During Business Email Comproise (BEC) engagements we often have to analyze the provenance of emails. According to the FBI’s Internet Crime Report, BEC is one of the most financially damaging attacks, even surpassing ransomware in terms of losses. But how can we know all of this? Through email headers! This blog post tries to shed some light on the information contained within emails, what it means, and what can be done to prevent this type of attack.
Compass Security Blog
Offensive Defense
Page 4 of 29
Given the explosion of development and interest in deep learning models in the past year, we decided to research on the topic to increase our know-how and find applications where these technologies can be leveraged in offensive security engagements.
This posts explores the use of machine learning for voice cloning and how it can be used for social engineering.
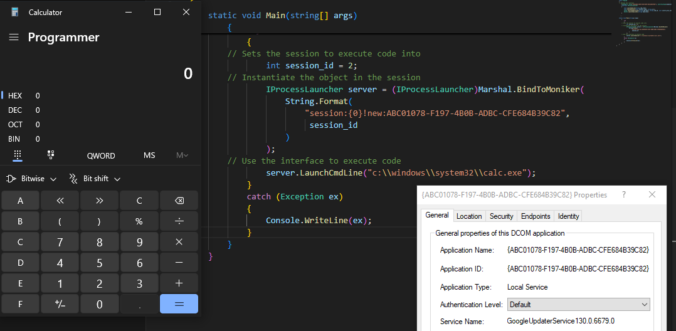
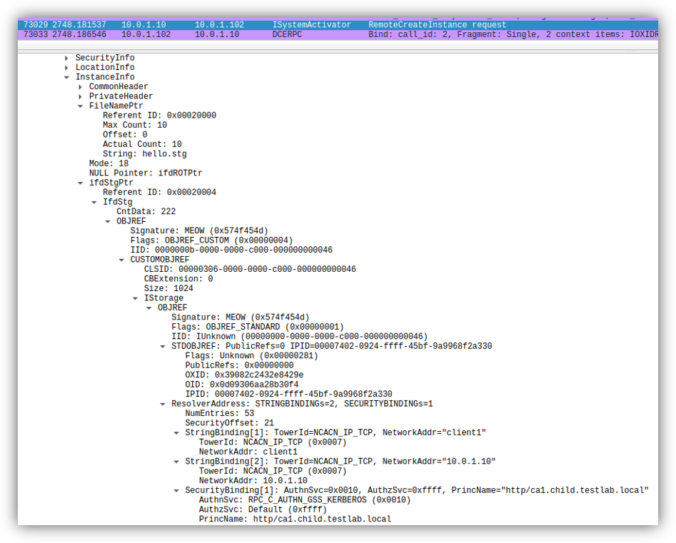
Once again, reading blogs and tweets from James Forshaw led me to wonder how things work. This time, I was working on DCOM for my last blog post and while reading about cross-session activation, I had trouble believing what I was reading.
Earlier this year, several security researchers published research about using DCOM to coerce Windows systems to authenticate to other systems. This can be misused to relay the authentication to NTLM or Kerberos, to AD CS over HTTP for instance. This sounds like a hot and complex topic. Let’s take a look back how this started […]
Bug bounty programs have evolved into a critical element of modern cybersecurity. In this post, we give some answers to how bug bounty programs can attract students as hunters.
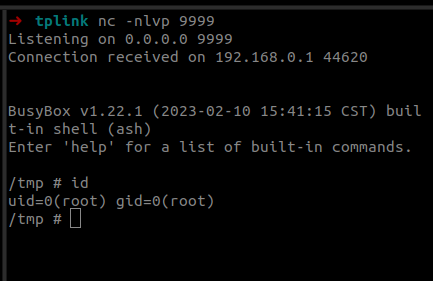
Last year we participated in the Pwn2Own 2023 Toronto competition and successfully exploited the Synology BC500 camera. The DEVCORE Internship Program team managed to exploit a bug in the TP-Link Omada Gigabit VPN Router. So I was naturally curious and wanted to figure out how difficult it would be to recreate that exploit having access only to a high-level bug description and the firmware.
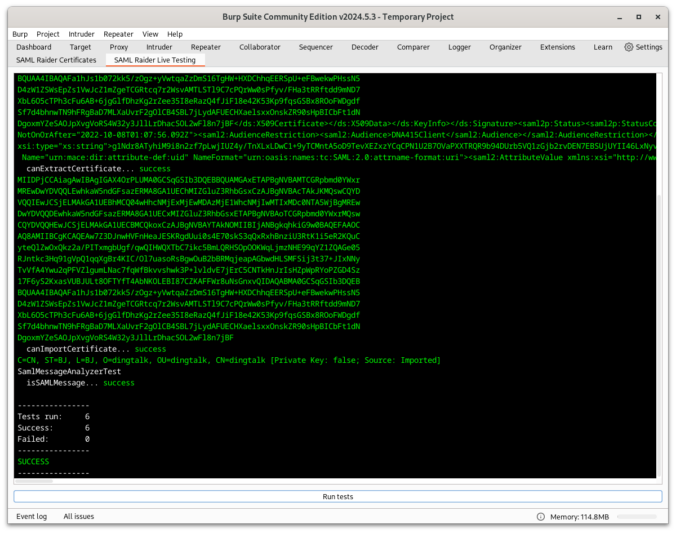
SAML Raider is a Burp Suite extension and the tool of choice for many pentesters for testing SAML infrastructures. This blog post should give a brief introduction to what has changed in the new version 2.0.0. From Improving developer and user experience to bug fixes.
TL;DR Release of Conkeyscan – A Confluence Keyword/Secret Scanner, which is tailored towards pentesters. Secrets Everywhere Many companies, especially larger ones, need to store knowledge in a centralized way. A wiki is the usual choice for this. One product that is frequently used for this purpose is Confluence from Atlassian. Similar to how sensitive data […]
To identify and understand threats and weaknesses of smart contracts, it is important to be at least familiar with common smart contract bugs and vulnerabilities, how they can be leveraged by a malicious attacker, and how these issues can be mitigated.
This blog article aims to raise awareness about common smart contract vulnerabilities and their corresponding mitigation strategies.
Introduction Last year, I attended a job fair organized by the Association of Computer Science Students at ETH Zürich. It was a rewarding experience to be able to share my day-to-day work in a field I am so passionate about. We got to talk to numerous students at different stages of their studies, as well […]
© 2026 Compass Security Blog