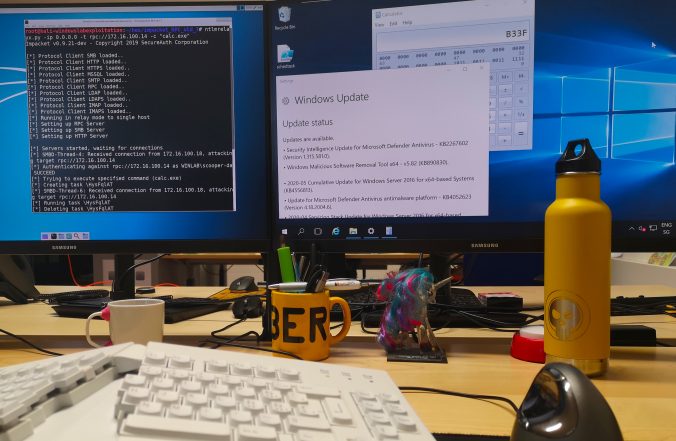
A little bit over a year ago, I wrote an article on this blog about CVE-2020-1113 and how it enabled to execute code on a remote machine through relaying NTLM authentication over RPC triggering a scheduled task on the remote system. History repeats itself and a vulnerability of the same category has been fixed by Microsoft in June this year.
Compass Security Blog
Offensive Defense
Page 2 of 2
Since a few years, we – as pentesters – (and probably bad guys as well) make use of NTLM relaying a lot for privilege escalation in Windows networks.
In this article, we propose adding support for the RPC protocol to the already great ntlmrelayx from impacket and explore the new ways of compromise that it offers.
This vulnerability was discovered by Compass Security in January 2020, disclosed to Microsoft Security Response Center and assigned CVE-2020-1113 as identifier.
As a defender, you want to find and patch attack paths in your Active Directory environment. One cannot easily spot issues by looking at the Active Directory Users and Computers console, GPOs, etc. but here comes BLOODHOUND.
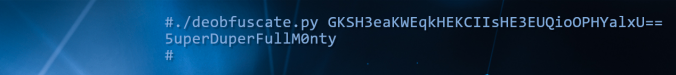
During internal penetration tests or Windows client hardening engagements, we often find configuration files with obfuscated passwords. The post demonstrates a general approach and required tools to effectively make use of such credentials.
When attackers try to access confidential data, to steal money or simply to disrupt a business, they will often look for the weakest link to get inside a target network. In some case, this might be an outdated system exposed to the internet or an easy physical access to the network but quite often, the […]
The goal in the Capscii challenge was to solve 50 captchas consecutively in less than 100 seconds and prove that we are not human. The captcha was not your usual recognition of text though, it consisted of an operation (addition, subtraction or multiplication) on two numbers. Only problem, the numbers were printed as ASCII art on […]
© 2026 Compass Security Blog