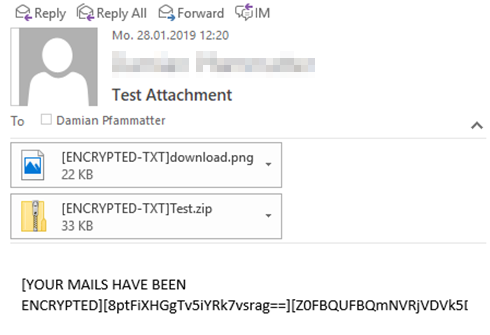
Ransomware focuses on encrypting data on a filesystem-level, either locally on infected client systems or remotely on accessible file servers. However, what if ransomware would start encrypting data on an application-level too?
Compass Security Blog
Offensive Defense
Contents Introduction Background Story External Device Access Auditing with Windows Security Event Logs Audit Plug and Play Activity Audit Removable Storage Activity External Device Access Auditing with Default Windows Artifacts Other Ways to Monitor External Device Usage Conclusion References Introduction Have you ever investigated a data leakage case involving a suspect potentially leaking data to […]
Contents Introduction Attack Overview Step-by-Step Detection Email Clients Administration Tools Exchange Compliance Features MAPI Editor Eradication Microsoft Security Response Center Swiss Cyber Storm 2018 Conclusion References Introduction In recent investigations, Compass recognized a raise in popularity for attackers to compromise Microsoft Exchange credentials. As one of the first steps after having obtained the credentials (most […]
Ein Hintegrundartikel zur SRF Einstein Sendung vom Donnerstag, 3. September 2015 um 21:00 Uhr zum Thema “Cybercrime, wie sicher ist das Know-how der Schweiz”. (Trailer online) In diesem Artikel zeigen wir Ihnen die Vorgehensweisen von Angreifern auf, die versuchen unerlaubten Zugriff auf fremde Systeme zu erlangen — beispielsweise im Netzwerk eines KMUs. Schematisch sind diese Vorgehensweisen […]
Nowadays, a growing list of XSLT processors exist with the purpose of transforming XML documents to other formats such as PDF, HTML or SVG. To this end such processors typically offer a powerful set of functionalities – which, from a security point of view, can potentially pose severe risks. Within this post, we highlight some […]
© 2026 Compass Security Blog