Therefore, two Compass employees developed an extension for Burp Suite during the Hack-Labs [4] provided by Compass. This extension automates most of the steps, which are necessary for testing JWT in a time effective manner.
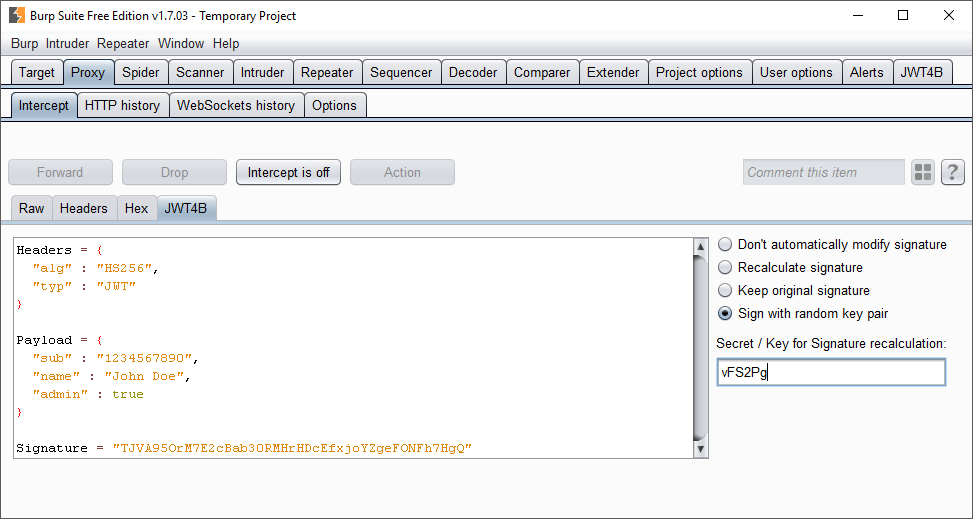
The extension, called JWT4B (JWT for Burp), supports the penetration tester with the following tasks:
- Intercepting of requests and responses
- Manipulation of payload
- Changing of algorithm
- Resigning JWTs
- Decoding of JWTs in the history view
- Integrity verification
- Dedicated tab for tokens that are not transferred through the authorization header
Download and Sources
The most recent versions as well as the source code can be found on the projects GitHub repository
Furthermore, the plugin is also available through the BApp Store as “JSON Web Tokens“.
Screenshots
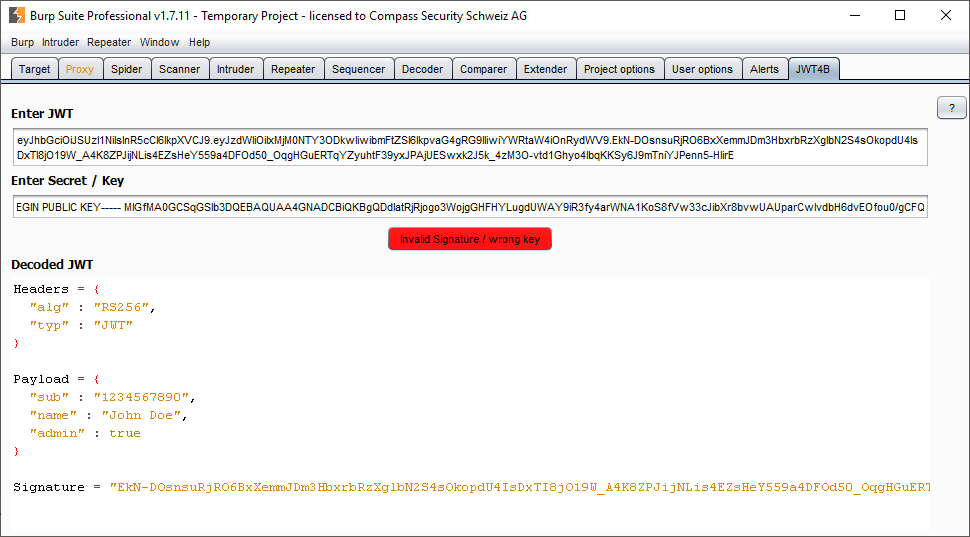
JWT4B – Suite Tab – Allowing to manually enter JWTs or by selecting text and using the custom context action
References:
[1] – https://tools.ietf.org/html/rfc7519
[2] – https://portswigger.net
[3] – https://jwt.io
[4] – https://blog.compass-security.com/2017/01/wrap-up-hack-lab-1-2017/

Leave a Reply