When attackers try to access confidential data, to steal money or simply to disrupt a business, they will often look for the weakest link to get inside a target network. In some case, this might be an outdated system exposed to the internet or an easy physical access to the network but quite often, the easiest will be to go through the company’s own employees.
Inadvertent insiders were responsible for more than twothirds of total records compromised in 2017.
https://www.ibm.com/security/data-breach/threat-intelligence
There are several ways to abuse the trust of an employee in order to get access to data or a network. One can drop infected USB drives in the company’s parking lot or call employees to convince them to download and execute a malicious file from the internet. However, the vector of choice to reach a company through its employee remains the email.
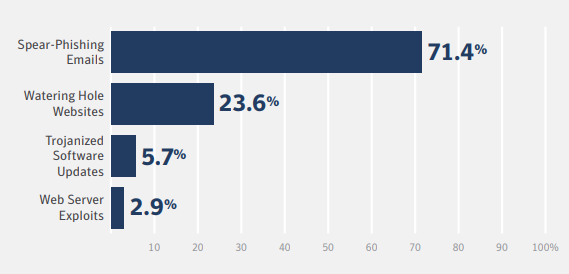
In 2017, 71.4 percent of targeted attacks involved the use
of spear-phishing emails.https://www.symantec.com/security-center/threat-report
Attacks also become more and more advanced and can be targeted towards a specific industry or company. The Anti-Phishing Working Group (APWG) reported more than 250 thousand attacks in 2016 using 195 thousands unique domains. It does not stop at the swiss borders unfortunately as the Reporting and Analysis Centre for Information Assurance (MELANI) reported 2501 phishing websites in the first half of 2018.
There are two fronts on which IT Security professionals have to battle in order to prevent an attack:
- Infrastructure – Filtering content using a Web Gateway, Sandboxing any incoming active attached documents, keeping every piece of software up to date and monitoring suspicious activities
- Awareness – Teaching users to recognize and report social engineering attempts.
Unfortunately, having the best infrastructure in the world does not prevent a tailored phishing attack. This blog post focuses on how one can improve awareness through staged phishing attacks followed by immediate awareness training.
Raising awareness
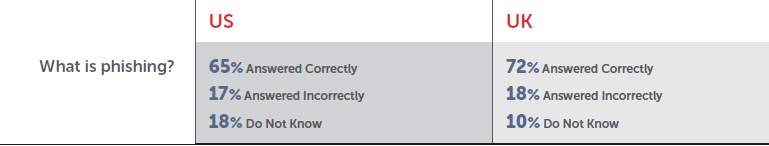
https://www.wombatsecurity.com/state-of-the-phish
There exist different methods to try and raise awareness. In many companies, some kind of training will be given to new employees about the policies and security measures in place. Further, some providers offer great online trainings (wombatsecurity.com or phishme.com, they also have nice infographics), which can be performed regularly in order to reactivate this knowledge. Finally, you can opt for a staged social engineering attack to assess the risk in your company. This is nicely combined with a debriefing presentation where the results of the tests are shown and the security measures are one more time explained.
Our rationale is:
- Spread-out the learning – that one e-learning that your employee did 2 years ago is not going to help against today’s targeted and advanced attack
- Vary teaching method – as for any learning, the facts that get repeated under different form are better assimilated
- Learn through personal experience – it may be easier to understand the actual risk when caught red-handed
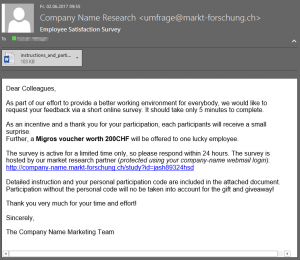
A not too good phishing campaign
The idea is to perform a phishing attempt where some elements can be recognized by the employees as phishy. In the following example e-mail, many elements hints that it might not be legit:
- The sender is unknown
- There’s an urgency to open the attached document
- A link to a login page
- The mail content appeal to one’s emotions by offering a reward and a threat
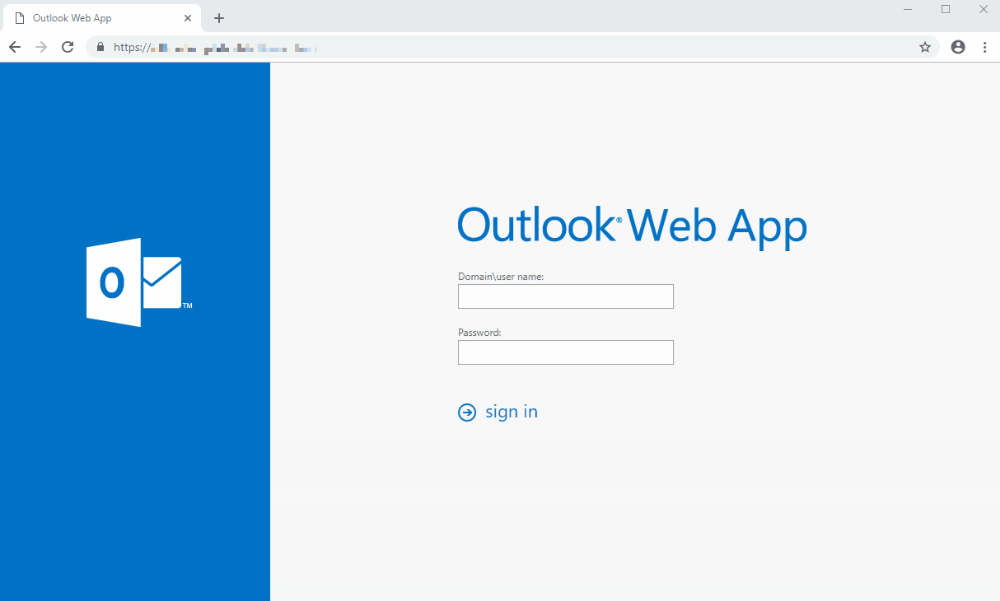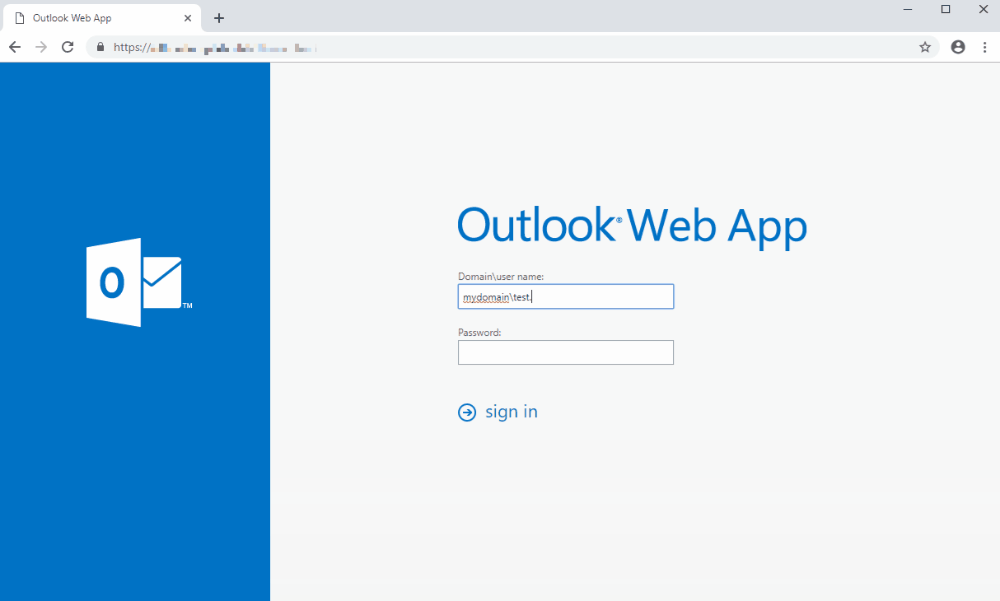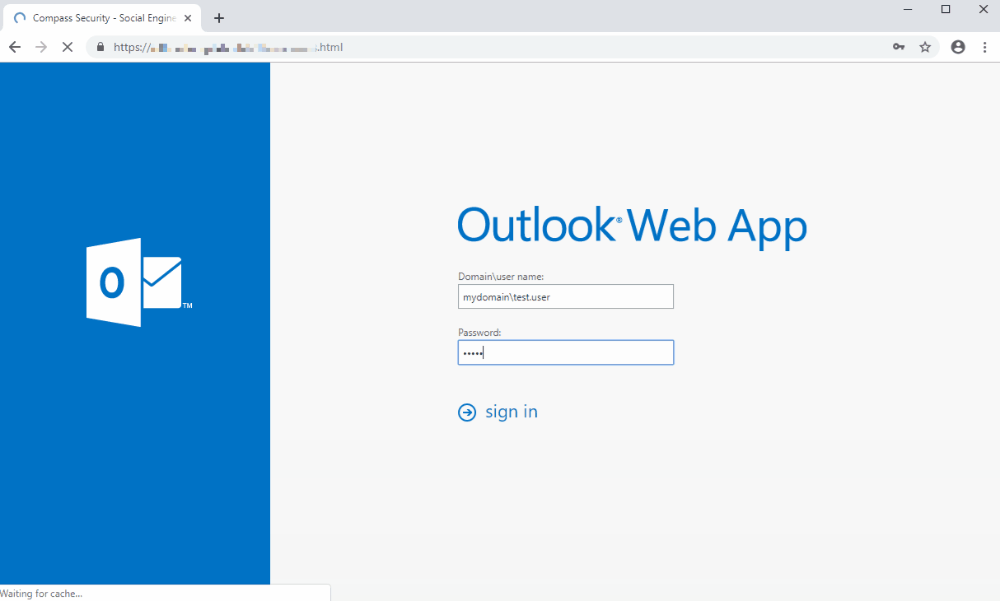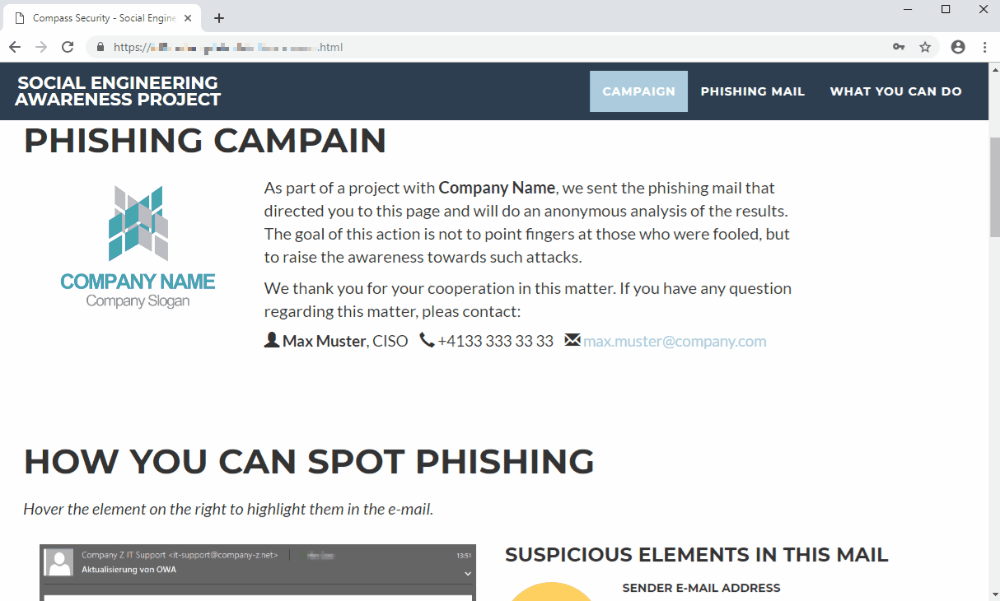
These e-mail can be sent in mass from a bought phishing domain or sent with a spoofed e-mail address. One typically want to gather information from people who entered login information or executed the malicious document in order to get numbers on the attack. Finally comes the time to communicate about the phishing and one need to be careful about how things are explained so that the information is taken seriously and people don’t feel betrayed.
A good awareness communication
From our experience, the following points are key to a good post-phishing-test awareness communication:
- Explain what happened
- Teach about phishing
- Clarify the employee’s expected behavior
- Optionally: Ask for feedback
Explaining what happened
You need to break it to the people that 50% of the employee got caught in the phishing attempt. Many are going to feel hurt or betrayed and many other are going to think “it wasn’t me”. The key elements below can help to explaining what happened:
- The whole thing was a test organized by the security team
- No credentials were stolen, no workstation infected, all statistics recorded are anonymous
- Explain what a real attacker could have done with the stolen credentials / remote access to a workstation.
Tip: give a phone number or an internal document reference to allow the authenticity of the communication to be verified
Teach about phishing
It is convenient to have an example phishing at hand where people got caught to explain the elements to be aware of. Using the real-life example of the staged phishing, explain how employees should be aware of:
- Technical elements:
- Unexpected e-mail address
- Attached document
- Link to a (login) page
- Textual content:
- Tone and wording (language mistakes, etc)
- Signature and salutations
- Emotions raised:
- Urgency
- Fear
- Curiosity
- Greed
Clarify the expected behavior
The user should learn what to do next time something strange happens, when it is not a test:
- Give contact details for the SOC
- Don’t try to analyze any file or suspicious content
- Spread the word that phishing has been received
Optionally: Ask for feedback
It might be interesting to ask what lead the employees to click on a malicious link / open a malicious file. For example you might want to ask:
- Did you notice anything unusual in the mail
- What reason lead you to click
- How do you feel about security at the office/at home
- Knowledge about phishing / IT
- Age/department
Combining Phishing and Awareness Communication into an Effective Awareness Training
Lately we combined the phishing campaigns with a direct awareness feedback and it proved to be efficient. Here’s how we did it:
In this example, the user gets an e-mail warning him that he needs to connect to his webmail if he doesn’t want to lose all his data.
Upon logging in and before he even had time to type his complete password, the user gets redirected to our awareness page where he can learn what happened and how to prevent it in the future.
Conclusion
We’ve proposed a new way to spread awareness after a phishing assessment. Although we don’t have enough data to show trends, we claim this method is effective and leads to awareness being significantly raised. Furthermore, feedback from the victim is positive.
Training
If you are interested to learn more about Phising, Vishing, SMShing, Baiting, Pretexting, OSINT, and Social Engineering in general – then join us for the upcoming training in Zurich (German spoken).
Leave a Reply